1. What Are Linux Permissions?
Linux file permissions determine who can perform actions on files and directories, such as reading, writing, and executing. Each file or directory in Linux has associated permission sets for the file owner, a group, and others. These permissions are fundamental in protecting sensitive information and preventing unauthorized access.
Permissions in Linux are represented by a combination of letters and numbers. The three types of permissions are:
1.1 Read (r)
- Allows a user to open and read the contents of a file.
- On directories, it allows listing the directory's contents.
1.2 Write (w)
- Allows a user to modify or delete a file.
- On directories, it allows the user to create or delete files within the directory.
1.3 Execute (x)
- Allows a user to execute a file, such as a script or binary program.
- On directories, it allows entering the directory or accessing its files.
Each file in Linux has three sets of these permissions:
- Owner : Permissions for the user who owns the file.
- Group : Permissions for the group that owns the file.
- Others : Permissions for all other users.
2. Understanding Permission Notation
Permissions are displayed in a symbolic or numeric format when you list files using the ls -l command. Here’s an example:
$ ls -l
-rwxr-xr--
This output can be broken down into:
- -rwxr-xr-- is the permission string.
- The first character (-) indicates the file type (- for files, d for directories).
- The next three characters (rwx) show the owner’s permissions: read, write, and execute.
- The middle set of characters (r-x) represents the group’s permissions.
- The last set (r--) shows the permissions for others.
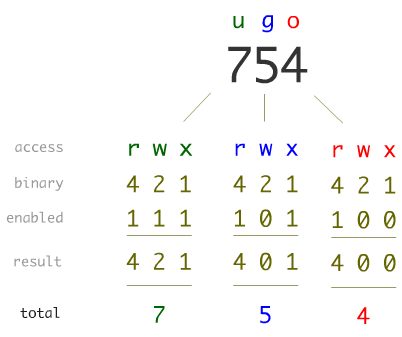
2.1 Numeric Representation
Permissions can also be represented numerically using octal notation. Each permission type has a corresponding value:
- Read: 4
- Write: 2
- Execute: 1
The sum of these numbers gives the final permission:
- rwx = 4 + 2 + 1 = 7
- r-x = 4 + 0 + 1 = 5
- r-- = 4 + 0 + 0 = 4
Example:
Using the same example from above (rwxr-xr--), the numeric permission is 754.
3. How to Change Permissions with chmod
You can change file permissions using the chmod command. chmod modifies file permissions either symbolically or numerically.
3.1 Symbolic Mode
To modify permissions symbolically, use chmod with the permission set (u for owner, g for group, o for others) and the action (+, -, or =).
Example:
$ chmod u+x myscript.sh
This command adds execute permission for the owner of the file myscript.sh.
3.2 Numeric Mode
Numeric mode changes permissions based on the octal values discussed earlier. For example, to set a file's permissions to rwxr-xr--, you would use:
$ chmod 754 myscript.sh
3.3 Demo Code: Changing Directory Permissions
Consider a directory project/ where you want the owner to have full permissions, but the group and others should only be able to read and execute.
$ chmod 755 project/
After running this command, if you check the permissions using ls -ld project/, you’ll see:
drwxr-xr-x 2 user user 4096 Sep 26 14:10 project/
This output shows that the owner has full access (rwx), while the group and others have read and execute permissions (r-x).
4. Practical Use Cases for Permissions
Understanding and using permissions effectively is essential in different scenarios, especially in shared environments and when setting up servers.
4.1 Securing Sensitive Files
Let’s say you have a configuration file, config.txt, that should only be accessible by the file owner (you). You can restrict access as follows:
$ chmod 600 config.txt
The permissions 600 mean that the owner can read and write (rw-), but the group and others have no permissions (---).
4.2 Managing Group Collaboration
If you're working in a shared project directory, and you want all group members to be able to modify the files but not other users, you can use:
$ chmod 770 shared_dir/
The 770 permission allows the owner and group to read, write, and execute, but prevents others from accessing the directory.
5. Changing Ownership with chown
In addition to permissions, ownership of files and directories can be changed using the chown command. The chown command modifies the file owner and group.
$ sudo chown newuser:newgroup file.txt
This changes the owner of file.txt to newuser and the group to newgroup.
5.1 Demo Code: Changing Directory Ownership
To change the ownership of a directory project/, run the following command:
$ sudo chown -R user:group project/
The -R option applies the ownership change recursively to all files and directories inside project/.
6. Advanced Permission Techniques: Setuid, Setgid, and Sticky Bit
Linux also has advanced permission settings that provide more control over file and directory access.
6.1 Setuid (Set User ID)
Setuid allows a file to be executed with the permissions of its owner, rather than the user running the file. This is useful for programs that need elevated privileges.
$ chmod u+s script.sh
6.2 Setgid (Set Group ID)
Setgid ensures that files created in a directory inherit the group ownership of the directory, rather than the user creating them.
$ chmod g+s directory/
6.3 Sticky Bit
The sticky bit is commonly used on shared directories like /tmp to ensure that users can only delete their own files, even if others have write access.
$ chmod +t /shared_dir/
7. Conclusion
Linux permissions are a vital tool for system administration, enabling you to control access to files and directories securely. Understanding the symbolic and numeric representations, along with how to use chmod and chown, will allow you to confidently manage permissions. Advanced techniques like setuid, setgid, and sticky bit further enhance control. Mastering these concepts ensures that your Linux environment remains safe and efficient.
Have questions or run into any issues? Feel free to leave a comment below!
Read posts more at : Understanding Linux Permissions: A Complete Guide with Examples


Top comments (0)