TL;DR
- Zero Trust Network is post VPN for remote access.
- Base on HTTPS and Context awareness access Control(CAAC)
- Big paradigm shift from Firewall boundary to ID boundary
What is Zero Trust Security?
Do you know Zero Trust Security?
Now many people work from home due to Coronavirus disease (COVID-19).
This is very very bad situation for your life, health and global economy.
However, it is good opportunity to consider about remote access.
Roughly speaking, we can understand Zero Trust Network is post VPN.
This concept is simple, "Never trust, anywhere and anyone".
Traditional VPN and Offie network are base on trust networks.
It made trust network in office and DC. These physical facilities are connected trust network like dedicate line. And they are protected Firewall.
Firewall is the Great Wall to separate trust networks and untrusted
networks. Security solutions take care a lot about access from untrusted networks.
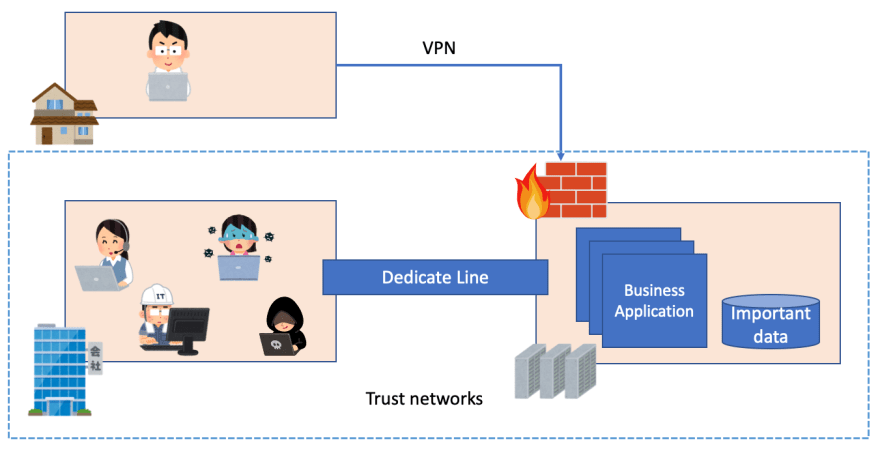
Image: Traditional office networks
VPN is only way to connect trust networks through untrusted networks as the special solution.
On the other hands, Zero Trust Network is base on untrusted networks.
Today, remote access is very natural requirement. And Attacks have gotten more malus continuously. We have to take care about access from even trust network. That's why zero trust network start from untrusted network. So they can provide same security models whether trust networks or untrusted networks.
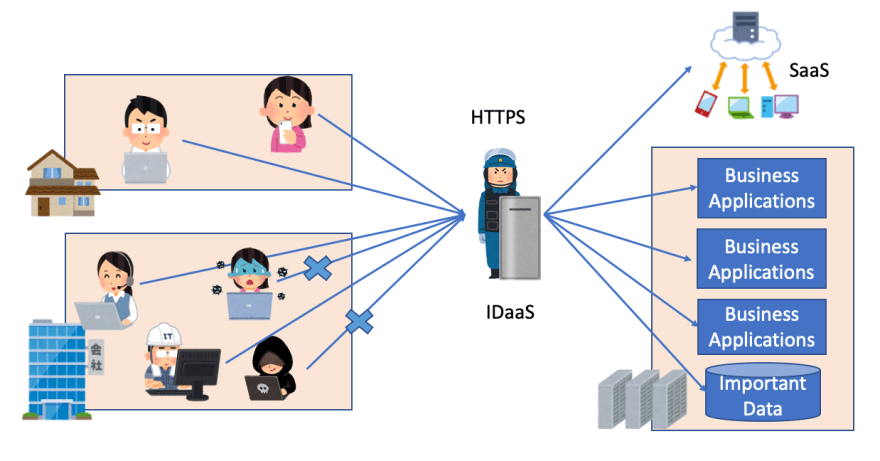
This approach protect systems by IDaaS like AzureAD or Google Cloud Identity instead of network firewall.
Whether from office or home, each access is controlled by Context like user account, device, location and target application.
Why do we need post VPN?
Before deep diving to Zero trust network, let me explain why do we need post VPN.
There is two issues.
- Performance
- Difficulty of right access control
- Consistent security policy
Performance
VPN performance is not so good. Because encryption is heavy task and it has latency problem. Even we want to connect to SaaS, we need access data center as VPN access hub. It is an extra connection.
In addition, capacity plan is difficult. Because in the normal situation, only very few people will access from remote. However disaster situation like now, remote access will increase dramatically for BCP.
Honestly specking, it's difficult to always secure enough capacity for emergency.
Difficulty of right access control
VPN looks internal access, so it difficult to control office or home by application side.
For example, if you want only approve e-mail and some reporting tool from remote but you don't want to access business application which includes customer information. This requirement is natural. However if you want to realize, you may need to make or change firewall and network configuration. You need take care about network segment of each application. If you want to change such a remote access privilege level depending on role or person, you also need to take care about IP address which is distributed by VPN. If you want to utilize VDI(Virtual Desktop Infrastructure), issue will be complex more and more.
This is a big problem.
Consistent security policy
We should use consistent security model to avoid complexity.
However, tradition office network is difficult to do it.
First of all, it only provides security through trust network. Because almost security solutions like AV, EDR, CASB, device management are deployed on data center. This mean remote device is only applied through VPN. If VPN is not connected, that device is not secure. The problem is caused by that only the office is the first citizen and remote access is not.
Second is SaaS. Office networks changed. We utilize not only intra system but also many SaaS product for our business environment. In this case, we also take care about SaaS access control and generally it is separated from current office configurations.
From these three reasons, we need to consider about new security model.
Context-Aware Access Control (CAAC)
CAAC is key component for zero trust security network.
Role base access control (RBAC) verify user/role and target application. This is a better approach than just Network access control (NAC). Generally, we combinate NAC + RBAC. But it still not enough.
CAAC verify user/role, device, location and target application. Location is typically network. So CAAC realize same control with NAC + RBAC by only single security control.
Below is an example scenario.
This sales staff can access to their customer management (CRM) system from office.

