A few months ago I wrote a post in the Wazuh blog describing how to monitoring root actions on Linux systems using auditd and Wazuh which had been useful for a lot of users. Nevertheless, I've been asked by a slack community user how to do something similar on Windows and I've found the solution may be a little bit tricky.
I'm writing this post sharing with you the solution I've proposed to this user in order to leave it in writing and have it at hand if someone needs it in the future.
Sysmon
My proposal was simple: use Sysmon, a (and I'm quoting Microsoft documentation) Windows system service and device driver that, once installed on a system, remains resident across system reboots to monitor and log system activity to the Windows event log which It provides detailed information about process creations among other things.
But, how does Sysmon integrates with Wazuh?
Okay, there is an interesting post in Wazuh blog talking about Sysmon and how to install and integrate it with Wazuh, but it described a particular case where the execution of a concrete program is realized.
As we want to track every program execution in the system (As a starting point, of course, we could filter the data in one way or another and we won't generate alerts for every single program execution!), we need a different Sysmon config.
So what do we do?
Install Sysmon as described in Microsoft documentation and configure it according to our needs. I recommend using it as a base this Sysmon configuration which is well documented and available at GitHub. It has some exceptions for the Sysmon event with ID 1 (process creation) which is the one we want to track.
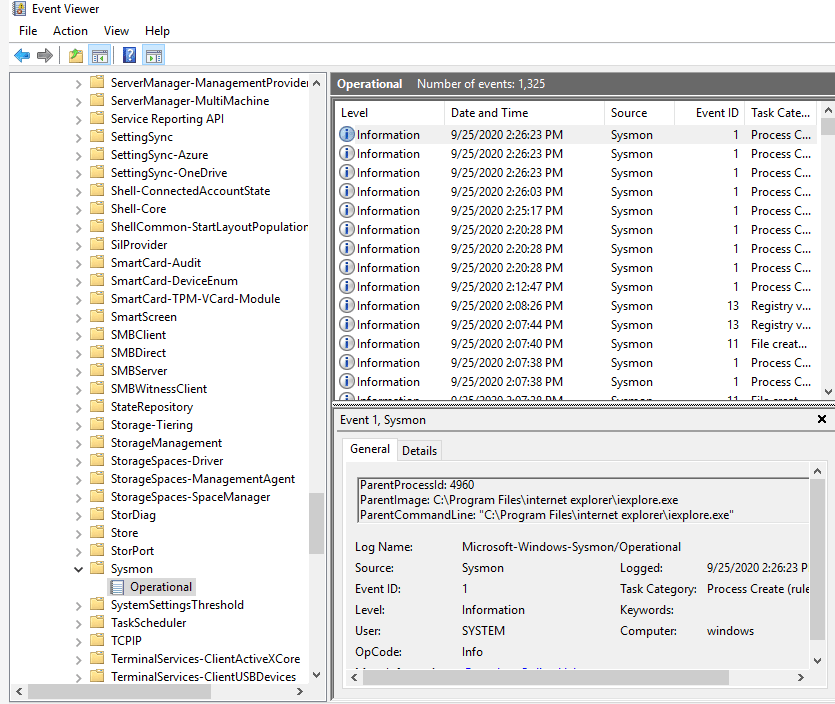
After enabling Sysmon on our system, we will start receiving events on the event viewer for program executions (on the Sysmon folder, like it is shown in the image)
Now, we will need to include this to our Wazuh Windows Agent configuration (ossec.conf) to make it analyze those Sysmon logs:
Microsoft-Windows-Sysmon/Operational eventchannel
And, in order to generate alerts, add to our manager custom rules (/var/ossec/etc/local_rules.xml):
sysmon_event1 Process creation detected: $(win.eventdata.description) by $(win.eventdata.user)
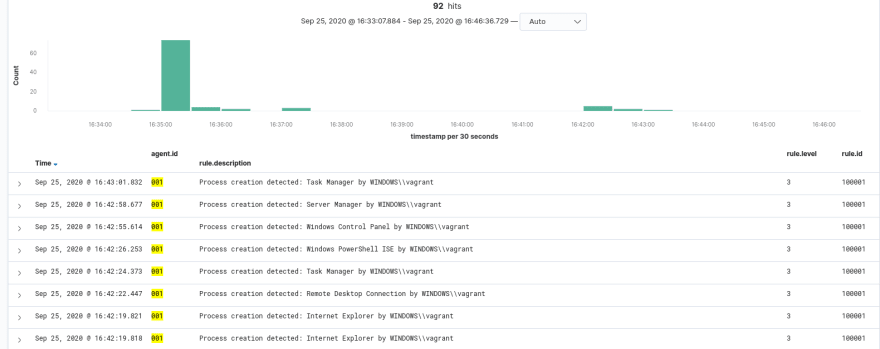
Naturally, this will generate alerts for every single process created on the system (with the exception of those that we filter in the Sysmon configuration). My advice over here would be to receive an alert of level 3 for all command execution (maybe filtering with Sysmon that program that doesn't matter to us) and child alerts with a severer level for more unusual programs.
