__
What is VPC?
- Virtual Private Cloud (VPC) enables you to launch AWS resources into a virtual network that you've defined. This virtual network closely resembles a traditional network that you'd operate in your own data center, with the benefits of using the scalable infrastructure of AWS.
Amazon VPC concepts
- Virtual private cloud (VPC) — A virtual network dedicated to your AWS account.
- Subnet — A range of IP addresses in your VPC.
- CIDR block —Classless Inter-Domain Routing. An internet protocol address allocation and route aggregation methodology.
- Route table — A set of rules, called routes, that are used to determine where network traffic is directed.
Internet gateway — A gateway that you attach to your VPC to enable communication between resources in your VPC and the internet.
Security groups: Acts as a virtual firewall to control inbound and outbound traffic for an AWS resource, such as an EC2 instance. Each VPC comes with a default security group, and you can create additional security groups. A security group can be used only in the VPC for which it's created.
Network ACLs: An optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of your subnets.
VPC endpoint — Enables you to privately connect your VPC to supported AWS services and VPC endpoint services powered by PrivateLink without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. Instances in your VPC do not require public IP addresses to communicate with resources in the service.
- To understand what an S3 VPC endpoint is, we first need to know what problem it solves.
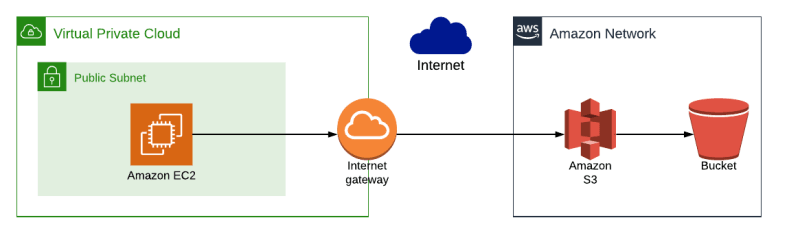
- Imagine we want to get access to S3 from an AWS resource. In the example below, we have an EC2 instance that needs to copy a file from an S3 bucket:
- This works, because:
- the EC2 instance is in a public subnet, so has access to the internet
- therefore the EC2 instance can reach the AWS S3 URL to copy the file from the S3 bucket
The problem with S3 access from a private subnet
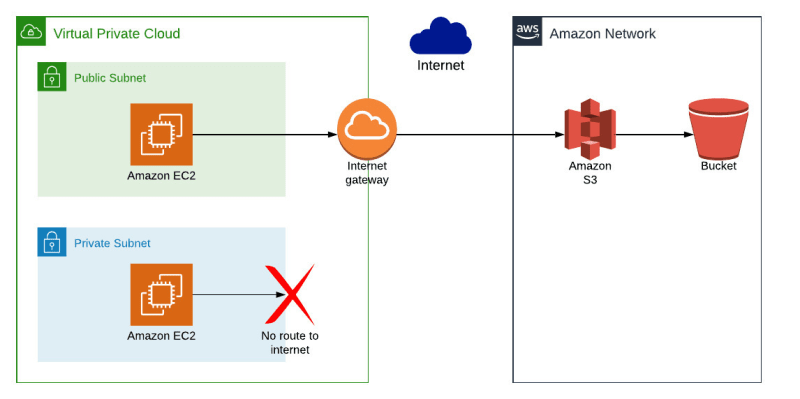
- Where this starts to fall down, though, is when we need to access S3 from an EC2 instance in a private subnet, as in the example below:
- This doesn’t work, because:
- the EC2 instance is in a private subnet, so has no internet access
- therefore the EC2 instance can’t reach the AWS S3 URL, and the request will time out
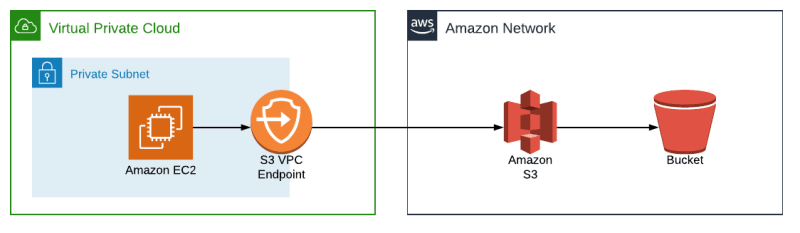
- S3 VPC endpoints solve this problem
- An S3 VPC endpoint provides a way for an S3 request to be routed through to the Amazon S3 service, without having to connect a subnet to an internet gateway.
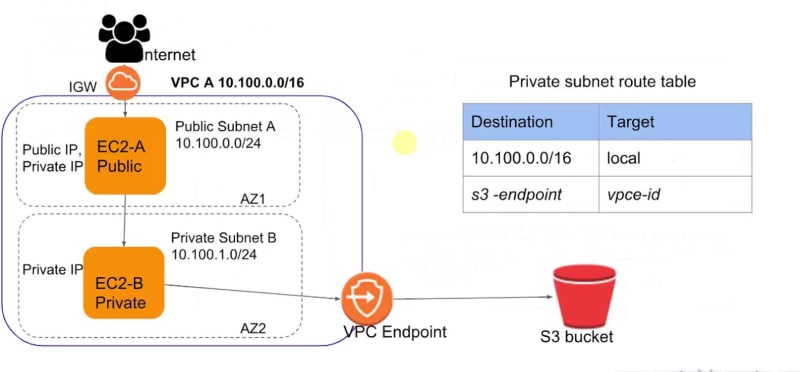
How can we access our s3 bucket if our instance is present inside a private subnet of VPC?