But, even same person and same device can't access to their CRM from office.
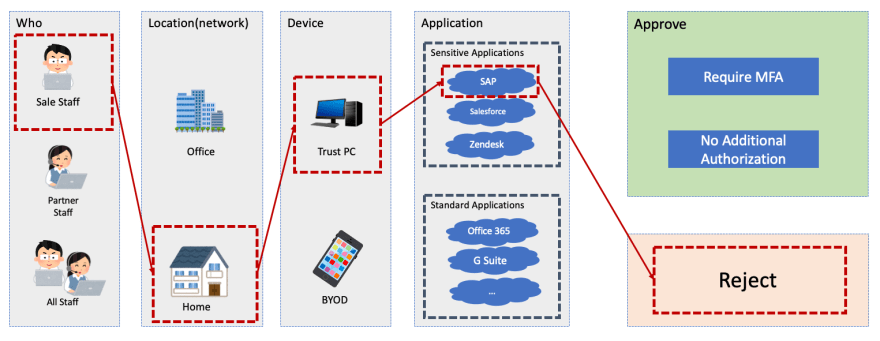
And he can access Office 365 like e-mail and one drive from home. However ind this case, he is required additional authentication like MFA.

CAAC realize such a control easily. If we want do same control by NAC + RBSC, it is very complex configurations.
Conditional access of Azure AD and Cloud IAP of GCP are popular implementation of CAAC.
Office network with Zero Trust Network
Zero Trust Network is ID base security boundary. It is able to apply same control both office and home by CAAC.
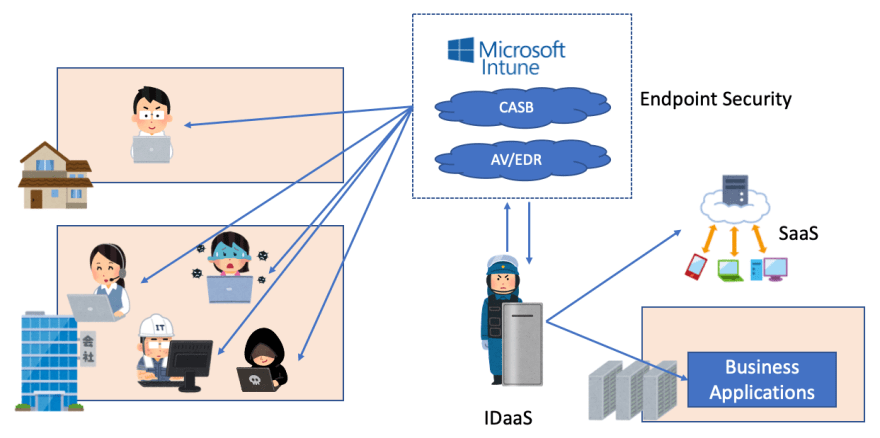
To utilize this control, typical we use cloud security for endpoint security like AV, EDR, CASB, device management.
These tools can apply security whether trust networks or untrusted networks.
Form CAAC and Cloud Security, we can resolve Difficulty of right access control and Consistent security policy.
In addition, Zero Trust Network doesn't apply extra encryption. Because every application should support HTTPS/TLS. Then they don't need extra overhead by encryption.
Someone may afraid HTTPS is less secure than VPN, but it's not true.
VPN is based on TLS. So security level is completely same with HTTPS. Sometime VPN also support device trust. But IDaaS like Azure AD also support device trust with Intune. So we can say "It's completely same with VPN".
Finally, zero trust security network doesn't take care about remote access or NOT. This mean everyone has capability of remote access. It is just control. So even if remote access increase by BCP, capacity is always enough.
Conclusion
VPN was good solution. However it has some issues today.
We should shift from traditional network model to zero trust networks.
Of course, migration is not easy. However always improvement is only way to keep security.
We should be consider everything about security.
Happy Hacking!


Top comments (0)