The need for tenant isolation and various strategies for isolating AWS resources
_Written by @sharibj _
Introduction
In the dynamic world of Software as a Service (SaaS), the concept of multi-tenancy has become a game-changer. It allows SaaS providers to efficiently serve multiple customers or tenants using a single application, effectively streamlining operations and reducing costs by pooling resources. However, beneath the surface of this efficiency, lies a critical imperative: the need to implement robust isolation strategies. These strategies are vital to ensure the security, compliance, and strategic growth of your SaaS application.
In this blog we'll explore why isolating your tenants is essential and delve into different isolation strategies, focusing on isolating Amazon Web Services (AWS) resources.
Why should you isolate your tenants?
Security
Imagine a scenario in which tenants within your SaaS application inadvertently access each other's data or applications. This can lead to a cascade of unauthorized breaches, compromising the confidentiality and integrity of their sensitive information. Proper tenant isolation acts as a fortress, maintaining the confidentiality and integrity of their data.
Compliance
For many SaaS providers, achieving compliance with industry standards and regulations is non-negotiable. Stringent requirements such as GDPR or HIPAA necessitate rigorous data handling practices. Isolating tenants simplifies this task by providing clear boundaries. It ensures that each tenant's data is treated according to the stipulated standards, simplifying compliance implementation and demonstration.
Strategy
In the competitive SaaS landscape, strategic thinking can make all the difference. Isolating tenants opens up the possibility of implementing a tiered service model or tenant specific customizations. This means you can offer different levels of service to tenants based on their unique requirements or subscription plans, providing a distinct competitive edge.
Opportunity
Strong tenant isolation isn't merely a defensive measure; it's also a strategy to create new business opportunities. By offering robust isolation, you can attract high-profile clients with stringent security requirements. This opens doors to increased revenue and substantial business growth.
What are the different isolation strategies for AWS resources?
AWS provides a robust ecosystem for SaaS providers to implement tenant isolation effectively. Let's explore some key isolation strategies.
Infrastructure Isolation
Isolating based on infrastructure helps separate tenants at the foundational level. There are several ways to achieve this in AWS.
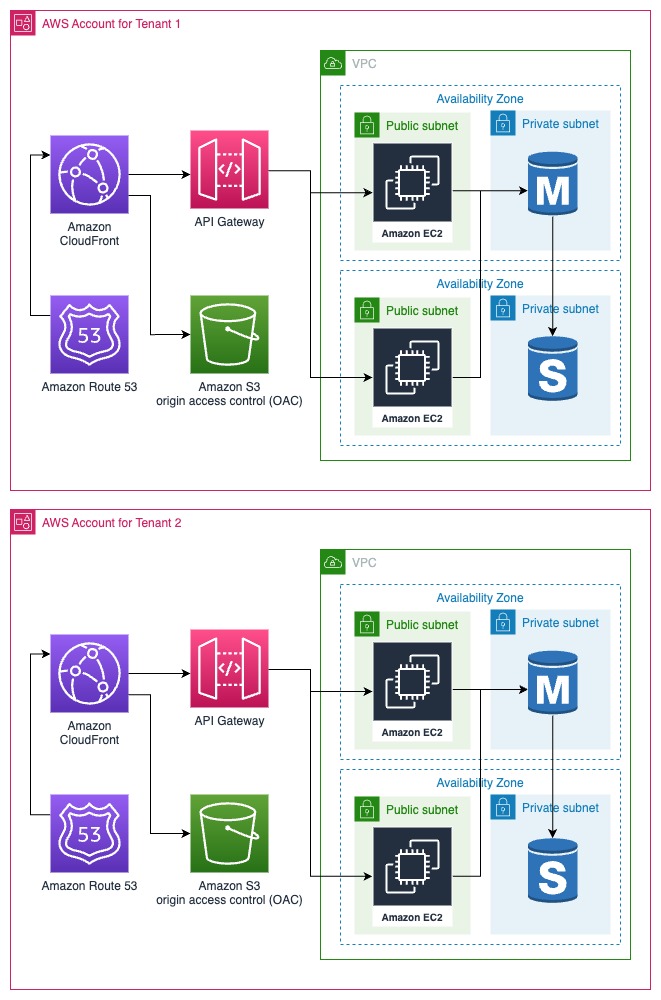
Account Isolation
Account Isolation stands out as one of the most straightforward strategies. It revolves around achieving comprehensive isolation by duplicating the entire resource stack for each tenant within an individual AWS account. Creating a dedicated AWS account for each tenant guarantees both resource and permission segregation. Additionally, it streamlines the process of tenant-level billing, providing clear financial separation.
However, it's essential to consider scalability and cost. As the number of tenants grows, this approach may become less practical. While account creation itself is free, duplicating the entire stack for each tenant can incur significant costs. Furthermore, automating the account creation process during tenant onboarding can prove to be a somewhat tedious task.