- If your instance is in private subnet of VPC then: You need to have a NAT device running in public subnet. So that the instance in private subnet of VPC can access internet via NAT and access S3. But there may be a lots of latency , so in that case we can use VPC endpoint.
- Through VPC endpoint we can access our s3 bucket directly through a private instance present in a private subnet of VPC [ just like an internal tunneling ].
Lets do a Setup as per above diagram
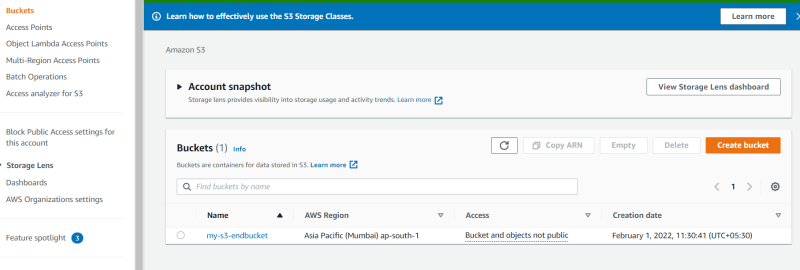
1. Create a s3 bucket
- Search for s3
- Click on Create Bucket and create a s3 bucket
- Follow this link :- https://dev.to/shankarsurya035/what-is-s3-bucket-how-to-mount-a-s3-bucket-in-a-drive-network-drive-3d4f
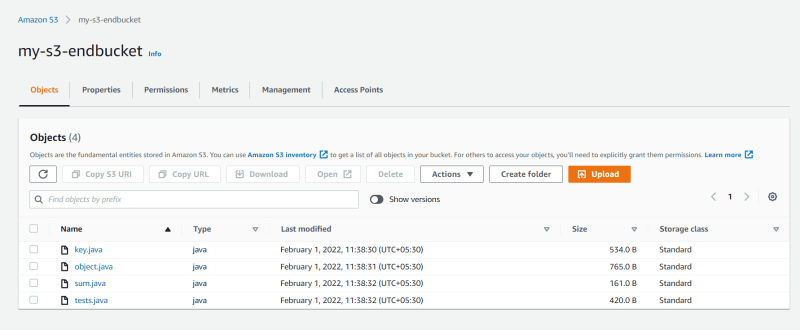
-Upload some files inside that bucket.
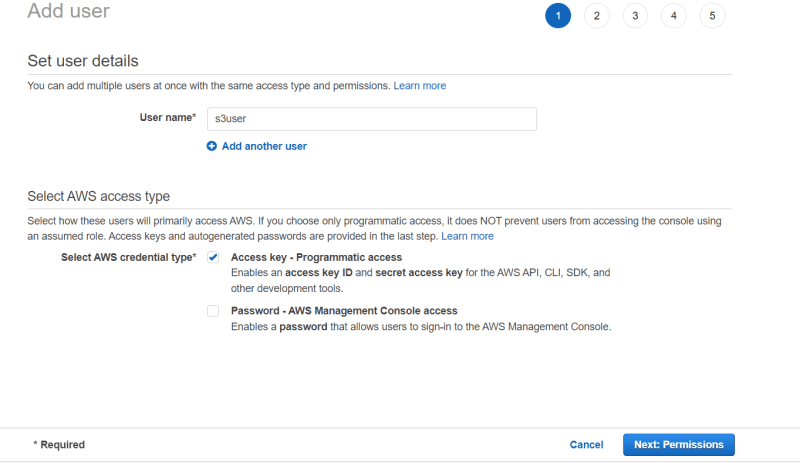
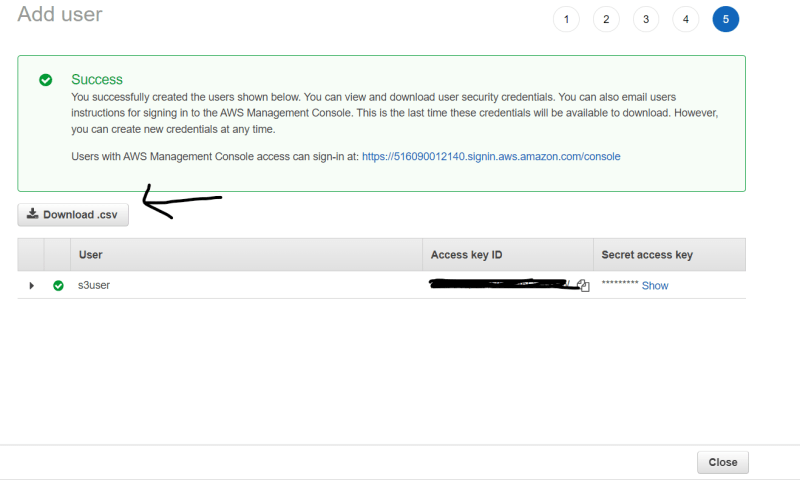
2. Create a IAM User
- Search for IAM role
- Click on user and Add User
- Name it "s3user"[or your wish]
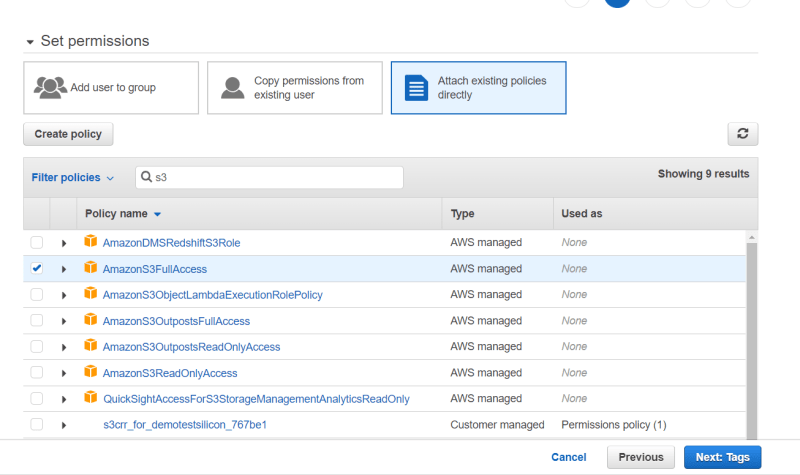
- grant access key permission , next permission.
