2021 is coming to an end, which means it's time to sum up the year! Today we'll tell you about the new features we added to PVS-Studio in the past year. Buckle up and let's go!
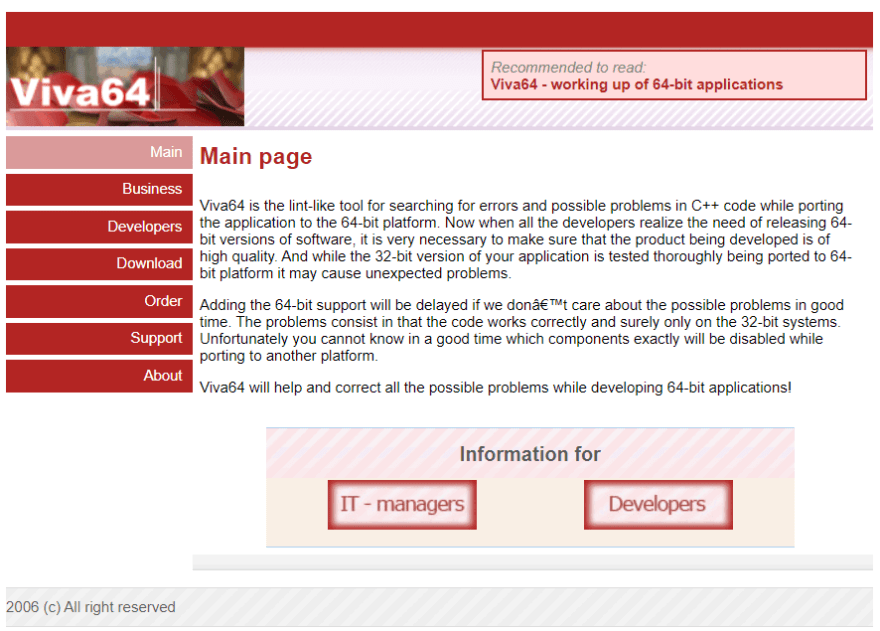
We'll start with going back to the past. You didn't expect that, right? Still, on this day 15 years ago we released the first version of our analyzer — Viva64 1.00. Yes, 15 years ago there was no PVS-Studio, no C# and Java analyzers. Even no general analysis diagnostics back then! :)
You can use the web archive to look at our website of those years:
A lot happened since then. The product has been actively evolving, and the company has been growing. To learn more about the PVS-Studio's history look at this page and read the following article: "PVS-Studio project - 10 years of failures and successes".
But it's time to return to our main topic and look at the new features PVS-Studio got in 2021! Let's start with general enhancements not tied to a specific language. You can find language-specific things in sections about C, C++, and C#.
Website update
Since we're talking about websites. If you visit our website from time to time, you probably noticed that we completely redesigned it. Besides, we finally moved to the pvs-studio.com domain. We increased the website's usability: the articles now have likes/dislikes, the documentation now has the dropdown menu, and much more. You can read about it all here.
Safety and security
We continue to develop PVS-Studio as a SAST (Static Application Security Testing) solution, and in 2021 we dedicated a lot of time and effort to this.
First, we added new groups of diagnostics that comply with OWASP ASVS (C++, C#, Java) and AUTOSAR. You can look at the full list of the PVS-Studio's diagnostic capabilities here.
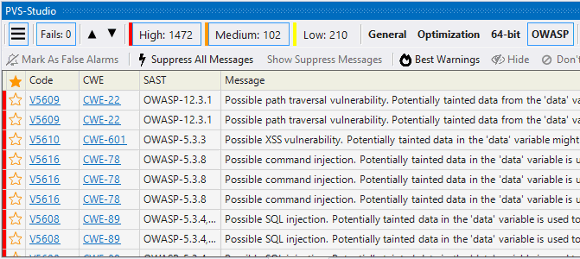
Second, we added information about security identifiers to the analyzer's reports. Earlier you could see the CWE and MISRA identifiers, now we also added OWASP ASVS, SEI CERT, and AUTOSAR. These identifiers are available in PVS-Studio plugins for IDEs, in conversion utilities (for example, PlogConverter), and in SonarQube as tags for issues.
