Virtual Private Cloud (VPC): A Comprehensive Guide
- Introduction A Virtual Private Cloud (VPC) is a logically isolated section of a public cloud where users can launch and manage resources in a secure environment. It allows organizations to define their own virtual network, including IP address ranges, subnets, route tables, and gateways, ensuring better security, control, and scalability over cloud resources.
VPCs are significant in the tech industry because they provide the benefits of a public cloud (scalability, cost-effectiveness) while maintaining the security and control of a private data center. They are widely used in cloud computing platforms like AWS, Google Cloud, and Azure for hosting applications, databases, and enterprise workloads.
- Technical Details Key Components of a VPC
- Subnets: A VPC is divided into subnets, which can be public or private.
- Internet Gateway (IGW): Allows public-facing subnets to access the internet.
- NAT Gateway: Enables private subnets to access the internet without exposing them directly.
- Route Tables: Defines rules for directing traffic between subnets and external networks.
- Security Groups (SGs): Acts as a virtual firewall for controlling inbound and outbound traffic at the instance level.
- Network Access Control Lists (NACLs): A stateless firewall for controlling traffic at the subnet level.
- VPC Peering: Connects multiple VPCs for resource sharing.
- VPC Endpoints: Allows secure connections to AWS services without using the internet.
Interaction Between Components
When a request is made from an EC2 instance in a public subnet to the internet, the following interactions occur:
- The request follows the route table associated with the subnet.
- The route table directs traffic to the Internet Gateway (IGW).
- The IGW allows outbound traffic, sending the request to the destination.
- The response is routed back to the instance through the same path.
For a private subnet instance accessing the internet:
- The request is sent to a NAT Gateway instead of the IGW.
- The NAT Gateway forwards the request to the internet, masquerading the private IP as a public IP.
The response follows the same path back to the private instance.
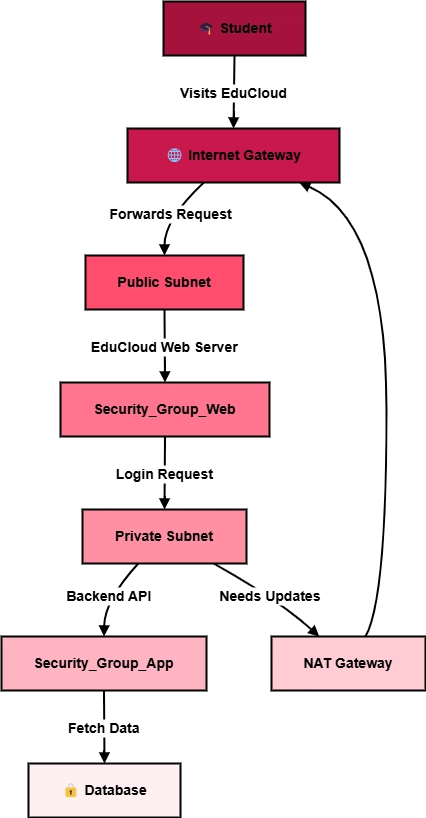
Real-Time Scenario: VPC for an Education Platform (EduCloud)
Analogy: University Campus
Imagine an educational institution with multiple departments. Each department has restricted access to certain facilities while some areas (e.g., the library) are publicly accessible. Similarly, a VPC in the cloud separates public and private resources.
Implementation in EduCloud
EduCloud, an e-learning platform, hosts:
- A public-facing website (Public Subnet)
- A secure backend API (Private Subnet)
- A student database (Private Subnet, no direct internet access)
- A NAT Gateway for backend servers to fetch updates
Traffic flow:
- Students visit EduCloud.com, which routes them to the public subnet.
- The web server communicates with backend services in the private subnet.
- The backend retrieves student data from the database in the private subnet.
Updates or patches are downloaded through the NAT Gateway.
Benefits and Best Practices
Advantages of VPC
✅ Enhanced security and isolation
✅ Custom IP addressing and network segmentation
✅ Better performance and latency control
✅ Secure VPN connectivity to on-premises data centers
✅ Scalability and flexibility for dynamic workloads
Best Practices
🔹 Use separate subnets for public and private resources
🔹 Implement least privilege security with Security Groups and NACLs
🔹 Enable VPC Flow Logs to monitor traffic and detect anomalies
🔹 Use NAT Gateway for secure internet access from private subnets
🔹 Restrict access to VPC resources using IAM roles
- Implementation Walkthrough (AWS VPC Setup) Step 1: Create a VPC
aws ec2 create-vpc --cidr-block 10.0.0.0/16
Step 2: Create Public and Private Subnets
aws ec2 create-subnet --vpc-id vpc-12345678 --cidr-block 10.0.1.0/24 --availability-zone us-east-1a
aws ec2 create-subnet --vpc-id vpc-12345678 --cidr-block 10.0.2.0/24 --availability-zone us-east-1b
Step 3: Attach an Internet Gateway
aws ec2 create-internet-gateway
aws ec2 attach-internet-gateway --vpc-id vpc-12345678 --internet-gateway-id igw-12345678
Step 4: Configure Route Tables
aws ec2 create-route-table --vpc-id vpc-12345678
aws ec2 create-route --route-table-id rtb-12345678 --destination-cidr-block 0.0.0.0/0 --gateway-id igw-12345678
- Challenges and Considerations Potential Challenges 🚧 Network Latency: Poorly configured routing can cause delays. 🚧 Misconfigured Security Rules: Overly permissive security groups can introduce vulnerabilities. 🚧 Costs: NAT Gateways and VPNs incur additional charges.
Solutions
🔹 Optimize subnet placement across Availability Zones.
🔹 Regularly review security rules and IAM policies.
🔹 Monitor VPC Flow Logs for unusual traffic patterns.
Future Trends
🔮 AI-Driven Security Monitoring: Cloud providers are integrating AI to analyze VPC traffic for threats.
🔮 VPC Service Meshes: Future architectures will seamlessly integrate Kubernetes and VPCs.
🔮 5G & Edge Computing: VPCs will extend to edge locations, enhancing performance for IoT applications.Conclusion
VPCs play a crucial role in securing and optimizing cloud infrastructure. By implementing best practices like proper subnet planning, route table management, and security configurations, organizations can achieve scalable, secure, and efficient cloud networks.


Top comments (0)