- select attach existing polices
- select s3 full access ,next tag.
- Download .CSV file [ here access and secret keys are present]
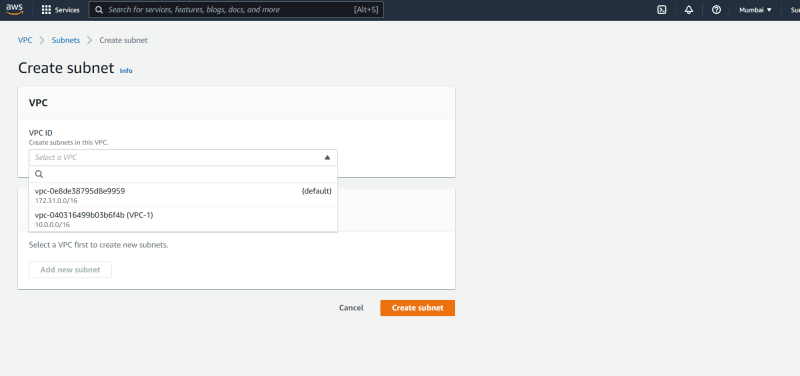
3. Create a VPC
- Search for VPC
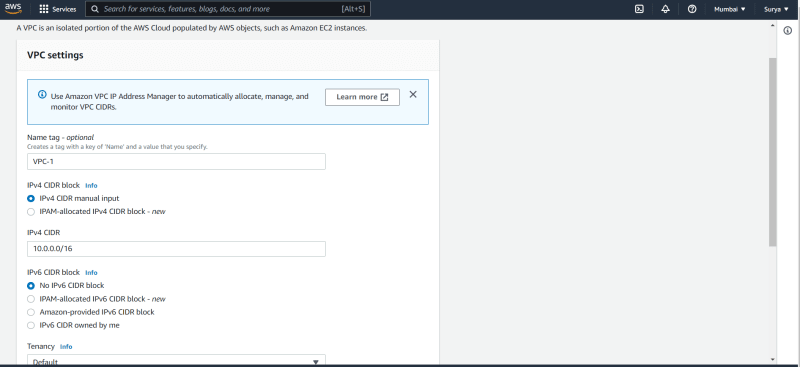
Click on create VPC
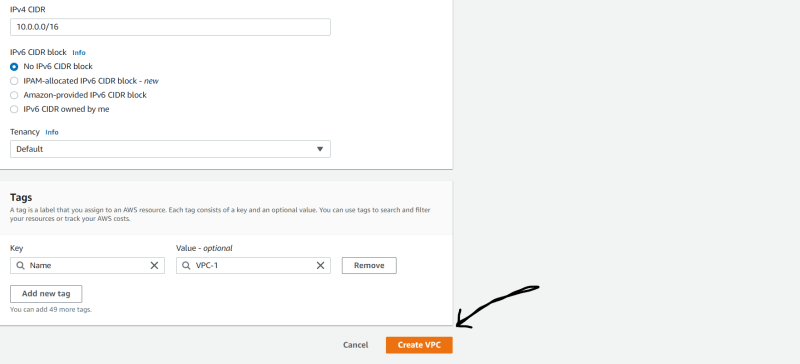
Name it VPC-1,
CIDR range :- 10.0.0.0/16
- Create VPC.
4. Create Subnets inside that VPC
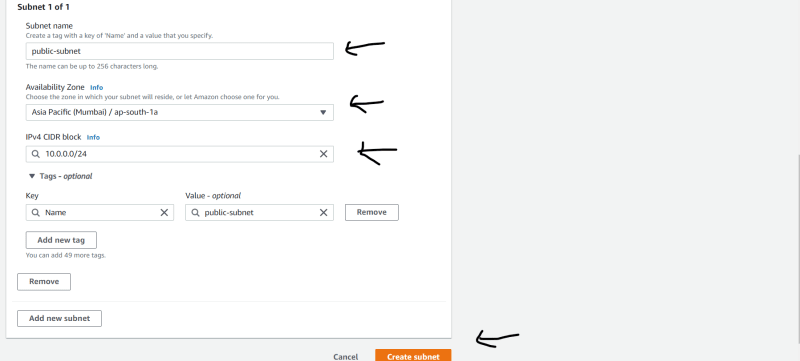
- Create a PUBLIC SUBNET
- Click on subnet and create subnet
- Choose Your VPC
- Name :- public subnet
- choose your zone
- Give a CIDR range to it
- Create.
