When architecting services across multiple AWS accounts—especially in a bulkhead architecture—enabling secure service-to-service communication is crucial. A Private API Gateway is often used to keep internal APIs accessible only within a VPC, but what if you need external access?
A Regional API Gateway with an authorizer (e.g., Lambda Authorizer) can act as a single-entry point for multiple private endpoints. This article demonstrates how to securely connect a Public Regional API Gateway in one AWS account (Account A) to a Private API Gateway in another AWS account (Account B), using:
✅ VPC Link to securely route traffic to internal services
✅ Network Load Balancer (NLB) to distribute traffic efficiently
✅ VPC Endpoint to expose the Private API Gateway securely
🏗 Prerequisites
Before starting, ensure you have:
- Two AWS accounts (Account A & Account B)
- VPC networking in both accounts with Transit Gateway (TGW) connectivity
📌 Architecture Overview
The diagram below illustrates the integration:
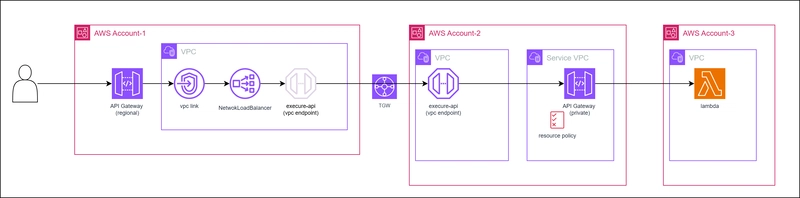
Key Components:
1️⃣ Private API Gateway (Account B) – Hosts internal APIs, accessible via a VPC Endpoint
2️⃣ Network Load Balancer (NLB) (Account A) – Routes traffic from the Public API Gateway to the Private API Gateway
3️⃣ VPC Link (Account A) – Connects the Public API Gateway to the NLB
4️⃣ Regional API Gateway (Account A) – Exposes the Private API securely to external users
Lets Get started !
🏗 Step 1: Create a Private API Gateway & VPC Endpoint (Account B)
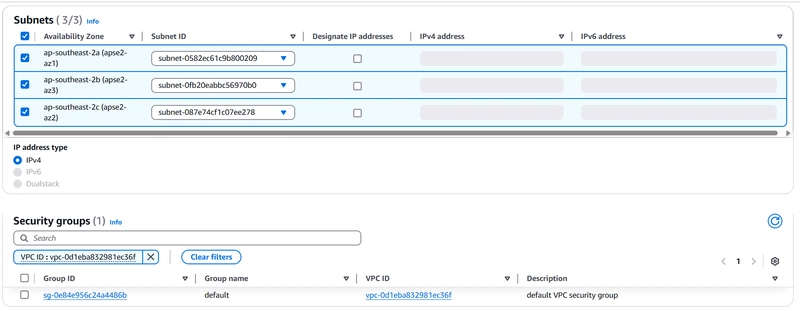
1️⃣ Log into Account B and navigate to VPC Endpoints
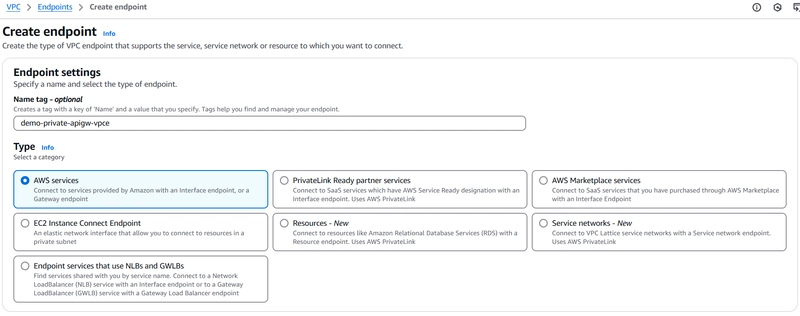
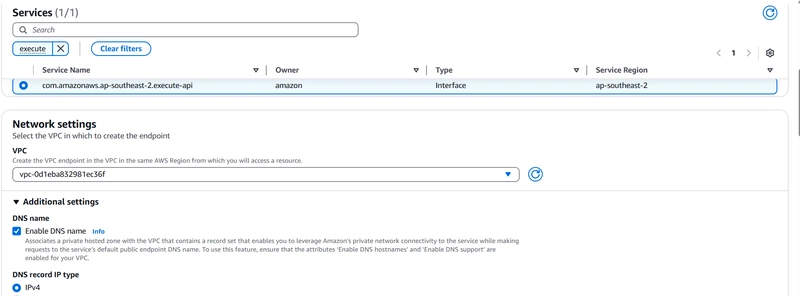
2️⃣ Create a new VPC Endpoint:
VPC: Select the VPC where the Private API Gateway resides
Security Group: Allow inbound traffic from Account A
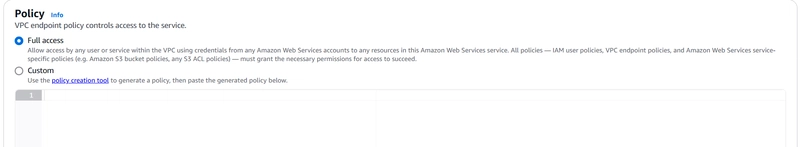
Policy: Set to Full Access for now
Then click create. Will take few minutes to status to become available.