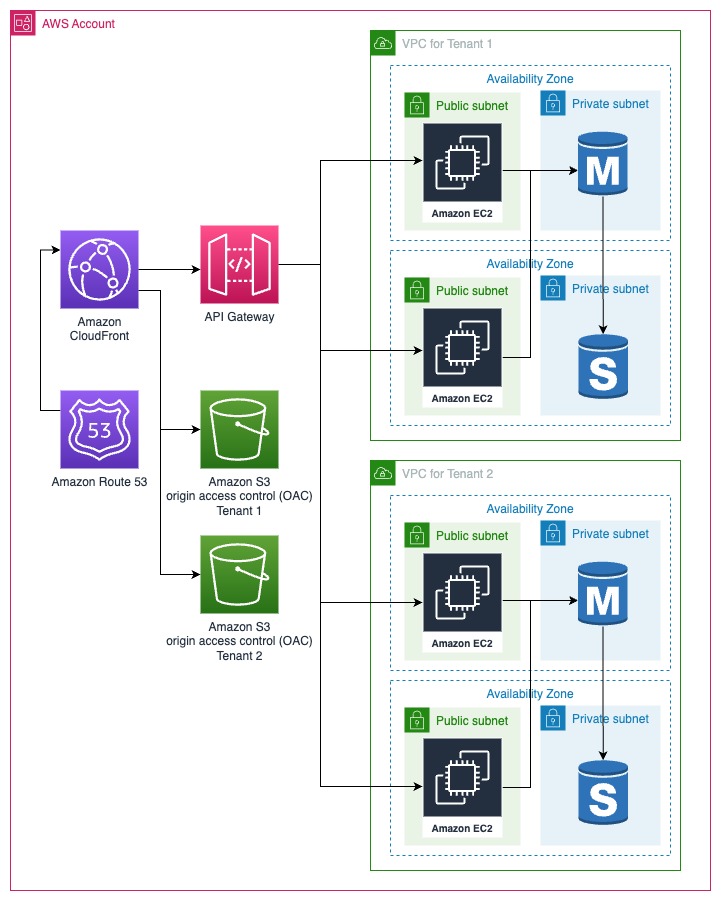
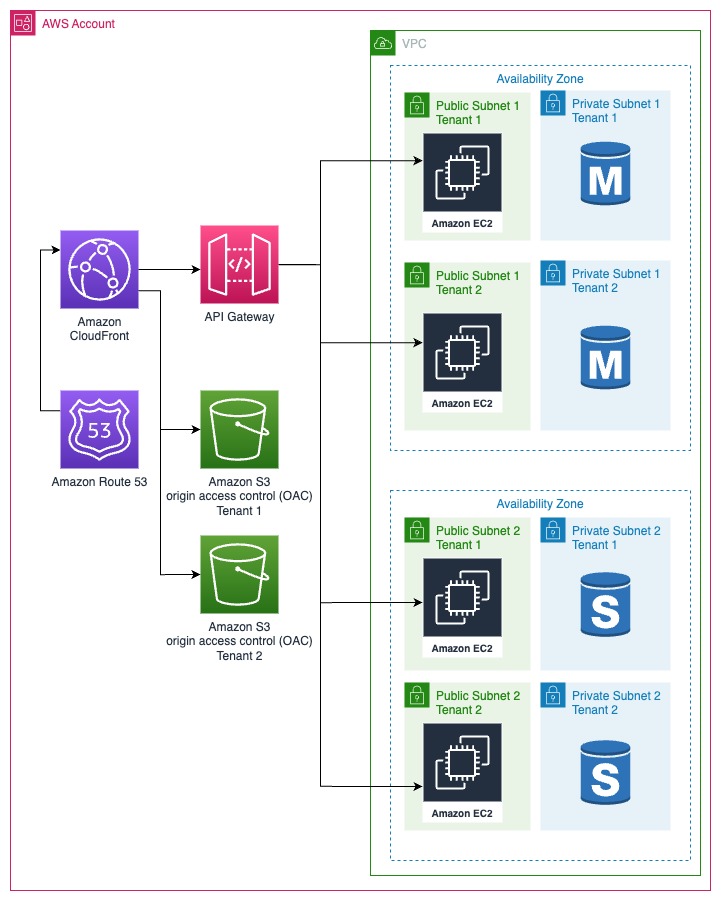
Network Isolation
Network Isolation is a strategy that capitalizes on key networking components within Amazon Web Services (AWS), such as Virtual Private Clouds (VPCs) and Subnets, to partition and segregate tenants effectively. As your tenant base grows, you can easily scale by adding more VPCs and Subnets to accommodate new tenants. Additionally, automating the process of provisioning and managing tenant-specific network resources is notably more straightforward compared to automating the provisioning of an entire account.