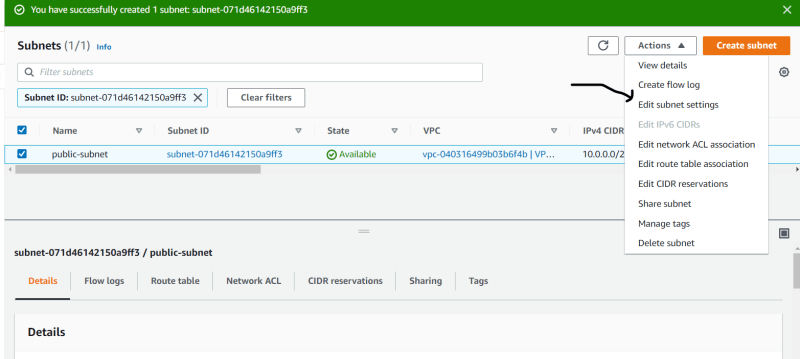
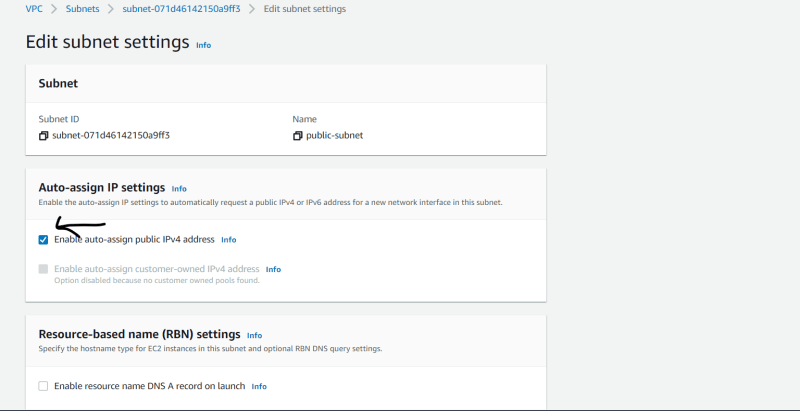
- Click on subnet setting and enable auto assign public IP.
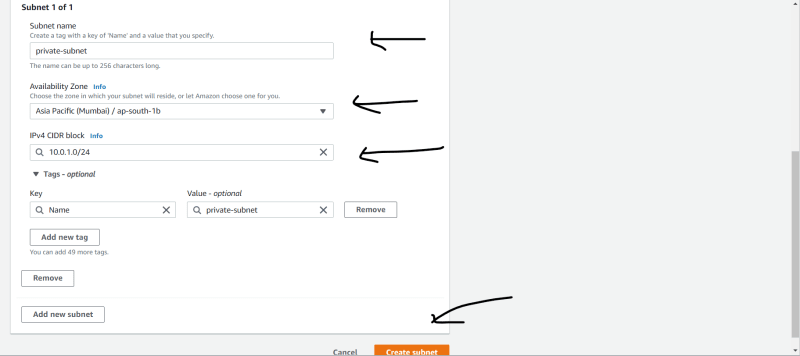
- Create a PRIVATE SUBNET
- Choose Your VPC
- Name :- private subnet
- choose your zone
- Give a CIDR range to it
- Create.
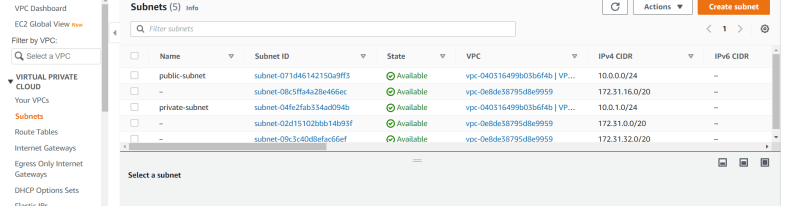
- Here Two Subnets Are
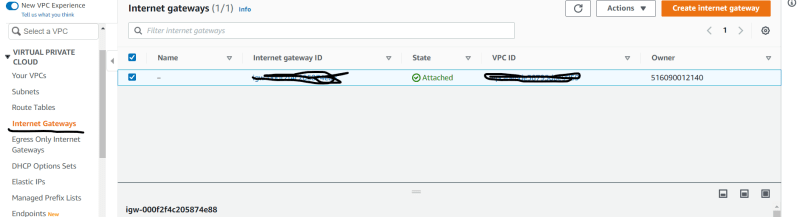
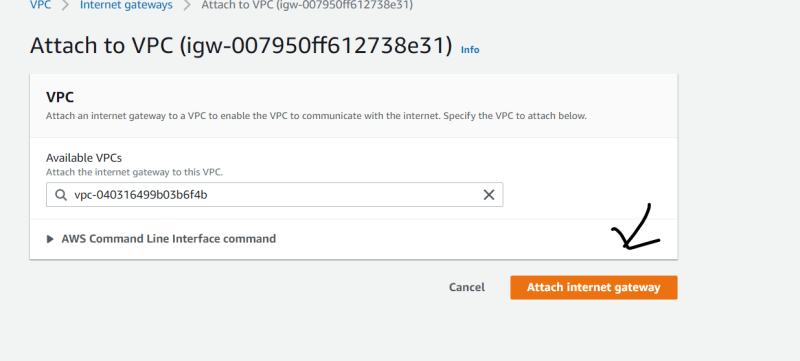
5. Create a Internet Gate way [igw]
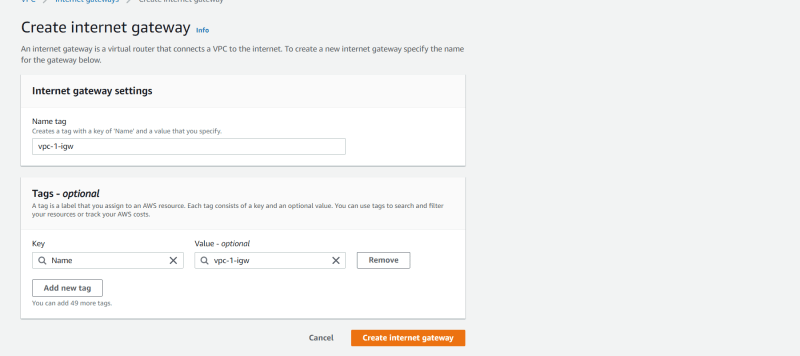
- Select Internet gateway
- Create igw and name it.