In the plugin for Visual Studio, security identifiers look like this (the example below demonstrates CWE and OWASP ASVS):
Third, we updated the tables of PVS-Studio diagnostics compliance with various standards:
- CWE;
- OWASP Application Security Verification Standard;
- SEI CERT Coding Standard;
- MISRA C, MISRA C++;
- AUTOSAR C++14 Coding Guidelines.
You can use them to quickly look at the PVS-Studio's diagnostic compliance with the desired standard's rules.
Besides, we added compliance with OWASP Top 10 and CWE Top 25:
We'll describe the work done on safety/security for each of the languages in the corresponding sections.
Visual Studio 2022 support
In the beginning of 2021, Microsoft announced Visual Studio 2022. They promised a lot of features, but the main one — the IDE would be 64-bit.
There was no question about whether to support Visual Studio 2022 — of course we were going to support it. Additionally, the closer the release of VS2022 was, the more people asked if we had a plugin for this IDE.
Finally, we supported Visual Studio 2022 in the PVS-Studio's December release. This release was the closest to this IDE's release.
Display of the Analyzer Best Warnings
When users run a static analyzer for the first time, they may encounter a large number of warnings. This is especially true of projects with much legacy code.
And here the person who is just getting acquainted with the analyzer may fall into several traps. For example, they can:
- turn on all warning groups of all levels and get discouraged from the possible number of warnings;
- look through a dozen of warnings, run into mostly false positives and get discouraged.
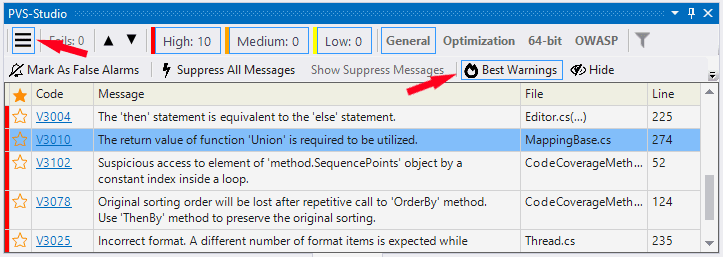
And we would like users to see the yummiest part — warnings that make them say "hm, there's definitely something wrong with the code here". Well, now PVS-Studio has such a mechanism. You click a special button and see the best warnings from the analyzer's log — the warnings that most likely point to an error.
As of now, this feature is available only in the Visual Studio plugin. However, in the future, we intend to integrate the best warnings mechanism into plugins for other IDEs.
Notifications about warnings issued for new code
PVS-Studio has the blame-notifier utility, which notifies developers and managers about warnings issued by the analyzer. The use of blame-notifier in CI, combined with regular analysis, allows developers to quickly see warnings that they may have missed, and managers to monitor the overall situation.
This year, blame-notifier has got an important update. Now the tool makes it possible to process only new warnings issued for new code. In addition, the report itself now contains more information – the date of the code change for which the warning was issued, and the revision number.
You specify the number of days that precede the current utility run. If the code is older than the specified days, the warnings issued for the code will be excluded from the list.
Why is this update so important? It allows to focus specifically on the new analyzer warnings and have a lighter analogue of SonarQube's "Clean as You Code". If you can't or don't want to configure SonarQube, but you want to have a similar feature — now you have it. You can read more about the mode, its history and work mechanics here.
Java
Unfortunately, the Java analyzer doesn't have any major updates except SAST identifiers and diagnostics from OWASP ASVS. :(
We have paused the development for now. We're searching for ideas in this direction. If you have any suggestions about the analyzer's functionality — share with us!
Nevertheless, we continue supporting the Java analyzer and fixing possible bugs.
C, C++
Intermodular analysis
Now the C++ analyzer supports intermodular analysis. In this mode, when parsing code, the analyzer takes into account information about functions defined in other translation units.
With intermodular analysis the analyzer learns the information about the full project structure. This makes the analysis more accurate and qualitative. This is very similar to the Link Time Optimization (LTO). Thus, the analyzer can learn the behavior of an external function from another project file and issue a warning, for example, for dereferencing a null pointer passed as an argument to an external function.
Despite the fact that this mode allows finding more interesting errors, in the C++ analyzer it's deactivated by default. Intermodular analysis may slow down the analysis. Read more about the mode's features and peculiarities.
Plugin for CLion
PVS-Studio has plugins for various JetBrains IDEs: Rider, IntelliJ IDEA. Somehow we missed another popular IDE — CLion. Our clients expressed an increasing interest in this feature. Moreover, the PVS-Studio plugin for CLion as a cross-platform IDE would make it possible to work comfortably with the C++ analyzer regardless of the environment in which the developer works: on Windows, Linux or macOS.
