This article walks through how to push and pull Helm charts on Azure Container Registry (ACR) locally. The same concept can also be used on a pipeline for automation.
Table of Contents
Prerequisites
- Azure Portal account
- Helm installed
- Azure Container Registry created
Note
The Helm chart version I’m using is version 3.10, there is an issue with Helm version 3.13 unable to push or pull charts to ACR even after logging into the registry successfully, throwing a status code 401 error.
Pushing To ACR
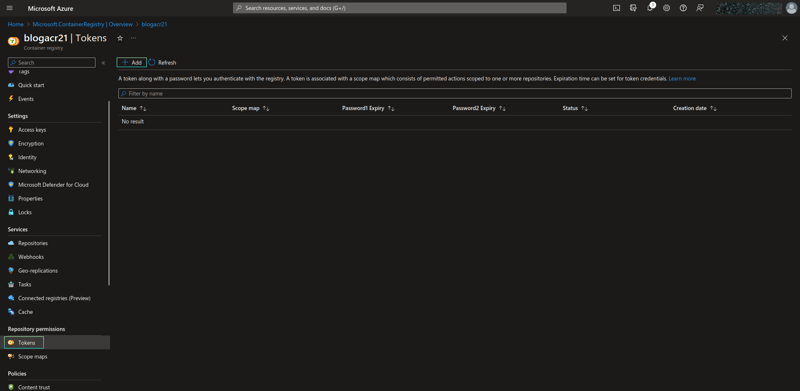
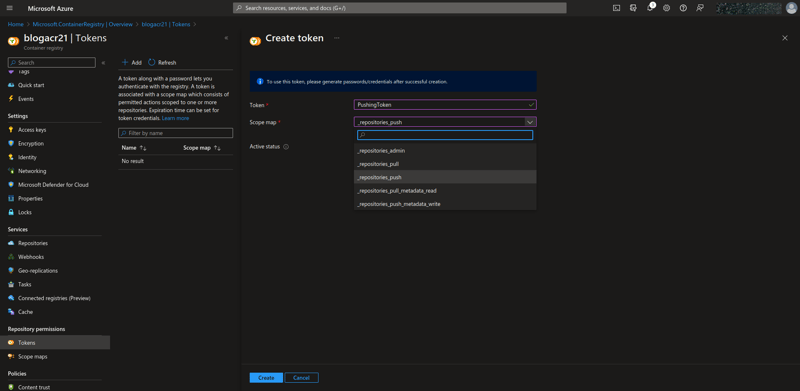
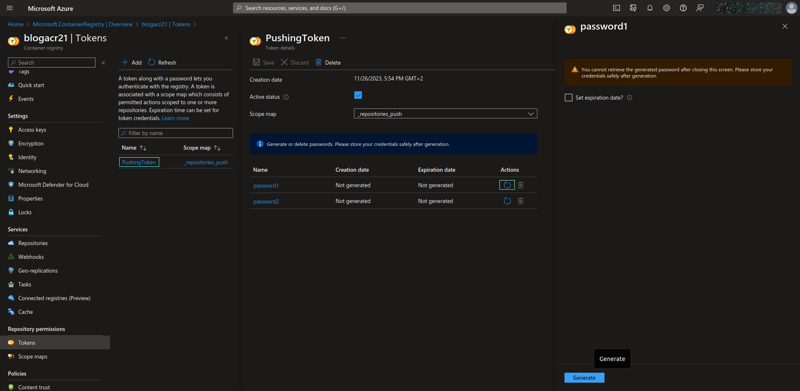
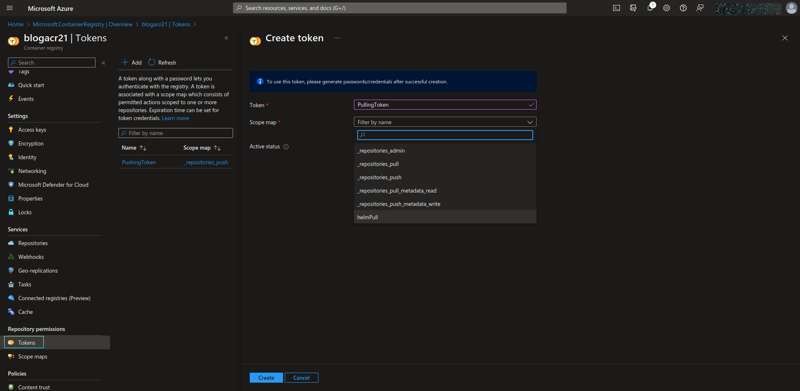
Navigate to your created ACR (mine is named blogacr21), on the sidebar, scroll down then click on Tokens (right under Repository permissions) and create a new token. Define the token name and scope map (_repositories_push for the current case). Click on your newly created token then generate for yourself a password.
