https://docs.mitmproxy.org/stable/howto-install-system-trusted-ca-android/
Using mitmproxy, it's possible to analyze HTTP(s) communication made by an application running in android emulator.
mitmproxy setup
To ease mitmproxy running, I'm using the following docker-compose.yml:
External mitmproxy docker volume needs to be created with the following command:
$ docker volume create mitmproxy
Once done, you can start mitmproxy:
$ docker-compose up
The mitmproxy web interface is available at http://localhost:8081
Once started, mitmproxy will generate a certificate which you have to retrieve.
$ mkdir /tmp/mycert
$ pushd /tmp/mycert
$ docker run --rm -u $(id -u) -v $(pwd):/out -v mitmproxy:/in alpine cp /in/mitmproxy-ca-cert.cer /out
$ cp mitmproxy-ca-cert.cer $(openssl x509 -inform PEM -subject_hash_old -in mitmproxy-ca-cert.cer | head -1).0
Android emulator setup
Proxy settings
To use your mitmproxy, you need to configure proxy settings in android emulator

Once you have done this settings, you can't anymore browse HTTPS webpage:

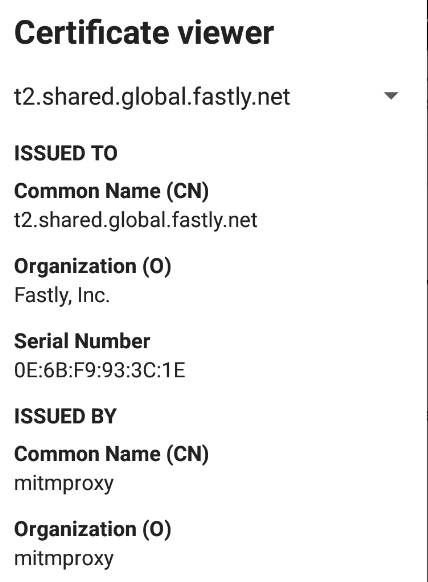
You need to install your generated mitmproxy certificate.
Permanent certificate installation using ADB
Please note that permanent certificate installation could only be done with a NON google play images.

Use the following commands to copy certificate to emulator (replace c8750f0d by the hashed name of mitmproxy-ca-cert.cer
$ adb root
$ adb shell "mount -o rw,remount /"
$ adb push c8750f0d.0 /system/etc/security/cacerts
$ adb shell "chmod 664 /system/etc/security/cacerts/c8750f0d.0"
$ adb reboot
Certificate installation on google play images
Once proxy is set, you need to go to mitm.it

And then click to install your certificate.
After certificate is installed
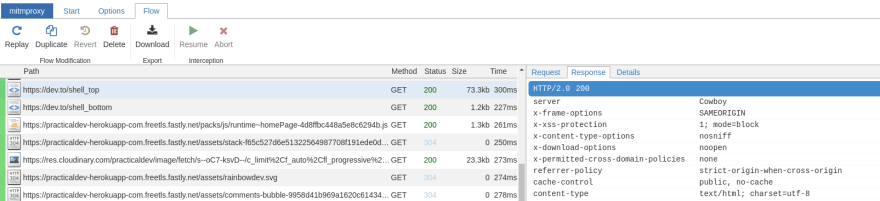
And at http://localhost:8081, you will have all your HTTP requests:
For advanced usage, please refer to mitmproxy homepage



Top comments (0)