Haven’t we all suffered with passwords for long enough? Many believe that passkeys are the new password, and they can be more secure and easier to use if implemented correctly. In this article, we’ll introduce the technology behind passkeys, so you can start taking advantage of them. In future articles, we’ll go into more technical depth on implementing passkeys in your organization.
What Is a Passkey?
Passkeys are a method of authentication that uses asymmetric encryption rather than relying on a shared secret like a password. With a password, the user and the company will both remember the same password. Passkeys store a private key on the user’s device, and the company stores a public key. These keys are long strings of characters that are created together in such a way that if you have one, it’s almost impossible to figure out the other, but they work together to prove something, such as that you are who you say you are. As long as we keep one secure (the private key), the public key can be, well, public. If someone steals your public key from a company, they still can’t access your account if they don’t also have your private key. Since there is less value in trying to steal your public key (that replaced your password) from a company, fraud (such as phishing) can be reduced in many ways.
To illustrate how powerful passkeys are compared to passwords, I’ll contrast how the two approaches work to protect an imaginary account that you have at a bank. The details will be simplified but include the important points. There are two essential parts of authentication: the first is creating an account (registration), and the second is accessing your account later (authentication).
Creating and Accessing Accounts with Passwords
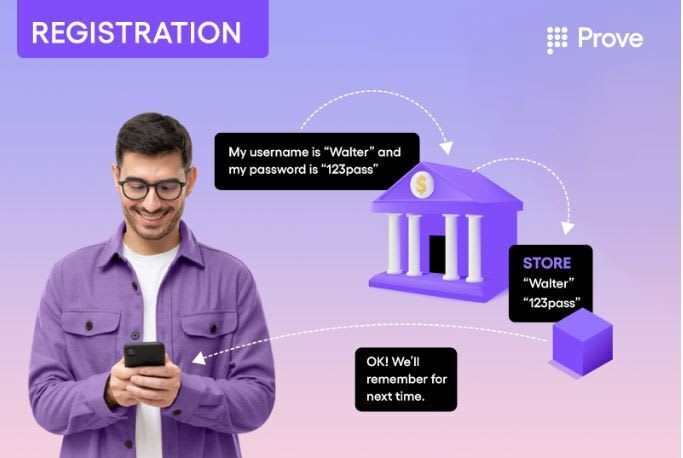
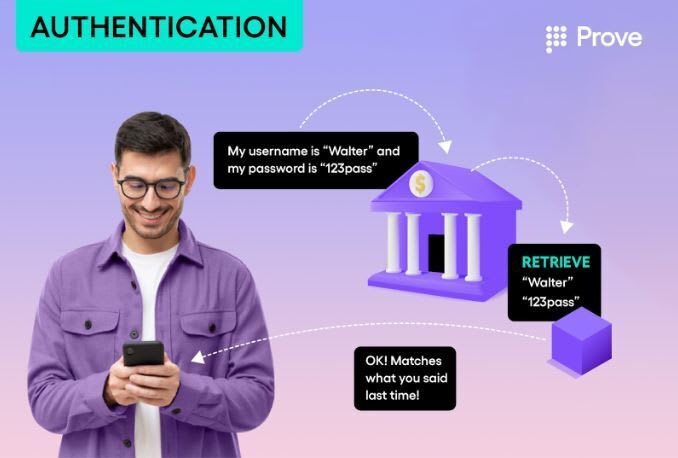
First, let’s review passwords. On registration, your account is created, and you tell your bank what your username and password is. You and your bank both agree never to share that password with anyone else, so no one else can access your account. Later, when you want to access your account, you authenticate yourself by telling the bank your username and password. The bank compares it to what you told them initially– and if it matches, you can access your account.
I don’t need to go into many details about how this can be problematic; you’ve likely experienced many downsides yourself. You might forget the password; someone can steal the password from you; a malicious third party can steal your password from the bank; a malicious third party can steal your password from your password manager; someone can try to change your password with the company without your knowledge. There are MANY ways passwords can be compromised.
Using passkeys that utilize asymmetric encryption helps solve some of the core problems of passwords. As noted earlier, asymmetric encryption uses both a public and a private key. Not surprisingly, these keys are used to encrypt data. If you have a pair of keys, you’ll always keep the private one a secret, but you can share the public one with anyone. Then, if I want to send you a message that no one else can read, I encrypt it with your public key. The message can only be read if you decrypt it with your private key. Because the private key is secret, no one else but you can read the message. Another feature is that when you send me a message, you can encrypt it with your private key. When I decrypt it with your public key, I know the message HAD to come from you because there’s no way it could be decrypted any other way.
