Content Directory:
- Virtual Networks
- Virtual Subnets
- Creating Virtual Networks and Subnets in Azure portal
- Peering of two virtual networks in Azure
Virtual Networks:
➢Azure Virtual Network (VNet) is the fundamental building block for your private network in Azure.
➢VNet enables many types of Azure resources, such as Azure Virtual Machines (VM), to securely communicate with each other, the internet, and on-premises networks.
➢VNet is like a traditional network that you'd operate in your own data center but brings with it additional benefits of Azure's infrastructure such as scale, availability, and isolation.
➢Here we will also discuss Vnet and Subnet Practical, VNET Peering – One way and Two way
Virtual Subnets:
In a virtual network, a subnet is a set of IP addresses. For organisation and security, a virtual network might be divided into many subnets. Each NIC (Network Interface) in a virtual machine is connected to a single virtual network subnet. Within a virtual network, NICs linked to subnets (same or different) can communicate with each other without any additional configuration.
Creating Virtual Networks and Subnets in Azure portal:
To construct a virtual network and subnets, you can utilise the Azure portal. The name is a mix of the resource group name that contains the virtual network and -vnet if you let Azure construct a virtual network when you create a VM. 10.0.0.0/24 is the address space, default is the needed subnet name, and 10.0.0.0/24 is the subnet address range.
When you construct a virtual machine (VM), you either create or use an existing virtual network. It's critical to plan ahead of time before developing resources and to be aware of the limitations of networking resources.
When you create a virtual network, you specify the topology, which includes the address spaces and subnets that are available. If the virtual network is connected to other virtual networks or on-premises networks, use address ranges that do not overlap. Any address range is considered part of the private virtual network IP address space in Azure.
By default, there are no security borders between subnets. Each of these subnets has virtual machines that can communicate with each other. Use Network Security Groups (NSGs) to regulate traffic flow to and from subnets and VMs if your deployment requires security boundaries.
In the following figure, each set of virtual machines is assigned to separate subnets in the virtual network.
Creating Virtual Network ‘FINANCE-VNET’ with 2 SUBNETS: ‘subnet-1’, ‘subnet2’.
Similarly creating a Virtual Network ‘HR-VNET’ with 2 subnets: ‘subnet-1’ and ‘subnet-2’.
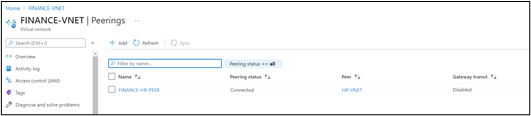
Peering of two virtual networks in Azure:
In Azure, virtual network peering allows you to link two or more Virtual Networks in a seamless manner. For connectivity reasons, the virtual networks appear to be one. The Microsoft backbone technology is used to transport traffic between virtual computers in peer virtual networks. Traffic is routed over Microsoft's private network only, just like traffic between virtual computers on the same network.
The following peering types are supported by Azure:
*Virtual network peering: Connect virtual networks within the same Azure region.
*Connecting virtual networks across Azure regions using global virtual network peering.










Top comments (0)