For example:
sysmon_event1 mimikatz.exe Malicious program process creation detected: $(win.eventdata.description) by $(win.eventdata.user)
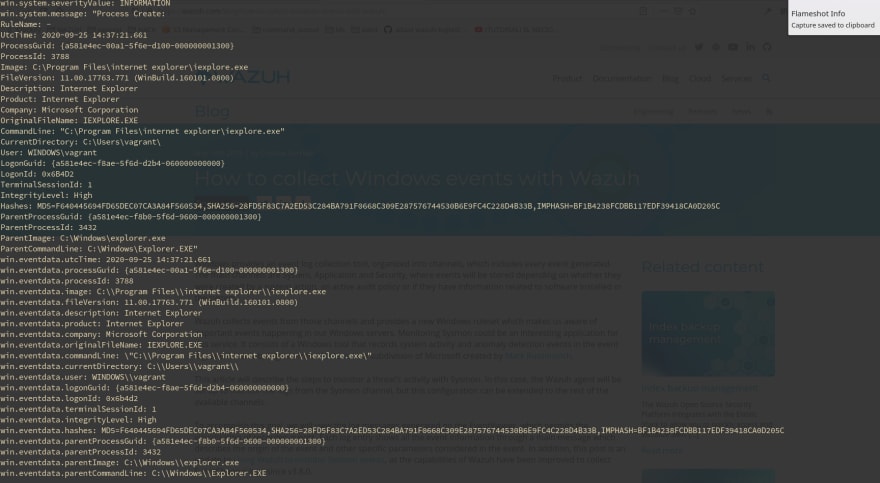
Here, an example of a complete alert generated by Wazuh using Sysmon:
And that's all.
Extra: Legacy systems.
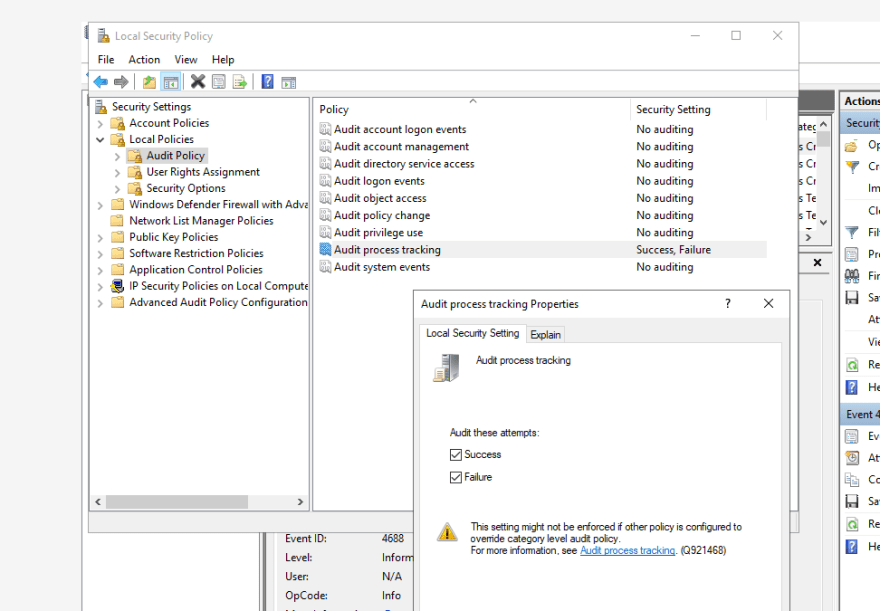
What if my system is old and doesn't support sysmon? Another way could be to enable a security system policy to track program execution:
And enable eventlog data collection on Wazuh Windows Agent configuration:
Security eventlog
And a custom rule on your manager:
18104 Process started on windows server 4688
With these steps you could generate another simpler but awesome alert like this one:
** Alert 1601034144.2471775: - local,syslog,sshd,
2020 Sep 25 11:42:24 (windows) any->WinEvtLog
Rule: 100009 (level 5) -> 'Process started on windows server'
User: (no user)
2020 Sep 25 11:42:21 WinEvtLog: registry: AUDIT_SUCCESS(4688): Microsoft-Windows-Security-Auditing: (no user): no domain: windows: S-1-5-21-3469229866-3176928381-1688825521-1000 vagrant WINDOWS 0x3fce6 0x1240 C:\Program Files (x86)\Internet Explorer\iexplore.exe %%1936 0xd9c ? S-1-0-0 - - 0x0 C:\Program Files\internet explorer\iexplore.exe S-1-16-12288
type: registry
It would be easy as well to create child rules for more concrete security events.
And that is all! I hope you've found this post useful. If you need help with something don't doubt to ask here or open a thread in Wazuh slack channel, someone would be glad to help you!


Top comments (0)