When you develop new software, there are several types of testing that code be done to check your code. Unit testing, integration testing, acceptance testing, etc. An important type of testing that should be incorporated into your development cycle is Static Code Analysis or sometimes referred to as Static Application Security Testing (SAST)
What is SAST
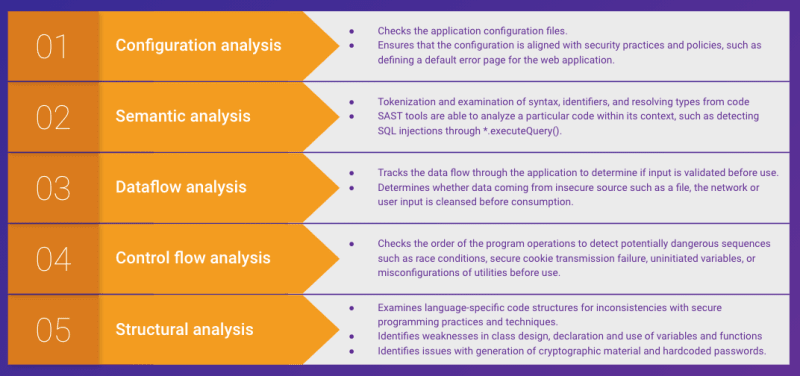
SAST (Static Application Security Testing) play an important part in security testing. It can be used to identify potential security vulnerabilities in codebases before they are deployed into production environments. Since going through the code manually may not be sufficient to sniff all the potential vulnerabilities out, SAST tools are utilized to carry out this operation, quickly and even some could recommend fixes.
SAST tools work by scanning the source code of an application for potential vulnerabilities, such as SQL injection or buffer overflow vulnerabilities, by analyzing the code structure and identifying patterns that may be associated with vulnerabilities. This identification, especially when done early in the development process, can help developers and security teams address these vulnerabilities before they are deployed into production environments, reducing potential security risks, increasing compliance with relevant security standards and regulations.
And this is where CodeQL comes into play.
What is CodeQL?
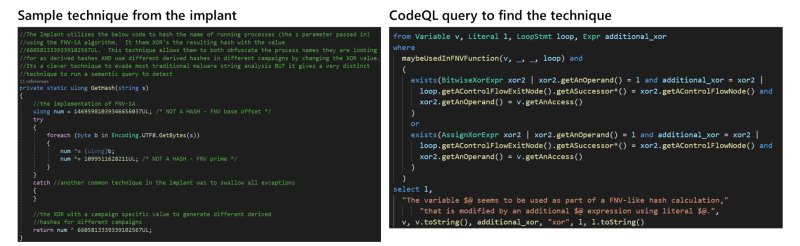
CodeQL is a semantic code analysis engine that allows developers to write queries to analyze codebases. When reviewing a codebase, some people would review the code manually or try to use regex (or negative regex), this however can miss a few things.
CodeQL analyzes codebases by breaking down the code into a graph of interrelated objects and relationships. The created graph is then used to execute queries that traverse the objects and relationships to identify potential security vulnerabilities. One thing to note is that because CodeQL creates a graph representation of the codebase, which can be computationally expensive for large codebases.
CodeQL is a powerful tool for automating code analysis and finding security vulnerabilities in software. It has already been used to identify and remediate many high-profile security vulnerabilities in open source software, including the infamous SolarWinds hack.
How does CodeQL work?
CodeQL works by analyzing codebases and building a graph of interrelated objects and relationships. The graph is then used to execute queries that traverse the objects and relationships to identify potential security vulnerabilities. CodeQL supports a wide range of programming languages, including C/C++, Java, JavaScript, Python, and more.
To use CodeQL, developers write queries in a declarative language called QL which stands for Query Language. It is used to write queries that traverse the graph of interrelated objects and relationships. The rationale behind this design is to be easy to learn and use, making it accessible to developers of all experience levels.
Use cases for CodeQL
CodeQL has a wide range of use cases, from identifying security vulnerabilities in open source software to analyzing codebases for compliance with coding standards. Here are some of the most common use cases for CodeQL:
- Security Vulnerability Analysis: CodeQL can be used to identify security vulnerabilities in software. By analyzing the codebase and identifying potential security vulnerabilities, CodeQL can help developers remediate these vulnerabilities before they can be exploited by attackers.
- Compliance Analysis: CodeQL can also be used to analyze codebases for compliance with coding standards and regulations. By analyzing the codebase and identifying areas where it does not comply with coding standards, CodeQL can help developers bring the codebase into compliance.
- Code Quality Analysis: CodeQL can also be used to analyze code quality. By analyzing the codebase and identifying areas where the code quality can be improved, CodeQL can help developers improve the overall quality of the codebase.
- Bug Hunting: CodeQL can also be used for bug hunting. By analyzing the codebase and identifying potential bugs, CodeQL can help developers find and fix bugs before they can cause problems. (Check out LiveOverflow's video on using CodeQL)
Advantages of CodeQL
CodeQL has several advantages over other code analysis tools. Here are some of the most significant advantages of CodeQL:
- Declarative Language: Uses a declarative language called QL, which is designed to be easy to learn and use. This makes it accessible to developers of all experience levels.
- Cross-Linguistic Support: Supports a wide range of programming languages, including C/C++, Java, JavaScript, Python, and more. This makes it a versatile tool for analyzing codebases written in different languages.
- Graph-Based Analysis: Uses a graph-based analysis approach that allows for a more comprehensive analysis of the codebase. This approach allows CodeQL to identify potential security vulnerabilities that might be missed by other code analysis tools.
Conclusion
CodeQL is a powerful tool for automating code analysis and finding security vulnerabilities in software. It uses a declarative language called QL to analyze codebases and identify potential security vulnerabilities. CodeQL supports a wide range of programming languages and uses a graph-based analysis approach that allows for a more comprehensive analysis of the codebase.
CodeQL has several advantages over other code analysis tools, including its declarative language, cross-linguistic support, and graph-based analysis approach. These advantages make CodeQL a versatile and effective tool for analyzing codebases and identifying potential security vulnerabilities.
If you are a developer looking to improve the security and quality of your codebase, CodeQL is definitely worth exploring. With its powerful analysis capabilities and easy-to-use interface, CodeQL can help you identify and remediate potential security vulnerabilities before they can be exploited by attackers.
References
https://www.microsoft.com/en-us/security/blog/2021/02/25/microsoft-open-sources-codeql-queries-used-to-hunt-for-solorigate-activity/
https://codeql.github.com/docs/codeql-overview/supported-languages-and-frameworks/
https://learn.microsoft.com/en-us/windows-hardware/drivers/devtest/static-tools-and-codeql


Top comments (0)