Hi friends!✌️
In this article, I want to share a solution to the problem of forwarding http traffic through socks5 to rotate ip-addresses, this can be useful when parsing, testing or bypassing DNS / IP-based blocking.
What is SOCKS5?
SOCKS is an Internet protocol that exchanges network packets between a client and server through a proxy server. SOCKS5 optionally provides authentication so only authorized users may access a server. Practically, a SOCKS server proxies TCP connections to an arbitrary IP address, and provides a means for UDP packets to be forwarded.
SOCKS performs at Layer 5 of the OSI model (the session layer, an intermediate layer between the presentation layer and the transport layer). A SOCKS server accepts incoming client connection on TCP port 1080, as defined in RFC 1928.
Required dependencies
Linux/Unix (For Windows, some differences will be characteristic (see the corresponding sections in the installation and configuration items))
TOR Client - Tor is free and open-source software for enabling anonymous communication. It directs Internet traffic through a free, worldwide, volunteer overlay network, consisting of more than seven thousand relays, for concealing a user's location and usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult to trace the Internet activity to the user. This includes "visits to Web sites, online posts, instant messages, and other communication forms". Tor's intended use is to protect the personal privacy of its users, as well as their freedom and ability to conduct confidential communication by keeping their Internet activities unmonitored.
Privoxy - is a non-caching web proxy with advanced filtering capabilities for enhancing privacy, modifying web page data and HTTP headers, controlling access, and removing ads and other obnoxious Internet junk.Can be used both for single device protection (by installing it on device you want to protect) and newtork protection (by configuring network devices to use privoxy server as proxy).
Privoxy is Free Software and licensed under the GNU GPLv2.
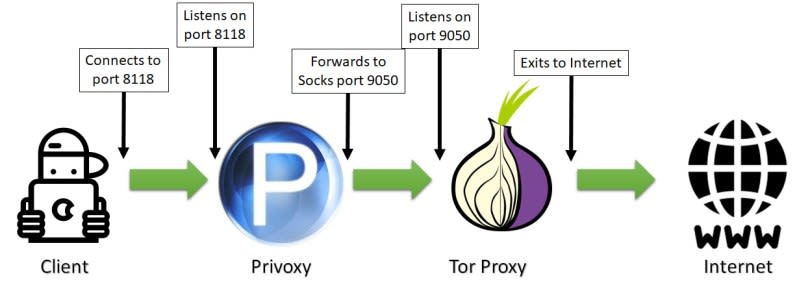
Proxy chain will be:
Ready? then go ahead
First step it's install tor
sudo apt update
sudo apt install tor
After do not forget to restart the service
sudo /etc/init.d/tor restart
Next you should create new password
tor --hash-password <enter your password here>
Save the resulting hash in
./etc/tor/torrc
In the same place, we will uncomment the following lines:
SOCKSPort 9050
HashedControlPassword 'your hashed passsword obtained earlier here'
CookieAuthentication 1
Restart the service to apply the changes
sudo /etc/init.d/tor restart
Hint
To regulate the speed of changing nodes (by default, this is 10 minutes)
MaxCircuitDirtiness 'int'
int is an integer greater than or equal to 10 responsible for the node change interval in seconds
Ok, it's time to install your reverse proxy
sudo apt install privoxy
The config file can be found at the following path:
/etc/privoxy/config
Privoxy needs to know that its follower in chain is a socks5 proxy which listens on 9050 port. Again, supposing that TOR is running on same host, Privoxy config file will be configured including following line (including last dot):
forward-socks5t / 127.0.0.1:9050 .
Restart
sudo /etc/init.d/privoxy restart
To check the readiness, you can run a request for httpbin.org
e.g.
import requests
def check_ip():
ip = requests.get('https://httpbin.org/ip')
return ip.text
if __name__ == '__main__':
result = check_ip()
print(result)
Done?
Congratulations!
Note
Warning! Please read this article carefully.



Top comments (0)