What is enumeration?
Enumeration is the first and most important step of any form of hacking. You need an in depth understanding of what you're going up against. For example, in a CTF, you need to know which ports are going to be open and which services they belong to.
Network enumeration
Network enumeration is going to give us a better understanding of what targets on a network are doing.
Discovering hosts on a network
Tools such as:
Can help us enumerate which devices are on a network using ICMP packets (pings) or ARP. Some specialised tools such as Bloodhound may help us enumerate networks using Active Directory.
Discovering open ports on a target
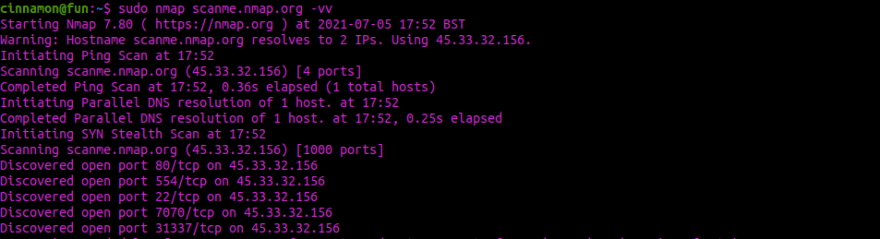
Once we have our target, we need to understand what the target is doing and potential attack vectors. Below is a sample of an nmap scan:
We can see there are 5 ports open. We may be able to exploit the HTTP service on port 80 or gain access to SSH on port 20. Port scanning can be slow, tools such as PyRCON and Rust Scanner may help us speed up this process. Typically this isn't necessary but in a KOTH or battlegrounds game, we can't spare the time.
Website enumeration
Websites are a huge attack vector as they're often public facing and have countless possible flaws, depending on their configuration. There are many tools that we can use to gain a better understanding of the website. Such as:
Specialised tools can be used, for example WPScan. Allowing us to enumerate the wordpress CMS.
Domain enumeration
In a real-world scenario. You're likely to come across a target with more than one domain, each having it's own subdomains. There's plenty of tools that you can use to discover these. Again, PyRCON offers some options for this but I like tools such as sublist3r and publicly available records such as security trials.
Tools such as Dig (preinstalled on most Linux distros) may also be used for performing DNS queries, alongside nslookup. They may also be used for resolving a domain name from an IP Address (for example: 45.33.32.156 -> scanme.nmap.org)


Top comments (0)