- Attach it to your VPC
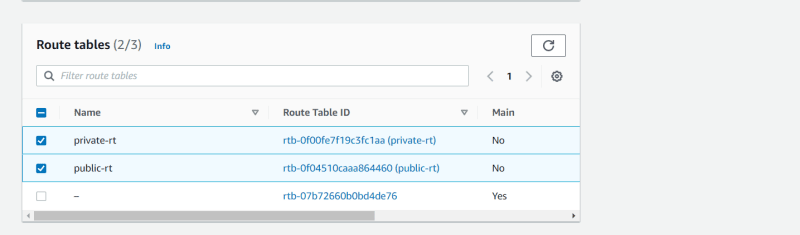
- Now we have to create Routes table with Subnets Association.
- Routes For Public Subnet
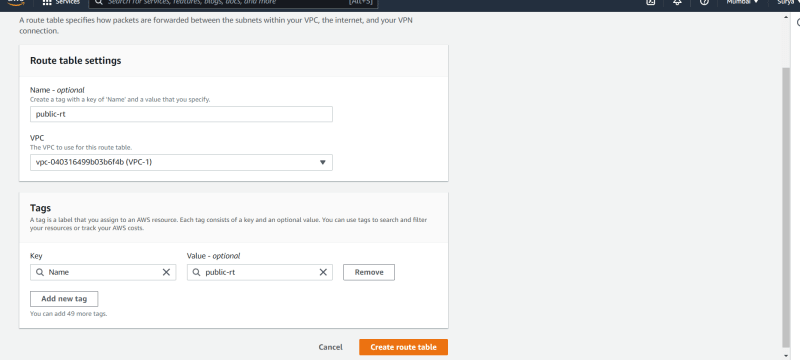
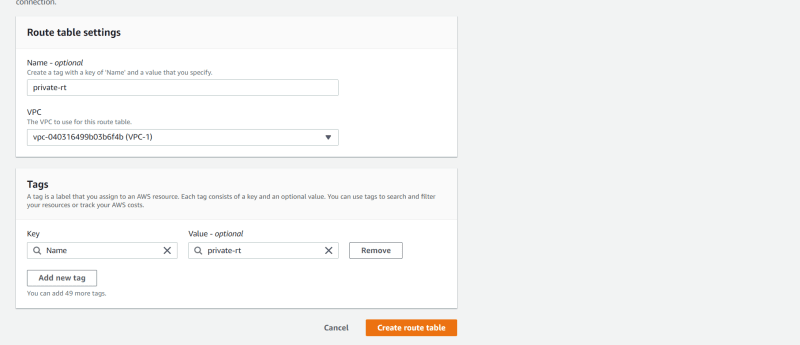
- Click on Create Routes table.