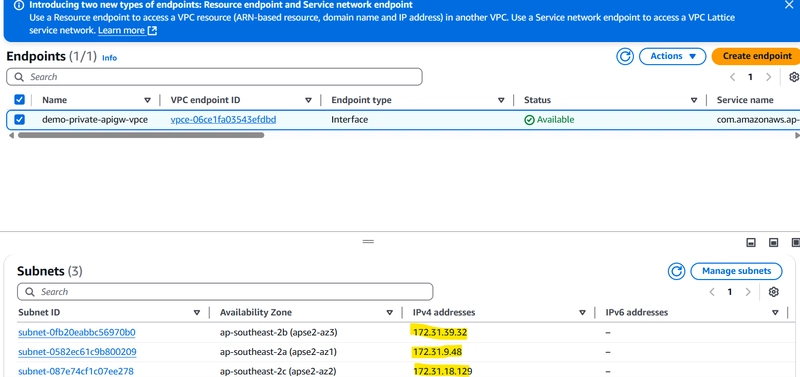
3️⃣ Once created, note down the IP addresses of the VPC Endpoint
Step 2: Create a Private API Gateway (Account B)
1️⃣ Log into Account B and navigate to API Gateway
Select rest api private.
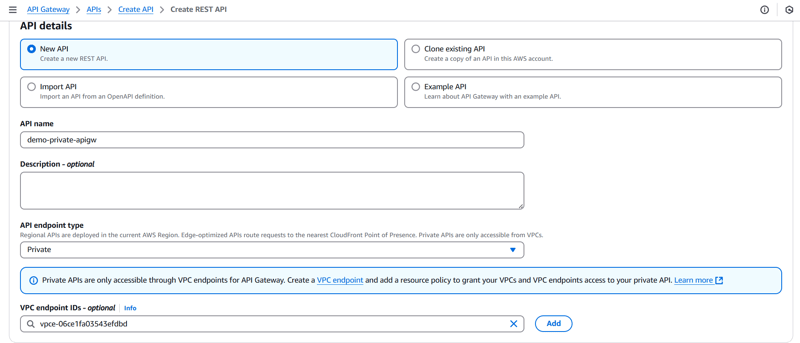
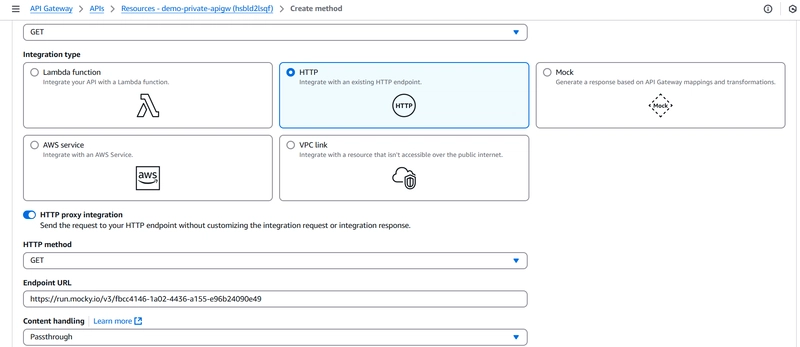
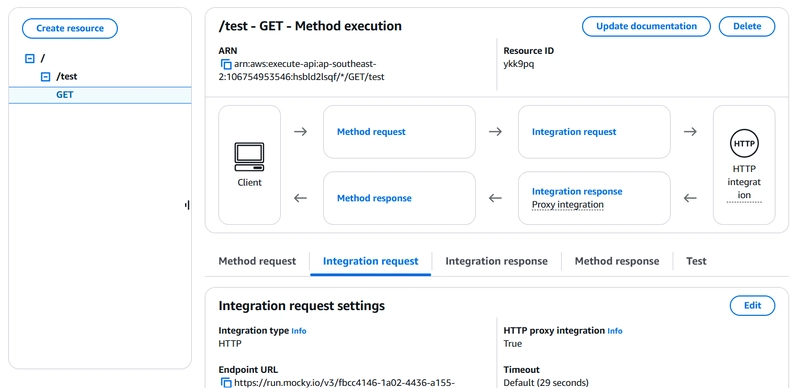
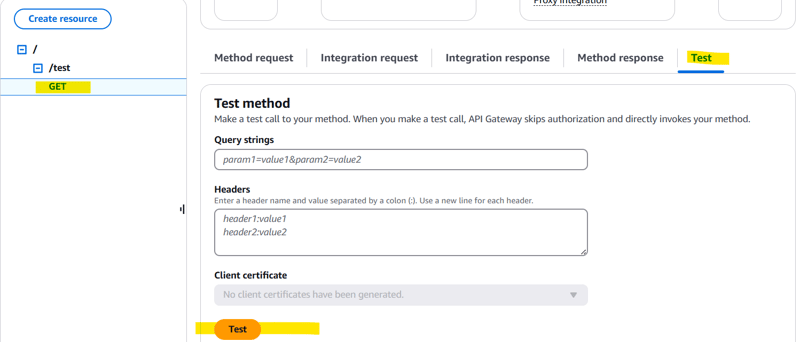
3️⃣ Create a resource and a method (e.g., GET /test)
4️⃣ Configure a mock integration for testing:
