Introduction
DevOps’s lightning-fast software development cycles imply traditional security measures can’t keep up. Organizations must include automated and continuous security testing in their software development processes to enhance security. It’s all about making security a part of the DevOps process — DevSecOps. That’s Filling the gap between I.T and security by incorporating security into every step of the software development lifecycle process Security bottlenecks may be alleviated by using the DevSecOps strategy. It also maintains the high development pace that DevOps allows. This post will share how the DevSecOps framework, activities, process, and challenges during your DevSecOps transformations.
What is DevSecOps?
DevSecOps is the practice of incorporating security and compliance testing into the DevOps pipeline without jeopardizing the speed and agility of continuous delivery. DevSecOps adoption is needed to make software delivery more agile, responsive, and secure. More team collaboration between IT security and the product team (including development and operations) must happen. In the past, the security team worked alone. There were always security and compliance checks done at the end. When you have a faster software delivery cycle with DevOps and more often make software, those checks at the end make it more difficult and slow down the continuous delivery process.
Why Move to DevSecOps?
The increased delivery velocity with a DevOps CI/CD pipeline, particularly with microservices-based applications, is prone to introducing vulnerabilities and making continuous security a major issue in organizations.
Security teams must learn and understand the security implications of all these new technologies to identify issues. The learning curve becomes a significant bottleneck, so automating security checks early in the continuous delivery process, i.e., practising DevSecOps.
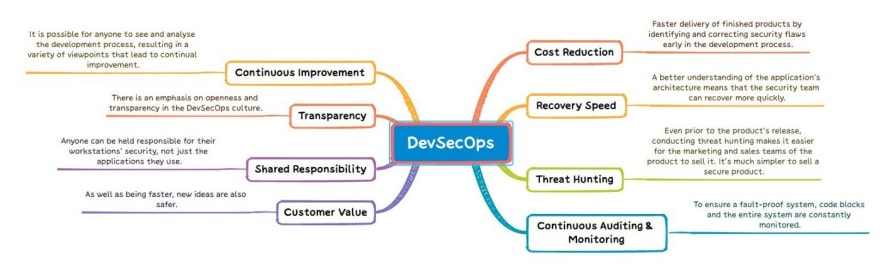
DevSecOps Benefits
DevSecOps Metrics
DevSecOps is a proven method for improving the quality and security of software, which can be measured using these metrics:
• Meantime to production: the average time it takes from when new software features are required to when they are up and running.
• Average lead-time: the time it takes to deliver and deploy a new requirement.
• Deployment speed: how quickly DevSecOps can deploy a new application version into production.
• Deployment frequency: the frequency with which DevSecOps can deploy a new release into production.
• Production failure rate: the frequency with which software fails during production.
• Mean time to recovery (MTTR): the time it takes for applications in the production stage to recover from a failure.
Furthermore, DevSecOps practice enables:
• Fully automated risk characterization, monitoring, and mitigation throughout the application lifecycle; and
Software updates and patching on-demand allows for addressing security vulnerabilities and code flaws.
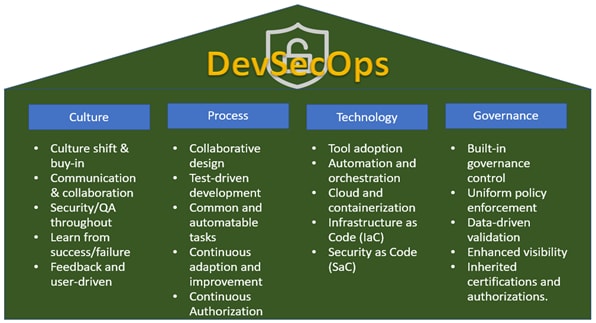
Four (4) DevSecOps Pillars
The diagram shows that DevSecOps is supported by four pillars: culture, process, technology, and governance.