In the end, we made a plugin for CLion, although there were some challenges during development.
Enhanced Unreal Engine support
One of the technologies used in static analysis is annotating functions of popular libraries. The developer studied the documentation of such functions and notes useful facts in form of annotations. The analyzer uses these annotations to make the project analysis more accurate.
In the PVS-Studio analyzer for C++, we additionally annotated hundreds of Unreal Engine functions. Annotations help not only to identify new errors, but also to eliminate some false positives. We used an open-source project, CARLA, as a proving ground. You can read about it in our article.
We provided another important enhancement for the analyzer to work with Unreal Engine projects. We added the ability to disable warnings on existing code — baselining. With this feature, developers can work only with new warnings without being distracted by warnings issued for legacy code. You can read more here.
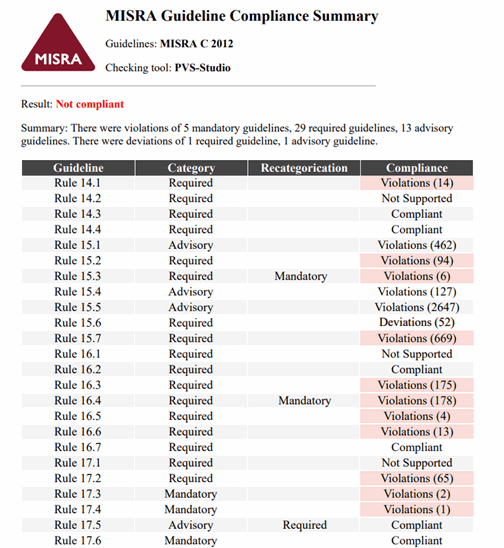
MISRA
We collected feedback from our clients and saw interest in checking projects for compliance with the MISRA C 2012 standard. After that we started developing this direction to a competitive level. Our goal was to increase the standard coverage to 80% with our diagnostics. As a result, we made 57 new MISRA diagnostics. As we planned, now PVS-Studio covers 80% of MISRA C 2012.
Another goal was to make the analyzer generate the MISRA Compliance report. This report helps understand whether your project complies with the MISRA C / MISRA C++ standards, taking into account all deviations and re-categorizations. Well, now the analyzer is able to create such a report. Read more about this feature here.
C#
Taint analysis, OWASP
In 2021, we implemented taint analysis in the C# analyzer. In short, this is the analysis technology that tracks tainted data transmission over an application. Data is considered potentially tainted when it comes from an external source and could have been compromised by an attacker. If tainted data gets into some places of an application (like a raw SQL-query), this data causes potential vulnerabilities. Find more information about taint analysis in this article.
We used taint analysis to develop several diagnostics that search for a number of weaknesses: SQLI, XSS, path traversal, XXE, XEE, etc.
Speaking of security and XEE. Wondering why and how Visual Studio 2022 could eat up a lot of memory (like 100 GB) on a machine? Read more here.
Performance
We spent a lot of time optimizing the C# analyzer and wrote a number of articles about that. The graph below shows how the analysis time for large projects decreased between PVS-Studio 7.11 and PVS-Studio 7.14 releases.
For more details on what, how, and why we optimized, see the following articles:
- "All hail bug reports: how we reduced the analysis time of the user's project from 80 to 4 hours"
- "Optimization of .NET applications: a big result of small edits"
Support projects on .NET 5 and .NET 6
A little late, but this year we taught the analyzer to work with projects on .NET 5. After that we taught it to work with .NET 6. This time we weren't late. The analyzer can also parse the C# 10 code now.
Besides, PVS-Studio C# on Linux and macOS now works on .NET 6.
Conclusion
Of course we didn't mention all the features that appeared in our analyzer in 2021. We continued to develop general analysis diagnostics and fix false positives, we introduced some other enhancements. For example, we supported new compilers, enhanced the ability to fine-tune the analysis with .pvsconfig files, etc. You can read more about features shipped with every PVS-Studio release here.
You can also subscribe to our YouTube channel so as not to miss our new videos.
One last thing: what would you like to see in PVS-Studio in 2022? Please leave a comment below.
And of course, happy holidays!







Top comments (0)