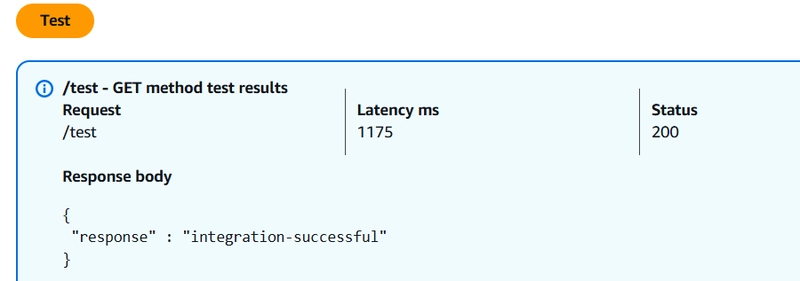
I'm using mock endpoint here. It will just return.
{
"response" : "integration-successful"
}
Select method and go to test.
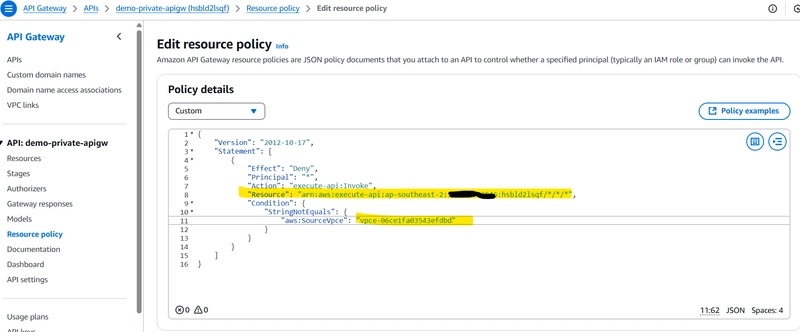
5️⃣ Set up a Resource Policy to allow traffic only from VPC Endpoint in Account B:
For resource include arn of private endpoints and sourcevpce should be id of vpc endpoint created above. This will make sure traffic will accepted only from vpc endpoint.
