Say, you need a real quick solution for your new data security tasks and the challenge looks no less enormous than your project. Just yesterday it was ok not to think about security, but things change fast nowadays, and the need to get your highly sensitive data well-protected could jump out at you all of a sudden.🤔
The idea of re-writing a whole app or even a bunch of them could be somewhere near falling into despair, but hold on, an immediate relief over sensitive data concerns is on the way. 💡 In some situations, infrastructure architecture allows to skip the full re-engineering of your current solution.
Don't panic and use Acra database security suite as the goal can be reached in a dev-friendly way.
Let’s be practical and explore a real case.
▶️ We solved alike issue for a nationwide company when updates in regulations demanded from it to protect sensitive data even more thoroughly. Our customer already had a huge infrastructure and stopping or slowing down its operations was not an option at all. They had more than 60 applications and thus had to manage an enormous number of keys and access policies to the same instances/databases. We were asked to blend in stronger data protection, compliant with FIPS 140-2, as smooth as possible and in no more than 12 weeks.
💡 If you are to choose between quick patching the problem or re-organizing architecture to minimize possibilities for problems, we would recommend looking at all potential scenarios beforehand. A strong foundation and architecture design give less room for problems.
Here’s what we did
✔️ First, we started with outlining the architecture (including security policies and a key lifecycle) that would meet the customer’s needs and security requirements.
✔️ Then, we tested the environment under various load, data volume, and network and security configurations to satisfy the demands.
✔️ After that, we turned to building a migration pipeline from their current solutions to a new one and flow that would not cause any disruption to customer operations.
💡 A secure dataflow solution—equally for small or large-scale projects—could be designed using different modules of Acra without great sacrifice. We built it to be an effective part of a solution not another part of a problem.
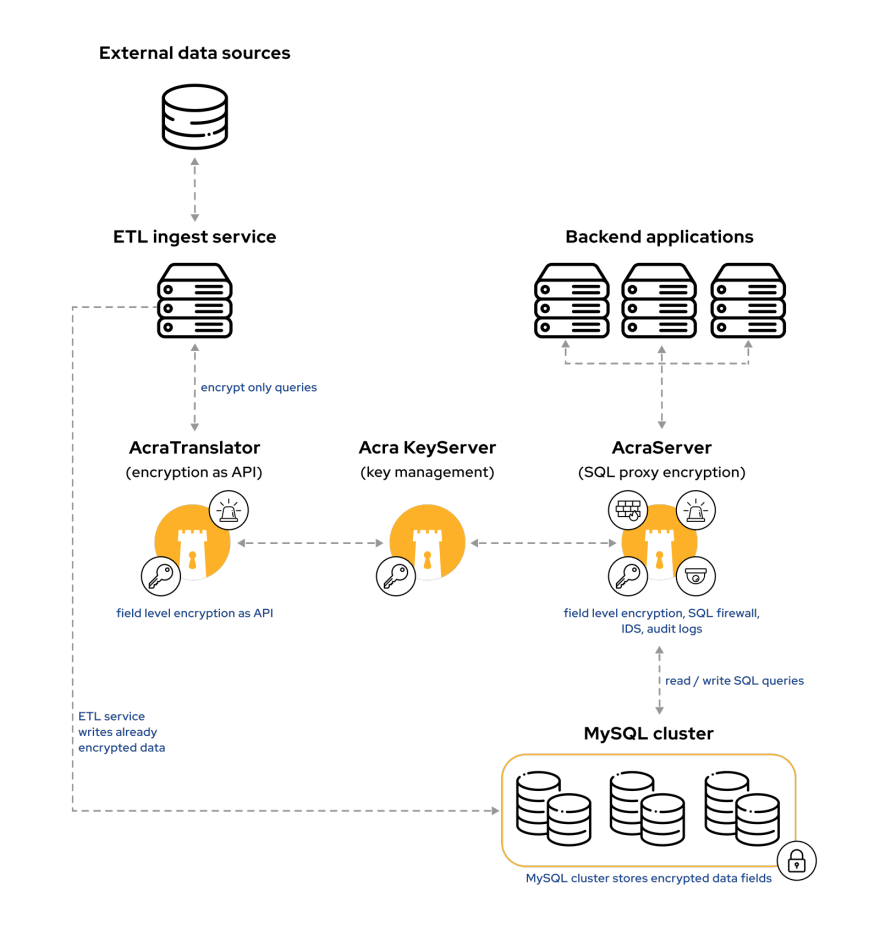
Let’s have a look at the secure data flow solution based on Acra, that we suggested:
💡 After passing through ETL gateway, large amounts of sensitive data are processed and encrypted “on a fly” with the help of AcraTranslator (API service), which requires only simple application modification to start working.
💡AcraServer (SQL proxy), placed between an app and DB as a proxy, encrypts/decrypts data transparently for the apps, parsing SQL queries directly to and from databases. Almost no changes in the app code are required.
▶️ Together, AcraServer and AcraTranslator keep an eye on every transmission of sensitive data. Acra identifies the app, uses mutual TLS authentication before accepting the connection, and decides on which data fields should be decrypted. (In apps with several levels of protected data, a variety of access levels are reached by using Zones, that manage which data to show in plaintext or masked.)
As for compliance with FIPS 140-2, Acra uses open-source cryptographic library Themis, which received a certified crypto module used to perform core cryptographic operations in a compliant manner.
🏁 So, by making changes in secure architecture and using Acra modules we blended data security into constrained architecture without re-writing the application code.
😊 Good thing is that Acra is available not only to huge enterprises/budgets but to small-scale projects as well (download open-source Acra Community Edition from GitHub and use it for free). While, yep, in large enterprises Acra uncovers its defensive strengths for strong solutions in full. 🔐



Top comments (0)