- Create routes table for public subnet
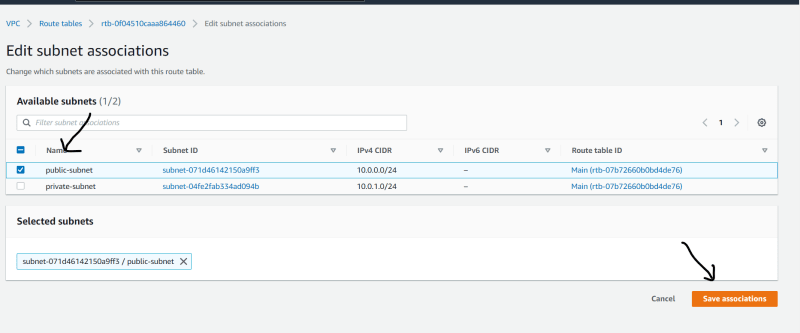
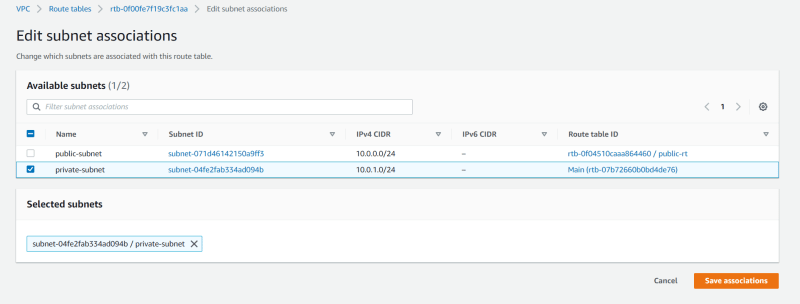
- Associate That private subnet to it
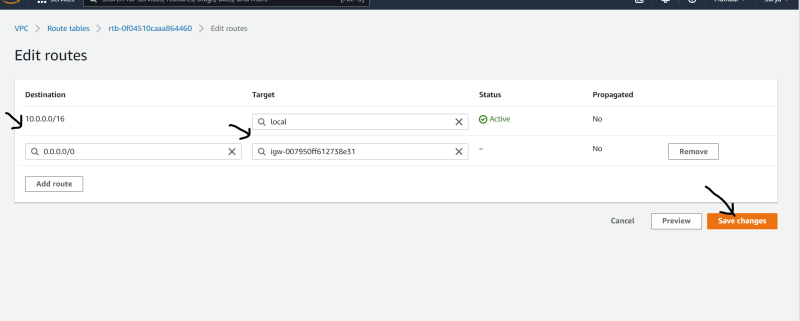
- Then Edit Routes , give a gate way path to the internet.
- Routes For Private Subnet
- Click on Create Routes table.
- Create routes table for private subnet
- Associate That public subnet to it
- Now as we want to restrict internet in our private subnet, so we don't give any internet routes path to it.
6. Lets Deploy Server/instances inside those Subnets
Public server
- Search for Ec2
- Click on Launch instance
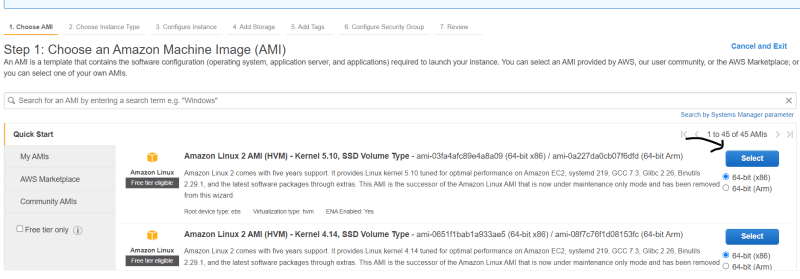
- Launch Amazon linux 2 AMI
- Select T2micro [free version]
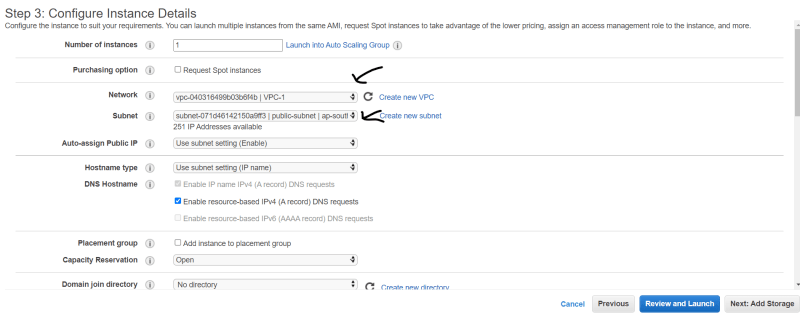
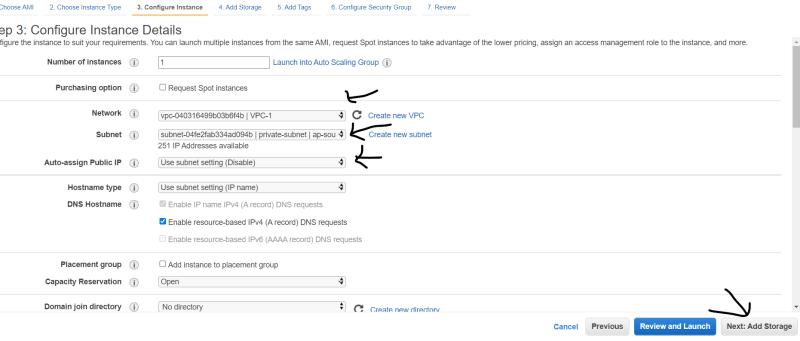
- On step-3 :- Select Your Vpc , public subnet.
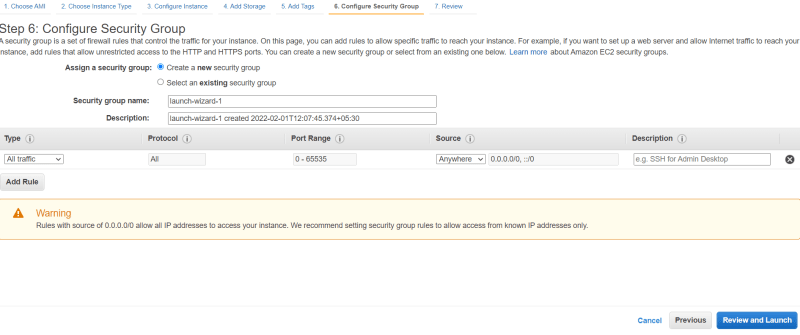
- On security group select All traffic , Anywhere [ Its not a best industry practice ].