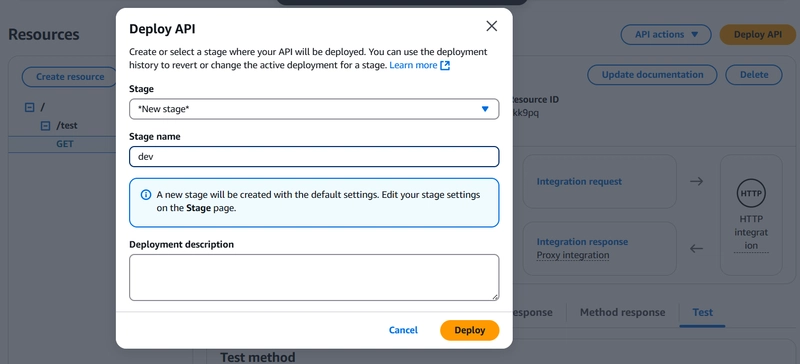
6️⃣ Deploy the API
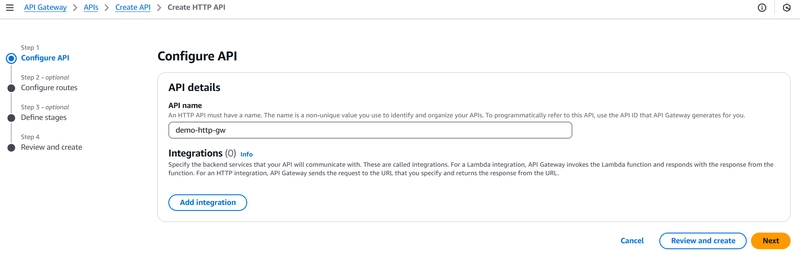
Step 3 : Create a Regional API Gateway (Account A)
Type: REST API (Regional)
Name: e.g., http-gateway
Create the http gateway.
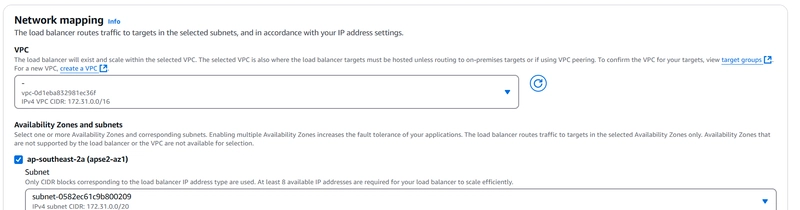
Step 3 : Create a Network Load Balancer (Account A)
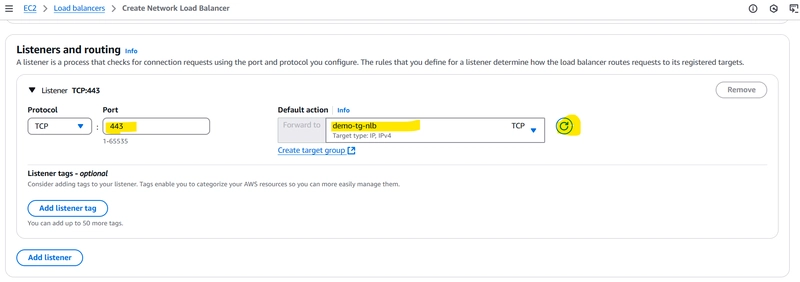
1️⃣ Navigate to EC2 > Load Balancers
2️⃣ Create a new Network Load Balancer
Scheme: Internal
VPC: Must have connectivity to the Private API Gateway's VPC