Login to your ACR with your created token by using the following command (blogacr21 is my acr_name, PushingToken is my token_name). You’ll be asked to enter a password, paste the one that you generated.
helm registry login <acr_name>.azurecr.io/helm --username <token_name>
# Login Succeeded
In case you don’t have a Helm chart, create one and package it for it to be pushed.
helm create demo-chart
helm package demo-chart
# Successfully packaged chart and saved it to: /path/to/demo-chart-0.1.0.tgz
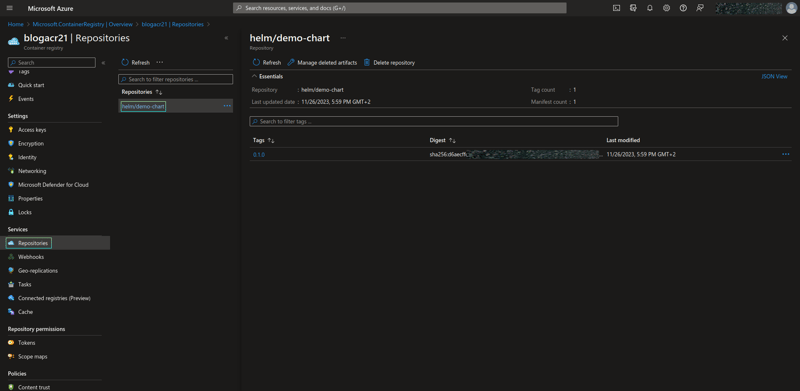
Push the chart using helm push command, it’ll be a successful push when it returns the hash digest, you should find the same digest if you checked on your repository.
helm push demo-chart-0.1.0.tgz oci://blogacr21.azurecr.io/helm
# Pushed: blogacr21.azurecr.io/helm/demo-chart:0.1.0
# Digest: sha256:d6aecffcxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
Pulling From ACR
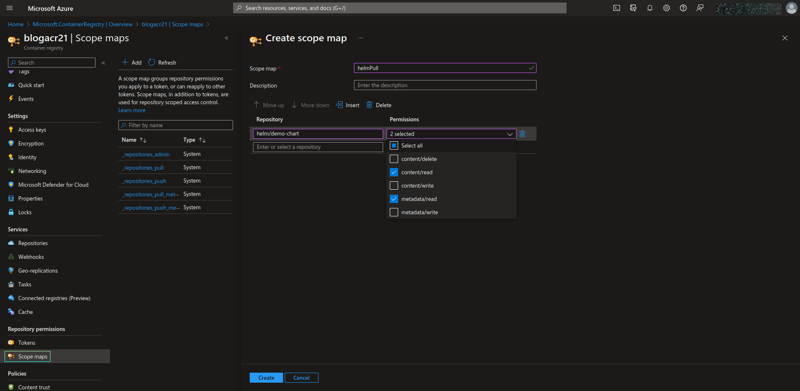
Just like in the previous steps for pushing to the repository, you’ll need to create another token that has pulling permissions (or you could use the admin scope map but wouldn’t be a good security practice if it got compromised). ACR offers that you can create your custom scope map even targeting a specific repository only than having it on all repositories (just an extra best practice!) Go to Scope maps and create a new scope map. To have pulling permissions only, check just content/read and metadata/read permissions.
Create a new token and assign the scope map to the one that you just created for pulling the helm chart, then generate a new password and do registry login using the new token.
helm registry login <acr_name>.azurecr.io/helm --username <token_name>
# Login Succeeded
When a successful helm pull command is executed, you’ll find the packaged chart downloaded.
helm pull oci://blogacr21.azurecr.io/helm/demo-chart
# Pulled: blogacr21.azurecr.io/helm/demo-chart:0.1.0
# Digest: sha256:d6aecffcxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
If you tried pulling another Helm chart (say helm/demo-chart2) using the same pulling token where it has scoped just on the demo-chart repository, it shouldn’t be authorized and you should receive a status code 401.
helm pull oci://blogacr21.azurecr.io/helm/demo-chart2
# Error: GET "https://blogacr21.azurecr.io/v2/helm/demo-chart2/tags/list": unexpected status code 401: unauthorized: authentication required, visit https://aka.ms/acr/authorization for more information.
Even if you tried pushing the same chart using the pulling token it shouldn’t be authorized as well because it lacks write permissions.
helm push demo-chart-0.2.0.tgz oci://blogacr21.azurecr.io/helm
# Error: server message: insufficient_scope: authorization failed
Conclusion
There can be other ways to use ACR and storing your Helm charts in them. However, using tokens can be the quickest way to set things up even on pipelines for automation, and if scope maps were used you can avoid having the risk of getting the entire repository compromised.



Top comments (0)