As the internet has become an integral part of our lives, our need for online security also became vitally important. In an attempt to protect sensitive data and keep anonymity while surfing the internet, users opt for secure ways of accessing the web. A proxy is a web server that allows users to view websites anonymously.
Open proxy servers became more popular these days thanks to their high variability of offered IP addresses and easy setup process that does not require specific technical knowledge.
What is an Open Proxy?
An open proxy is a computer program that allows users to access a remote server through another machine. The site owner doesn’t know who visited the website or what they did while accessing it.
Open proxies hide the identity of the person connecting to the internet. Because open proxies are available for general public access and lack internet security regulations or connection rules (they do not check, encrypt, or filter data or content that comes into the server) open proxies are often used by malicious third parties that mask their true nature under fake IP addresses.
What is the Use of Open Proxy?
There are a few reasons why a user wants to use an open proxy server:
- To protect (partially, because an open proxy logs users’ requests) a user’s identity while visiting websites;
- To access restricted websites on a local network or access content in different geolocations;
- To improve user experience by utilizing caching functions when surfing the web.
Advantages of Open Proxies
By masking a true IP address, open proxies make it difficult for cybercriminals to intercept and steal private data while browsing the web.
Privacy and Anonymity
Open proxies are accessible without restriction to all internet users who want to remain anonymous and secure their private information. Most public VPNs work through open proxies hiding users’ IP addresses from web servers.
High Availability
Widely available, mostly free, and easy-to-handle open proxies do not restrict their use so everyone can easily access the internet through open proxies, avoid geo and content blocks, leave messages, and stream media.
Disadvantages of Open Proxies
You must have learnt it by now – nothing is ever really free online. You always pay for services in one way or another. Once collected, the unencrypted information can be sold to marketing companies (if you are lucky). By using such valuable data marketing specialists can arrange highly effective marketing campaigns.
The main shortcoming of open proxies is that they do not cipher and check the transferred data. Open proxies are vulnerable as well as those who decide to use them.
Threat of Viruses
Open proxies transmit both legitimate and malicious traffic. That is why bad actors often use them to implant malware or illegal content onto your device or infect your device with viruses.
By deploying malware through open proxies hackers can spy on your online activity, use your device as an open proxy or perform actions on your behalf, like sending out spam messages.
It is possible for a computer to run as an open proxy server and pass external traffic. This means a device on your home network may be infected with viruses, trojans, or worms and act like a zombie computer or you may have misconfigured proxy software running on the laptop.
Phishing
An open proxy has no clear privacy policy. It tracks everything that goes in and comes out of the proxy server, including your private information, logged social media and bank accounts passwords, and credit card details. This data is a vulnerable asset that attracts hackers.
How To Use Open Proxy?
An open proxy can be deployed by updating users’ web browser settings. You do not have anything else to set up a proxy.
Lists of open proxy servers can be found in seconds with a simple Google search. You will find proxy servers available for public use, their IP addresses, the port they listen on, what country they are in, and their level of anonymity. Write down a few of them.
Next, you need to configure your browser to route connections through a proxy server. This process is quick and easy.
Here’s how to set up an HTTP proxy in three browsers (on Windows 10) and in Safari (on IOS):
Edge
- Open Edge.
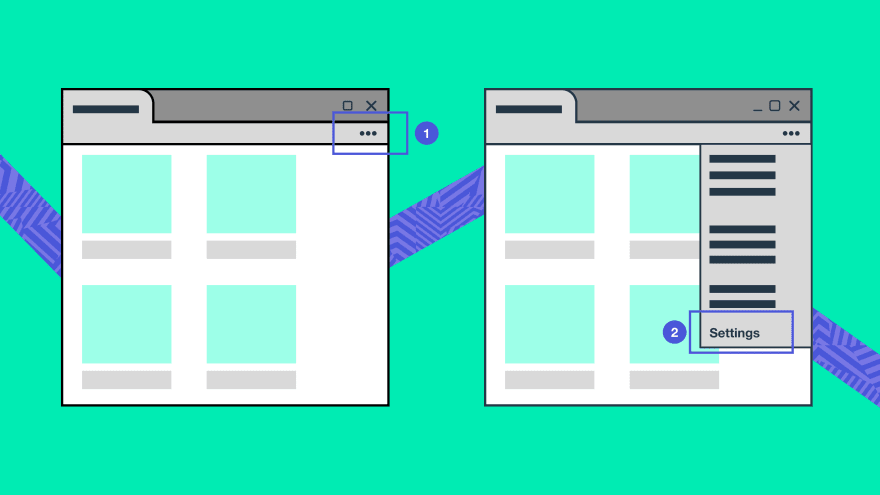
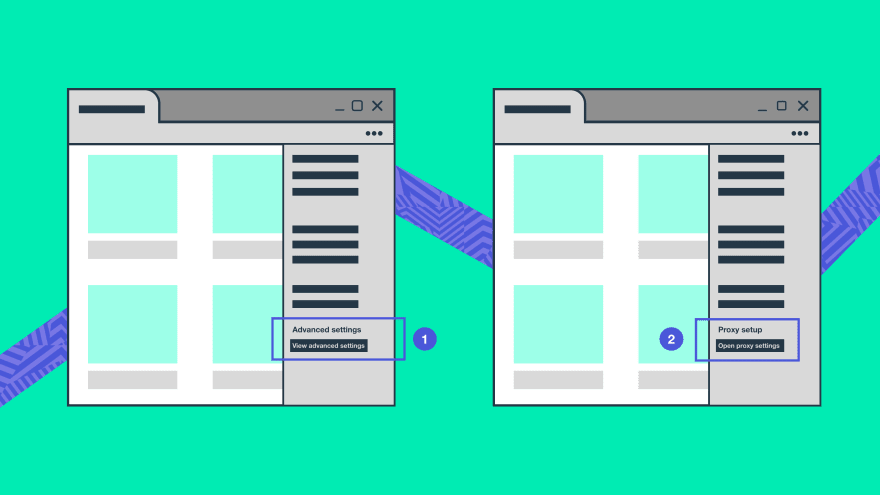
- Click Settings and more > Advanced > Open proxy settings.