Subnets: Private subnets in Account A
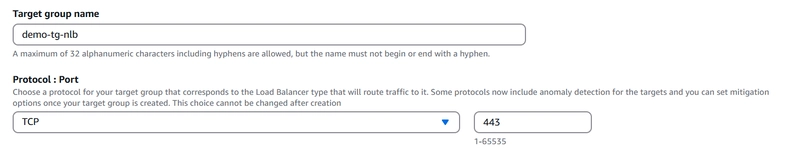
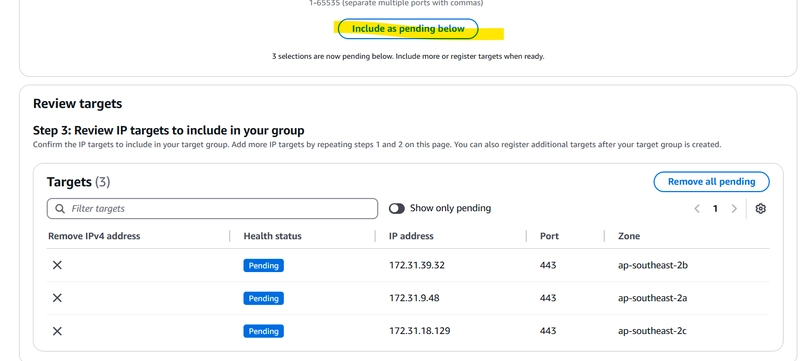
3️⃣ Create a Target Group:
Target Type: IP
Port: 443 (for HTTPS traffic to Private API Gateway)
VPC: that has connectivity with Private API Gateway
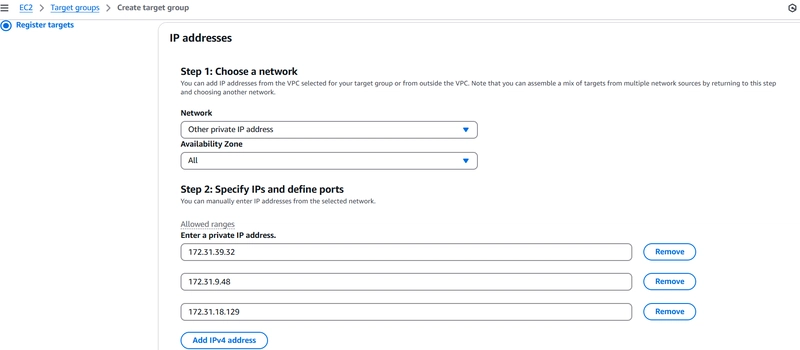
Target IPs: Enter VPC Endpoint IPs noted earlier
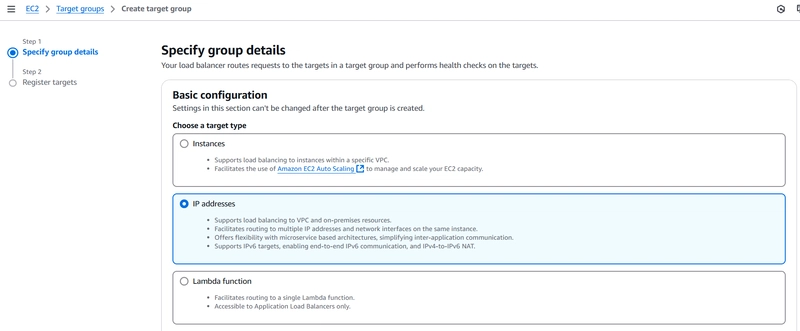
For IP addresses enter the Ip's of VPV endpoint previously note down in step 01 and keep port as 443.