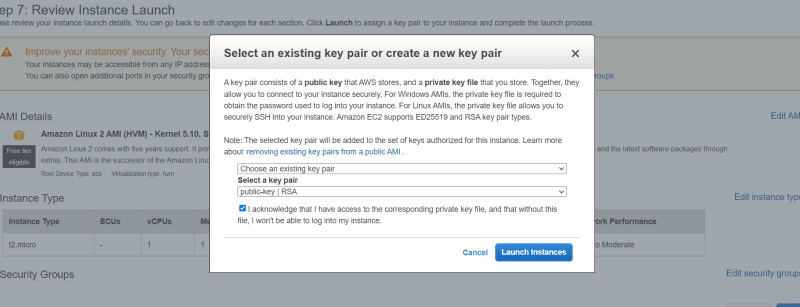
- Click next and download key pairs.
Private server
- Click on Launch instance
- Launch Amazon linux 2 AMI
- Select T2micro [free version]
- On step-3 :- Select Your Vpc , private subnet.
- Launch it and download key pairs.
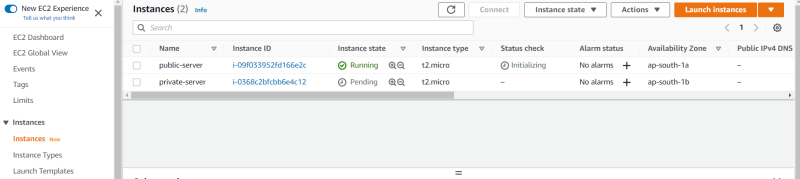
Here are Two servers
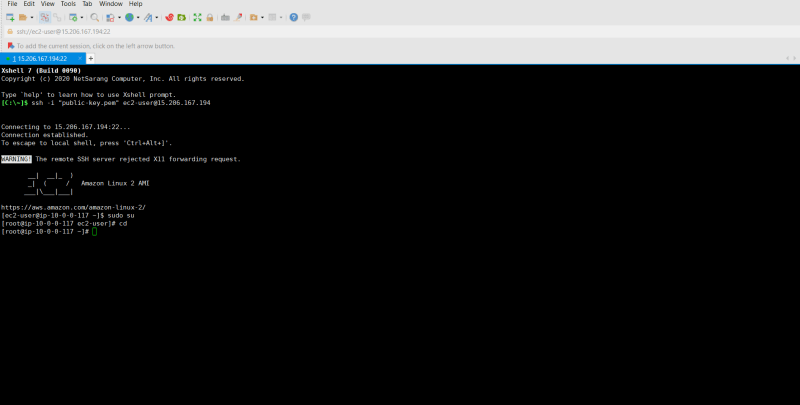
Now lets connect our public server through Xshell and try to access s3 bucket using internet
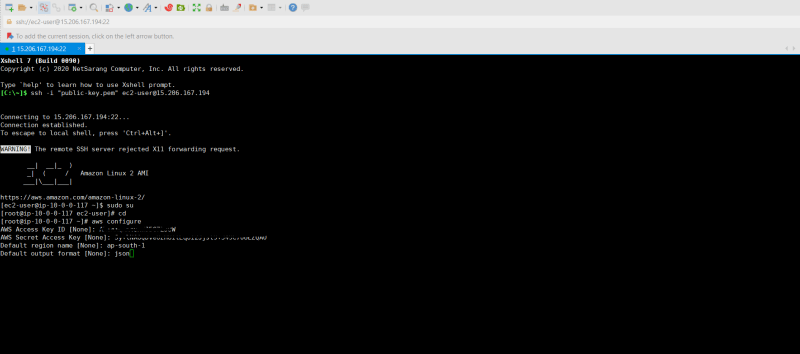
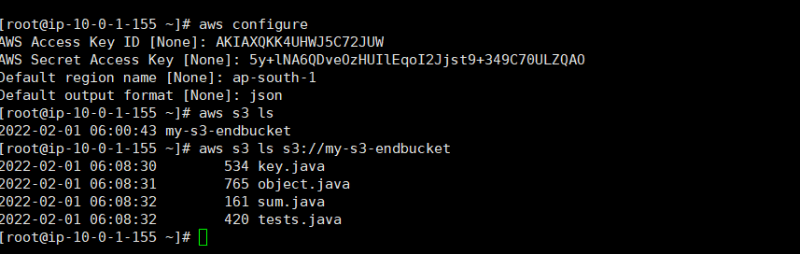
Go to root user and type aws configure
copy paste those IAM secret and access keys created earlier.
Type your region name and output format (example:-json,table).
- Type aws s3 ls [To list out your s3 buckets].