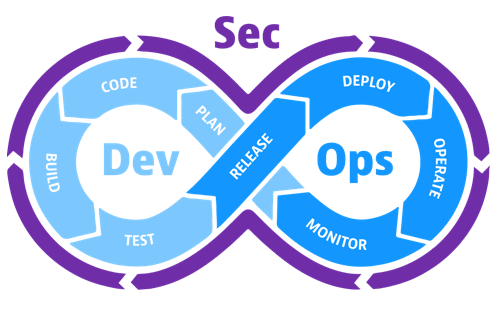
DevSecOps Lifecycle
The DevSecOps software lifecycle phases. Plan, develop, build, test, release, deliver, deploy, operate, and monitor are the nine (9) phases. Security is implemented in each stage:
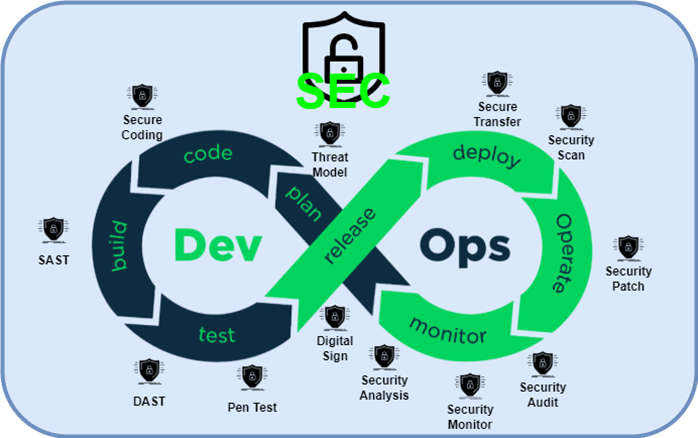
The software development lifecycle is not a monolithic linear process with DevSecOps. The Waterfall process’s “big bang” delivery style is replaced with smaller but more frequent deliveries, making it easier to change course as needed. DevSecOps implementation accelerates continuous integration and delivery, and each small delivery is completed through a fully automated or semi-automated process with minimal human intervention. The DevSecOps lifecycle is adaptable and includes numerous feedback loops to ensure continuous improvement.
DevSecOps Framework
The above picture presents a framework for getting started with crucial DevSecOps domains and activities.
DevSecOps Challenges
Issue1: Not Many DevSecOps Talent in the Market
Some continent might facing issue lack of DevSecOps Engineer/Talent since DevSecOps still a broad topic or approach most of organizations
Solution1: Diverify your DevSecOps Team
Instead looking in same region or continental, you have to start looking in differenct region or offshore DevSecOps Engineer to help in your transformation journey.
Issue2: End-of-cycle security testing causes delays and bugs to stay in the production process.
The conventional method of trying to shoehorn security into a nearly finished product is unsatisfactory. Too many flaws are finding their way into production code.
Solution2: Integrate security analysis into the very beginning of the development process.
Instead, security may be woven into the fabric of daily operations and growth. In order to move security compliance into the very early phases of development, developers should be able to do analysis right within the IDE.
Issue3: To "fix" security is a difficult task.
It's a big order for developers and testers who aren't security professionals to be told to "fix" security in the last phases of development when it's unclear what to do.
Solution3: Continually improve the level of security.
There is no need for separate teams to implement their own security rules, such as safe coding standards and static analysis tests for common vulnerabilities.
Issue4: There is no way to know the project's security risk until the last minute.
If a project doesn't have any form of vulnerability assessment, there are no recognised security issues. When late-cycle testing uncovers security flaws, it often leads to rework and further delays. Security flaws still find their way into the hands of users despite these valiant last-minute attempts.
Solution4: Software quality and security are constantly checked.
Compliance reporting or Vulnerability Management tool should give dashboards that are simple to use and provide a high-level and a detailed perspective of the data.
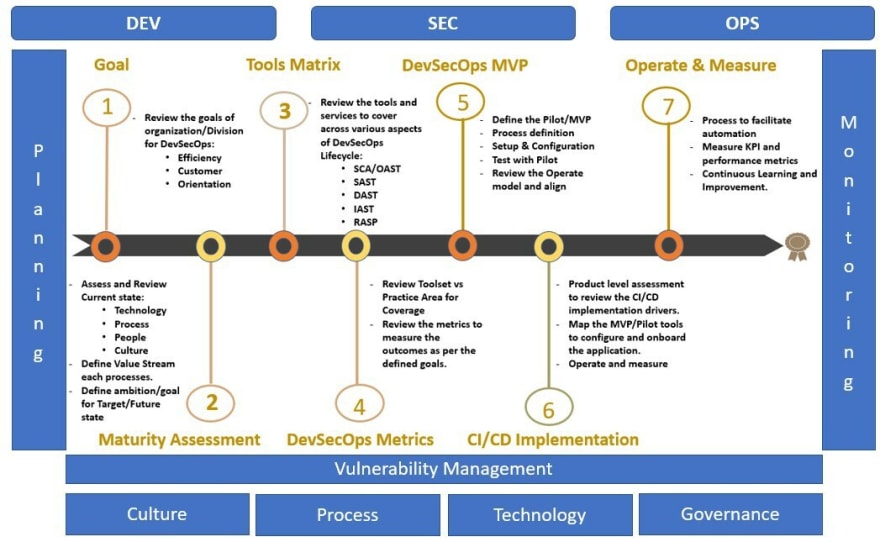
Get Started
It’s a good idea to move to DevSecOps if your firm is currently using DevOps. As a result, DevSecOps is founded on the DevOps mindset, which will make it easier for you to switch. So you may bring together people with diverse strategic backgrounds to work on improving the security procedures that are already in place. This post just discussed the non-technical of DevSecOps transformation; we will dive deeper into the DevSecOps scanner tool and CI/CD implementation using AWS CodePipeline. I hope to see you back in the next post for the DevSecOps CI/CD pipeline and its tools involved.


Top comments (0)