4️⃣ Attach the Target Group to the Load Balancer
5️⃣ Create and activate the NLB
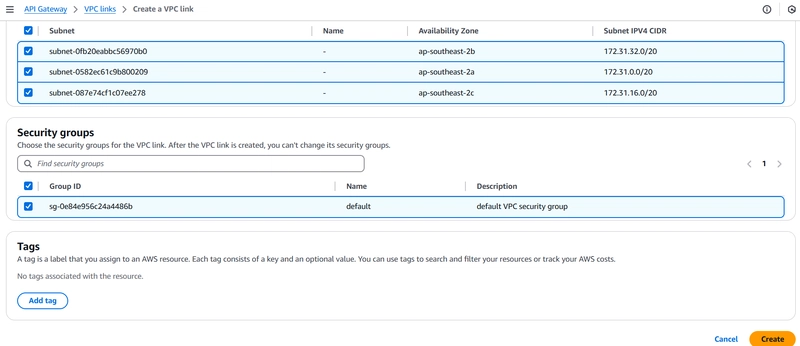
Step 4 : Create a VPC Link (Account A)
1️⃣ Navigate to API Gateway > VPC Links
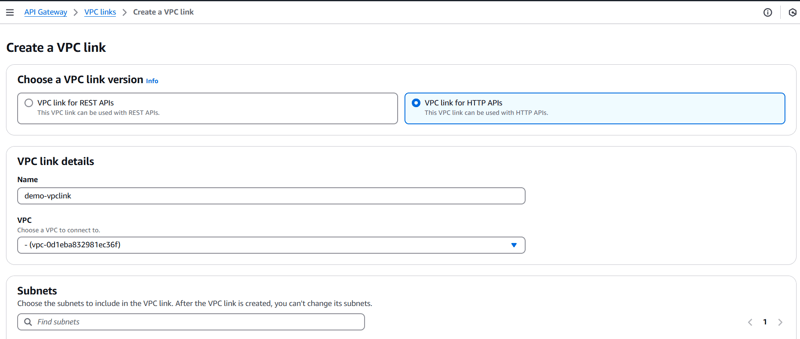
2️⃣ Create a new VPC Link
Type: Network Load Balancer
NLB ARN: Select the NLB created in Account A
3️⃣ Wait for the VPC Link to become available
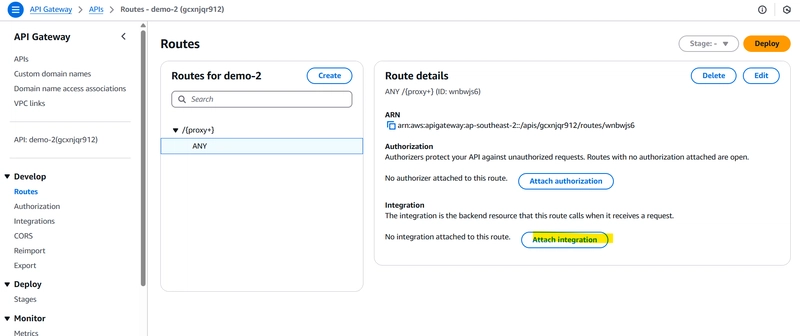
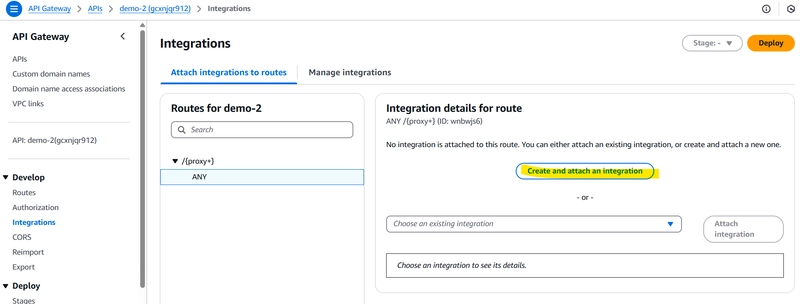
step 5 : Integrate http API Gateway with VPC Link (Account A)
1️⃣ Go back to the http API Gateway
2️⃣ Create a new resource & method
Method Type: ANY
PATH (use greedy path to pass all requests to private API: {proxy+}
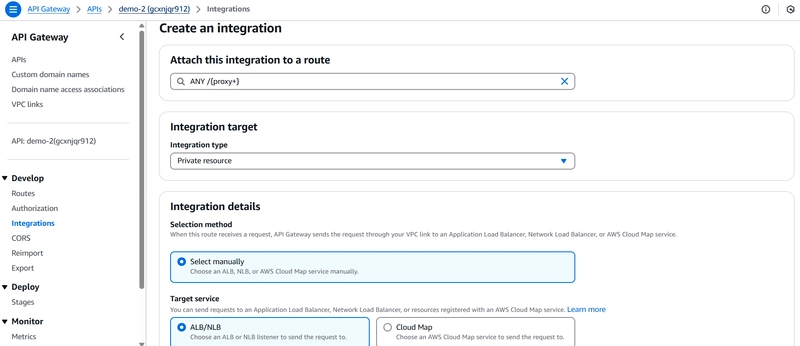
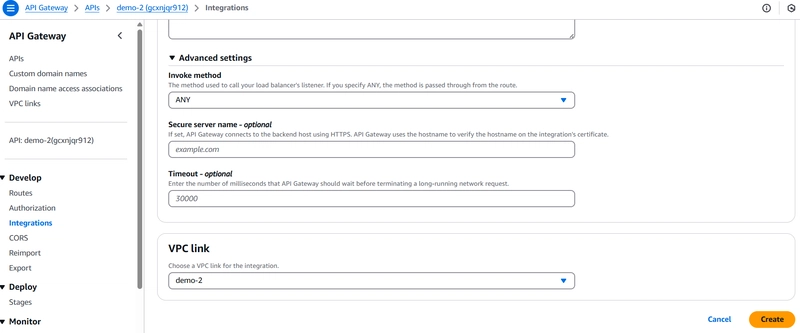
Integration Type: VPC Link
VPC Link: Select the one created earlier
Endpoint URL: Use the Private API Gateway Invoke URL from Step 1.