- Type aws s3 ls s3://Your bucket name [To list all files inside that bucket]
- Here we Successfully Access our s3 bucket through our Public server
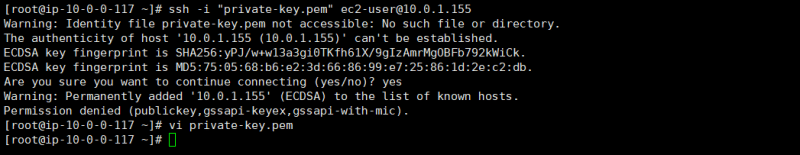
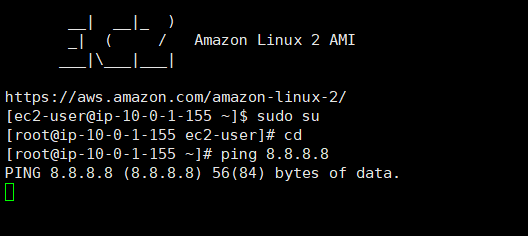
- Now we cannot Directly connect to our private server because that server don't have any public IP, we can only able connect to our private server through our public server [ inside our public server]
- Connect to public server , and now try to connect private server inside it.
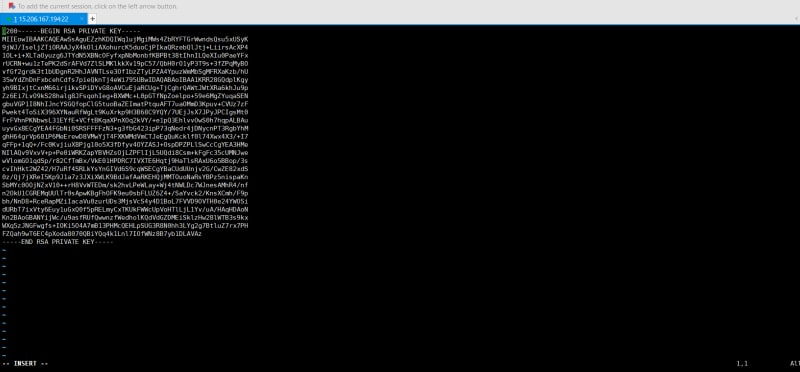
- Create private key file by vi command , paste the private keys keys , click esc shift+:wq to save
- Give read write permission to it by chmod command
- Now try to ssh into it You will able to connect
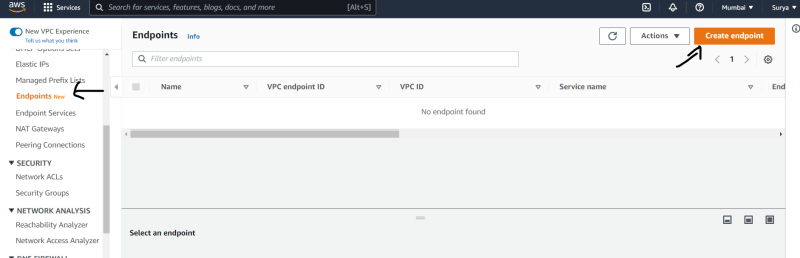
Inorder to access to our s3 bucket through private instance we need to setup a VPC end points
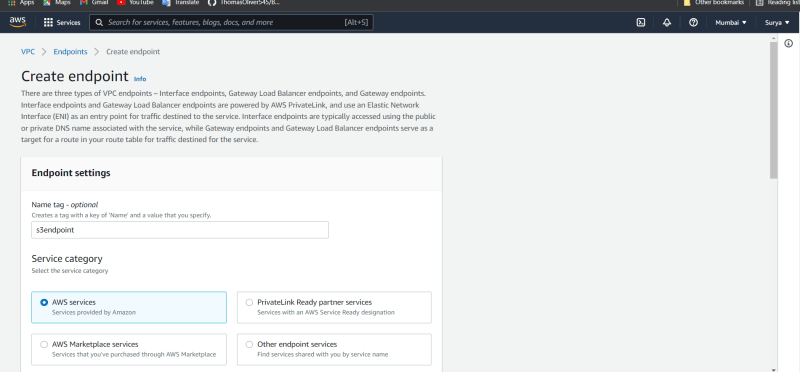
- Click on endponits , Create endpoints.
- Name it
- Select AWS services catagory.
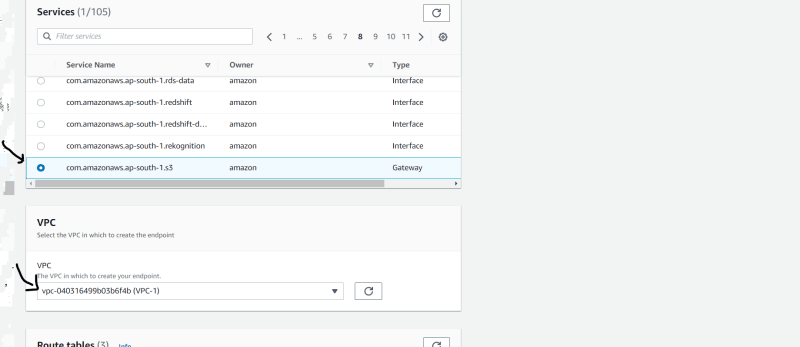
- select Your services , vpc and routes table
- Create endpoint.
- Now you can Able to access s3 bucket without connecting to the internet through private instance.

![Cover image for VPC [ Virtual Private Cloud] Setup & VPC Endpoints](https://media2.dev.to/dynamic/image/width=1000,height=420,fit=cover,gravity=auto,format=auto/https%3A%2F%2Fdev-to-uploads.s3.amazonaws.com%2Fuploads%2Farticles%2Fvvis1wii3i92cpzp65vb.png)




Top comments (0)