What is Man In The MIDDLE (MITM) attack
A man-in-the-middle (MITM) attack is a general term for when a perpetrator positions himself in a conversation between a user and an application—either to eavesdrop or to impersonate one of the parties, making it appear as if a normal exchange of information is underway. In another way, we can say that a man-in-the-middle (MITM) attack is a type of cyber attack in which the attacker secretly intercepts and relays messages between two parties who believe they are communicating directly with each other. The attack is a type of eavesdropping in which the attacker intercepts and then controls the entire conversation.
The goal of an attack is to steal personal information, such as login credentials, account details, and credit card numbers. Targets are typically the users of financial applications, SaaS businesses, e-commerce sites, and other websites where logging in is required.
Information obtained during an attack could be used for many purposes, including identity theft, unapproved fund transfers, or an illicit password change.
Additionally, it can be used to gain a foothold inside a secured perimeter during the infiltration stage of an advanced persistent threat (APT) assault.
Broadly speaking, a MITM attack is an equivalent of a mailman opening your bank statement, writing down your account details, and then resealing the envelope and delivering it to your door.
How do MITM attacks work?
During MITM attacks, cybercriminals insert themselves in the middle of data transactions or online communication. Through the distribution of malware, the attacker gains easy access to the user's web browser and the data it sends and receives during transactions. Online banking and e-commerce sites, which require secure authentication with a public key and a private key, are the prime targets of MITM attacks as they enable attackers to capture login credentials and other confidential information.
Typically, these attacks are carried out through a two-step process known as data interception and decryption.
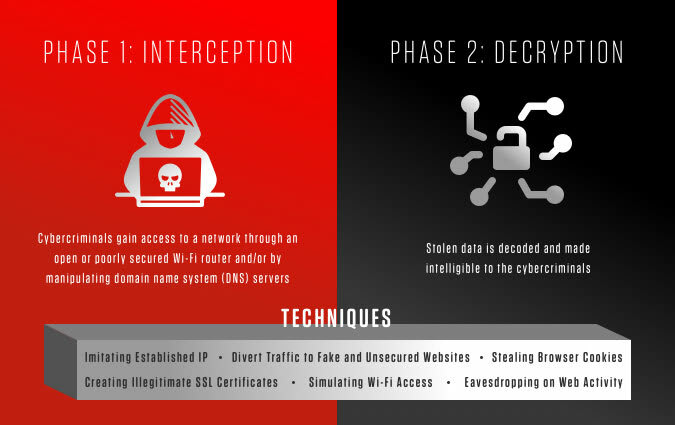
Interception Phase
Data interception entails an attacker intercepting a data transfer between a client and a server. The attacker tricks the client and the server into believing that they are exchanging information with each other, while the attacker intercepts the data, creates a connection to the real site, and acts as a proxy to read and insert false information into the communication.
Decryption Phase
The decryption phase is where the intercepted data is unencrypted. This essential step enables the attacker to finally decipher and use the data to their advantage; for example, they can carry out identity theft or cause disruptions to business operations.
What are the types of man-in-the-middle attacks?
Some of the attacks are:
Internet Protocol spoofing
It involves an attacker disguising himself as an application by altering packet headers in an IP address. As a result, users attempting to access a URL connected to the application are sent to the attacker’s website.
Domain Name System spoofing
This is a type of man-in-the-middle attack where cybercriminals alter domain names to redirect traffic to fake websites. Users might think that they are reaching a secure and trusted website, but instead, they land on a website operated by cybercriminals. The main aim behind DNS spoofing is to reroute traffic to a fake website or to capture user login credentials.
Address Resolution Protocol (ARP) spoofing
It is a type of attack in which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of an attacker’s MAC address with the IP address of a legitimate computer or server on the network. Once the attacker’s MAC address is connected to an authentic IP address, the attacker will begin receiving any data that is intended for that IP address. ARP spoofing can enable malicious parties to intercept, modify or even stop data in-transit. ARP spoofing attacks can only occur on local area networks that utilize the Address Resolution Protocol.
HTTPS spoofing
In this attacker uses a domain that looks very similar to that of the target website. With this tactic, also known as “homograph attack”, the characters in the target domain are replaced with other non-ASCII characters that are very similar in appearance. The unsuspecting user is very unlikely to notice the difference and is rest assured by the browser’s secure connection indication.
Secure Sockets Layer (SSL) hijacking
SSL is a protocol that establishes an encrypted connection between a browser and the web server. During SSL hijacking, a cybercriminal might use another computer and a secure server to intercept all information traveling between the server and the end user's computer.
Email hijacking
This is a type of MiTM attack where cybercriminals gain control of email accounts of banks and other financial institutions to monitor any transactions that users conduct. Cybercriminals may even spoof the bank's email address and send instructions to customers that lead them to unknowingly transfer their money to the cybercriminals.
Wi-Fi eavesdropping
This MITM attack is one of the many risk factors posed by public Wi-Fi. During this attack, public Wi-Fi users get tricked into connecting to malicious Wi-Fi networks and hotspots. Cybercriminals accomplish this by setting up Wi-Fi connections with names that resemble nearby businesses.
Session hijacking
Also known as stealing browser cookies, this malicious practice takes place when cybercriminals steal personal data and passwords stored inside the cookies of a user's browsing session. Sometimes, cybercriminals can gain endless access to users' saved resources. For example, they might steal users' confidential data and identities, purchase items or steal money from their bank accounts.






Top comments (0)