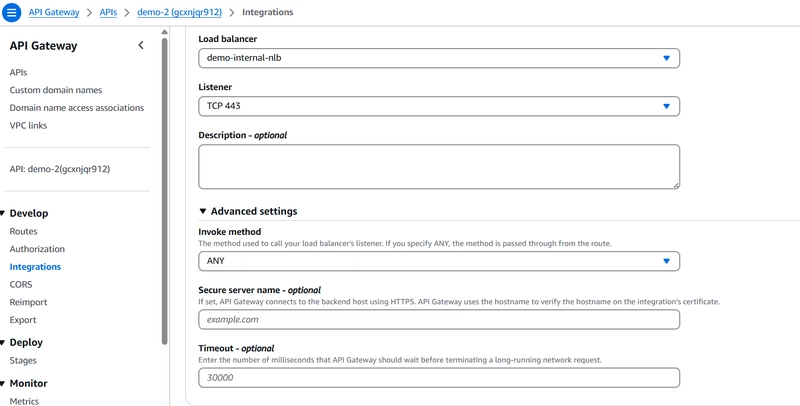
Select the load balancer created previously
Select the vpc link created above.
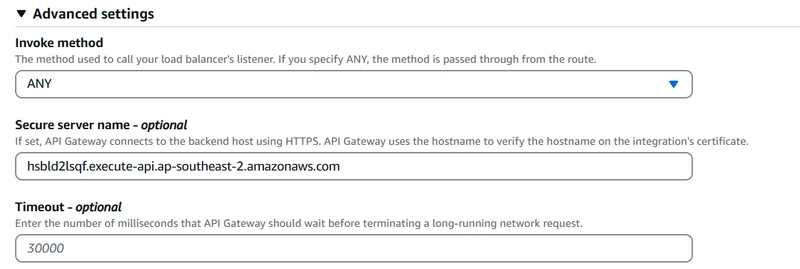
in the advance section for server name include invoke domain of private api gateway. Otherwise will get a certificate validation error.
Step 6 : Test
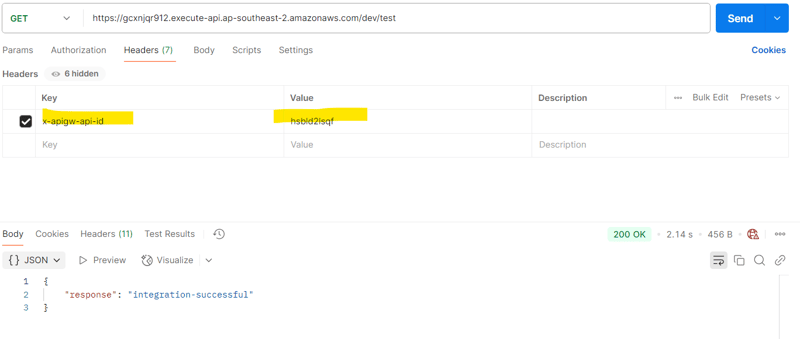
1️⃣ test the integration ✅
When sending the request to the regional api gateway invoke url need to include the header x-apigw-api-id with value as private api gateway ID.



Top comments (0)