However, it's important to note that Network Isolation also introduces certain challenges, particularly in terms of accounting and billing. With multiple tenants sharing AWS resources, tracking and attributing costs to each tenant can become complex. This is where the need for precise accounting and resource attribution arises. To address these challenges effectively, consider implementing a robust tagging strategy. Tags are labels or metadata that you can associate with AWS resources. By applying tags to resources associated with each tenant, you gain granular control over billing and can generate detailed billing insights for each tenant.
Lets have a look at two different ways to achieve Network Isolation.
VPC Partitioning
This involves creating a separate Virtual Private Cloud (VPC) for each tenant, effectively isolating their network environments.
Subnet Partitioning
Subnet partitioning entails using subnets within a VPC to create network boundaries around tenant resources, providing fine-grained control over network traffic.
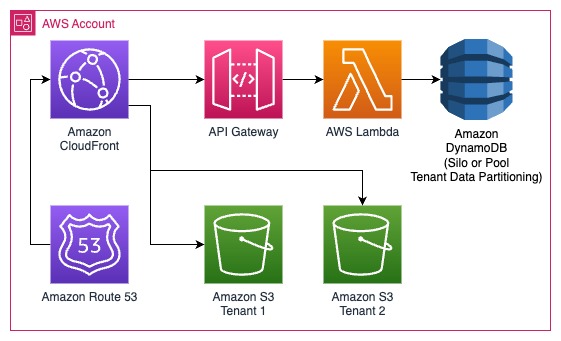
Serverless Isolation
Serverless computing (encompassing services such as AWS Lambda, AWS Step Functions, and more) offers a practical solution that eliminates the complexity of tenant specific provisioning altogether. These services are easier to provision and manage, making it a simpler and often more cost-effective solution as compared to provisioning dedicated and often under-utilized compute resources. In essence, Serverless computing liberates you from the intricacies of isolating compute resources. Instead, you can focus on implementing robust data isolation methods to attain comprehensive tenant separation.
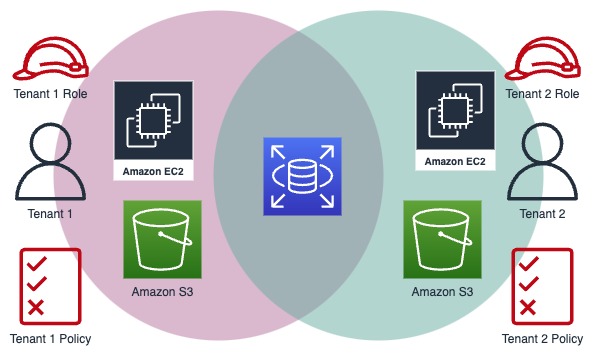
Policy Isolation
In a pooled (all shared resources) or bridge (some shared resources) model of multi-tenancy, it is essential to make sure each tenant can only access the resources they are allowed to access. Policy isolation revolves around controlling access and permissions to AWS resources. This requires a robust tenant identity system so you can identify the tenant inside the AWS eco-system and enforce the correct permissions.
This is done, for instance, by exchanging the web identity for a tenant identity token. This token can then be used to recognize a tenant and allow them to assume a specific IAM (Identity and Access Management) role. These IAM roles serve as the cornerstone for provisioning permissions tailored to each tenant's specific role within the system. For instance, you can create distinct roles such as "Tenant Admin" and "Tenant Viewer," each with its defined scope of access.
Policy isolation empowers SaaS providers with the precision needed to navigate the intricacies of shared resources, ensuring that each tenant accesses only what they are entitled to. It's a fundamental component in the arsenal of strategies for achieving comprehensive tenant isolation and maintaining the integrity and security of your SaaS application.
Conclusion
Isolating AWS resources for your multi-tenant SaaS application is not merely a best practice; it is an imperative step to ensure the security, compliance, and scalability of your SaaS offering. By understanding and implementing the diverse isolation strategies AWS offers, you can confidently steer your SaaS offering toward success in a competitive landscape.
AWS provides a wealth of tools and strategies to achieve robust tenant isolation. It's not just about having options; it's about harnessing the full potential of AWS to tailor your isolation approach to your unique requirements. With AWS, you have the flexibility to mix and match different isolation strategies based on your business needs and tenant personas.
As you navigate the dynamic SaaS landscape, remember that tenant isolation is not just a security measure; it's a strategic advantage. It opens doors to new business opportunities, empowers compliance, and positions your SaaS application as a leader in the industry.
So, embrace the power of AWS, explore its isolation strategies, and pave the way for your multi-tenant SaaS success. The journey may be complex, but with the right strategies and a commitment to excellence, your SaaS offering can thrive in the competitive world of multi-tenancy.



Top comments (0)