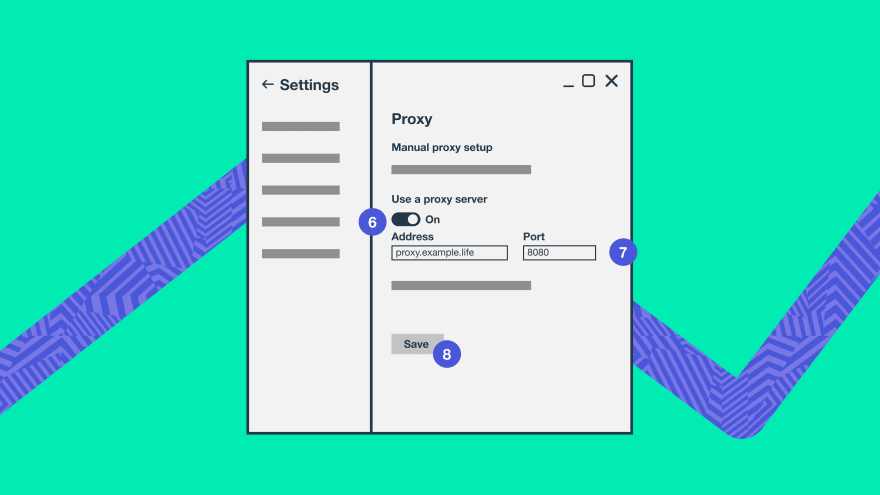
- Under Manual proxy setup, select Use a proxy server.
- Enter the address of your proxy server and a proxy port number.
- Click Save to save your changes.
Firefox
- Open Firefox.
- Click Menu > Options.
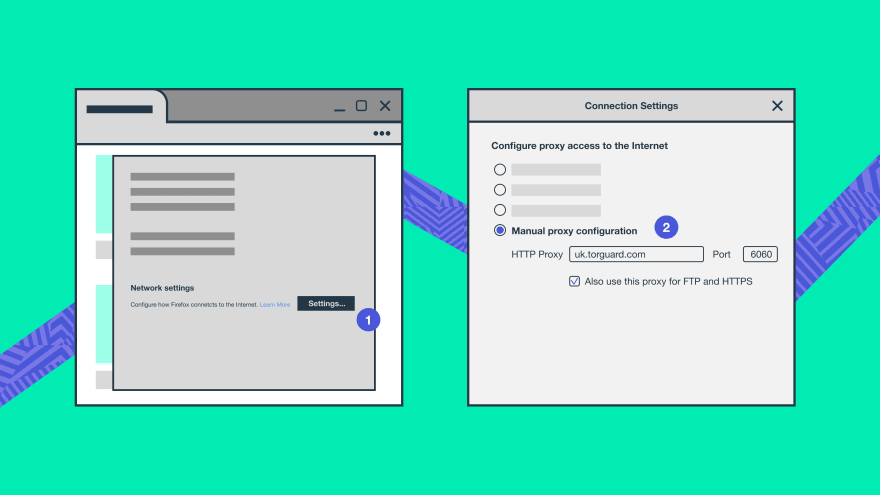
- In General, click Network Settings
- Select Manual proxy configuration.
- Enter the address of your proxy server, and a proxy port number
- Click OK to save your changes.
Chrome
- Open Chrome.
- Open the Customize and control Google Chrome menu
- Click Settings > System > Open proxy settings
- Select Manual proxy setup
- Enter the address of your proxy server and a proxy port number.
- Click Save to save your changes.
Safari
- In the Safari app on your Mac, choose Safari > Preferences, then click Advanced.
- Click Change Settings (next to Proxies) to open the Network pane of System Preferences.
- Enter the address of your proxy server and a proxy port number your network administrator provided.
- Click OK.
An open proxy server is configured in a way that anyone can use it. They provide a sufficient level of anonymity and help access geo-restricted content. There are proxy servers that are intentionally open to the general public, and they lack internet security regulations. There are also private proxy servers that are unintentionally left open because they are misconfigured HTTP proxy servers.
Open proxy servers are widely used by spammers because proxies hide spammers’ IP addresses from recipients which leads to massive open proxy abuse. Moreover, open proxies threaten your online safety by being a honeypot for sensitive information stealing.
Should you use open proxies, be extra careful.
This post was originally published on SOAX blog.







Top comments (0)