Next, we’ll talk through how these keys are used together to log into your account and show how they prevent the problems we have with passwords.
Creating and Accessing Accounts with Passkeys
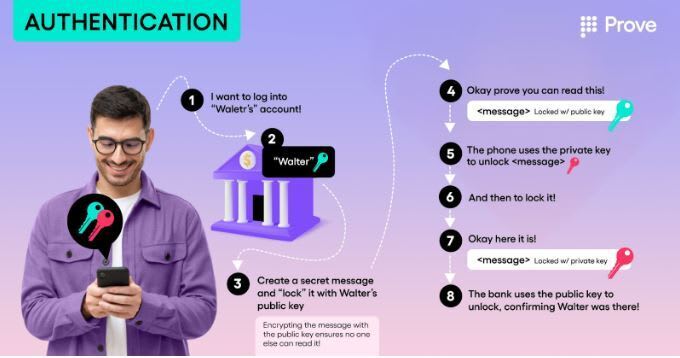
Okay, back to passkeys: When you create an account with your bank, the flow is slightly different. Your device (mobile phone, laptop) creates a private/public key pair. The private key is stored securely in your device, and you send the matching public key to your bank, which stores it. When you return to access your account later, you tell the bank who you are (username). The bank generates a secret message “locked” (encrypted) with your public key and sends it back to your device. No one else can read this message because it was locked with your public key.
Next, your device unlocks the message with your stored private key and re-locks it with the private key, adding additional info and doing other checks simultaneously. Because the message is encrypted with your private key, anyone who can decrypt it with your public key knows it came from your device. The locked message is sent back to your bank, which uses your stored public key to unlock the message. If the message is the same as the secret message generated at the start of the process, it must be you and only you logging in, so you can access your account.
Keeping the Private Key Private
Let’s talk about this private key. Similar to a password, it’s important to keep it private. Therefore, your device (a mobile phone, a computer, etc.) stores the private key in a special place to keep it secure and prevent access from anyone (human or otherwise) who shouldn’t have access to it. When passkeys were first deployed, this was usually a hardware key (similar to a USB thumb drive) that you’d plug into your laptop; it became imperative not to lose this key.
These days, many devices have secure storage built in to hold unique data such as these keys. The secure storage is usually protected with biometrics (such as Face ID or fingerprint) but could also be protected by a PIN. But, unlike a password, it’s not easy to guess. And because it never leaves your device (although I’ll contradict myself in a couple of paragraphs), it’s very difficult for someone to try to steal it.
The User Experience of Passkeys
As a user, the experience of using passwordless generally feels the same as using a password manager, at least for everyday needs. Here’s an example of a time when it will feel different: Let’s say you are using a borrowed laptop that doesn’t have your password manager on it. To log into an account, you can look up the username and password in your password manager on a different device, and enter it in on the borrowed device. The password might be long and complicated, and it might be somewhat awkward, but it’s possible. You can’t do that with passkeys: the private keys belong on one device, and they are complex and lengthy enough that you can’t just open it up, look at it, or copy it over elsewhere. This means that it’s crucial to think about where your passkeys are created/living in a way that we don’t have to think about passwords.
This difficulty in “copying” private keys to other devices is intended to be a security measure, but it has been one of the things preventing organizations from adopting passkey authentication so far. We mentioned hardware keys to store private keys earlier– that’s helpful because you can take that key and plug it into, say, a different laptop and access the credentials. But now that more devices can store these keys built into them, what happens if you lose the device you created your credentials on? What happens if you get a new one? What if the device gets stolen? Securely replacing those credentials is a hard thing to do without passwords. We’ll talk more about that in a future post, but spoiler: Prove has thought a LOT about handling many of these challenges and has a solution.
Passkeys can now be stored in password managers, such as 1Password in Apple’s iCloud keychain, which is used in devices like iPhones, iPads, and MacBooks. These are referred to as synced passkeys. Syncing passkeys addresses the problem of credentials living on one device (referred to as device-bound passkeys) by storing the private keys in a password manager, which can be synced to multiple devices via the cloud. We expect to see more organizations making passwordless authentication an option now, as some of the biggest challenges are addressed with the availability of synced passkeys. While this is an extraordinary, huge step forward, it’s not the entire solution: storing private keys in a password manager makes it easier to adopt but also weakens the security of the credentials. The credentials can be compromised via the password manager, so it’s not entirely as secure as device-bound passkeys stored in a trusted module on a single device.




Top comments (0)