Photo by Emily Reimer on Unsplash
The Issue
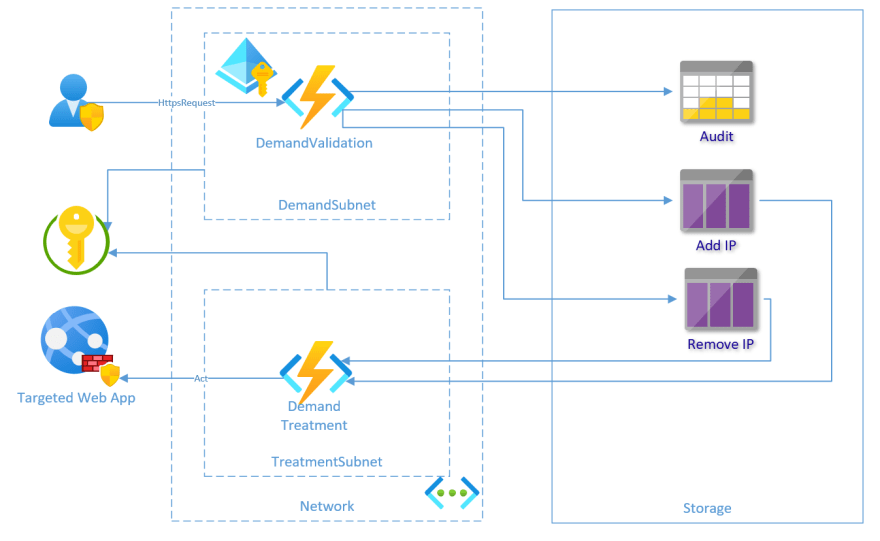
I was asked to frequently add or remove IP to an Azure Web Application firewall configuration, in a case where a restriction to a subnet is not an option. That's why i wanted to automate this task, in order to add a lifetime to the add.
The plan
After some thoughts, i come with the following plan:
DemandValidation Azure Function
Purpose
Validating request, and managing workflow of adding and removing IP.
Description
It's a C# Azure Function exposing one Http input binding, requesting Azure Active Directory authentication. The workflow of add and removing IP is managed through a Durable Function.
The claims in the request must contains at least the ID of the allowed group, in order to trigger the logic. The configuration required to inject security groups into claims will be treated in a future post.
The message sent to the queue and record to the audit table contains:
- IP of the request
- date in the description
- a unique ID
Audit Azure Table
Purpose
Keep track of the demand, without exposing clearly any sensitive data linked to a person.
Description
It's an audit log, with the capability of knowing if an IP has changed for a demand.
Add / Remove Azure Storage Queue
Purpose
It's a pipe to transfer request to the function having rights to manage firewall without exposing it.
Description
It's 2 Azure queue serving as link between 2 Azure Function.
DemandTreatment Azure Function
Purpose
Treating requests in Add and Remove queue by invoking simple Powershell Core commands.
Description
It's a Powershell Azure Function validating request (only one IP added), and applying it to the firewall. The priority used is a constant.
The Function identity is an Azure Managed Service Identity, which has a role to manage firewall configuration on the targeted Web Application.
Hope this helps !



Top comments (0)