As I dive deeper into my studies related to blockchain and blockchain development, I find some intriguing core concepts that shine a light towards the inner intricacies of how the blockchains work.
One of these concepts that are vital to the blockchain functionality is called SHA256. It is a Secure Hashing Algorithm, commonly used for digital signatures and authentication. But before we try to get a better grasp of it, let's understand what a Hash Algorithm is.
Let's say you want to transfer some data from one point to another, and you need this data to be secure and easily verifiable. By using the Hash Algorithms, you are going to crush down that big chunk of data into a single line - a hexadecimal value that summarizes what is contained in that file.
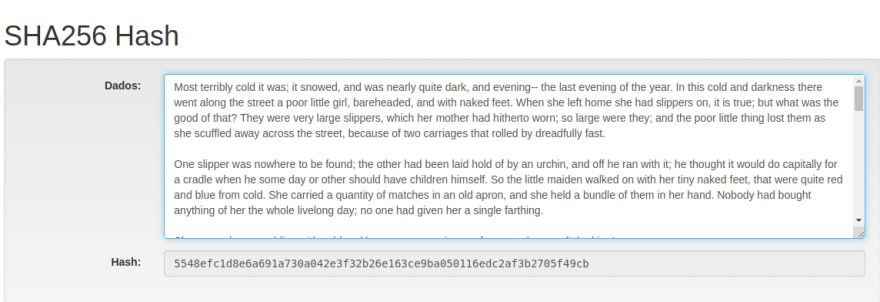
To illustrate that, let's use this awesome website called AndersBrownworth.com. They have a tab focused on Hashing, and we can go there and play with any values inside the Data box, and we can observe how the hash value is going to change. For this example, I'm going to use a short story from Hans Christian Andersen that I really like: The Little Match Girl.
The original short story has 5456 characters, but when it's hashed down, it will be represented by a 64 characters string.
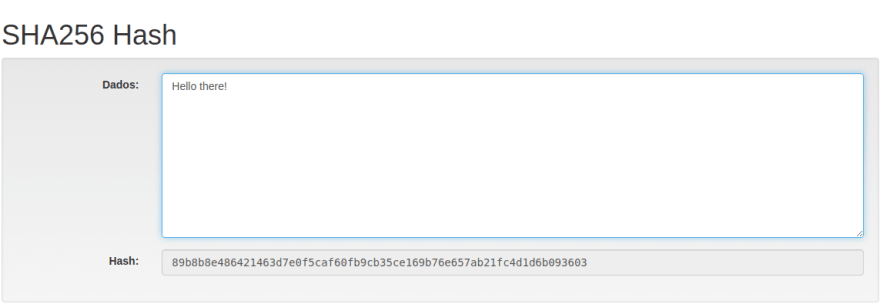
It is important to note that, no matter how many characters you pass through a hashing algorithm, you will always get a string with the same amount of characters as a result. Even if we write a simple "Hello there" in the data box, it will return a 64 characters string to us.
This hexadecimal value appears to be random, but it isn't. As it was said before, it is dependent on the original value, so even if we make small changes in the text, it will return a different value. For example, the hash value for our saddening short-story is 5548efc1d8e6a691a730a042e3f32b26e163ce9ba050116edc2af3b2705f49cb. That combination of 5456 characters in that same order will always return this value. But if we add an "A" to the beginning of the text, we will get a different result: 9ad55f658a3636ca079a0fe74b5a06a914977ba15b4db7f012ae2e47c8d1417b.
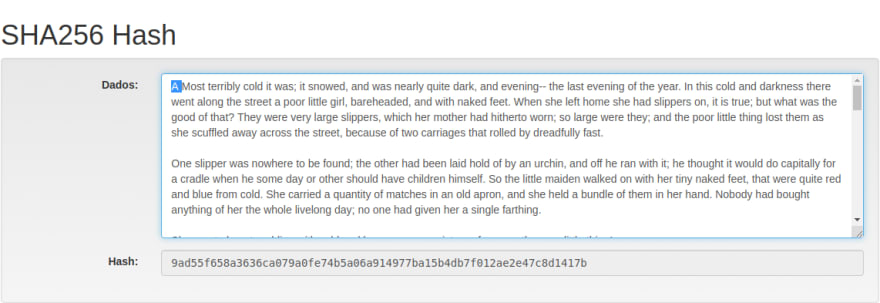
Even if we remove the extra "A" we added, going back to the original text, and then we change a semicolon for a regular comma, we still get different results: 2de2316e5e5f9e10ee899a7f42dc51a19f7fd9a219dae672ada1a80f5c74134a. So this might show how powerful SHA256 is, especially when for digital signatures.
This Avalanche Effect, this event of changing a letter, a signal or even a single byte in the original file and with that you modify completely the hash output, is one of the three requirements of a hashing function. The other two being Speed, which is also fairly great in SHA256, because it can find a good balance between fast enough - so it will improve its adoption - and slow enought - so it's not easy to crack - and Collision Resistant, which means it will prevent that two different inputs will provide the same output. Due to its calculations it's almost impossible to naturally create the same output with two different inputs, but if one can manipulate the function to artificially create a collision, it could result in a security break.
Summarizing, the process goes like this:
And how is it used in the various blockchains out there? With the hashing function, it is possible to create a different hash to each block in the blockchain. The reason for this is to provide an unique identifier for every block, allowing us to reference a block by its "digital fingerprint", the hash. It also allows the connection between to blocks, creating a chain, which I am going to explain in a future text.
Now, to implement a basic usage of the SHA256 with JavaScript, let's install a npm package called CryptoJS. Its installation is quite simple, you just need to run
npm install crypto-js
Once it's done, create a JavaScript file in the same folder you installed CryptoJS and open it.
Now we are going to import the CryptoJS package using:
const CryptoJS = require("crypto-js");
Then, we just need to call this function we just imported, using:
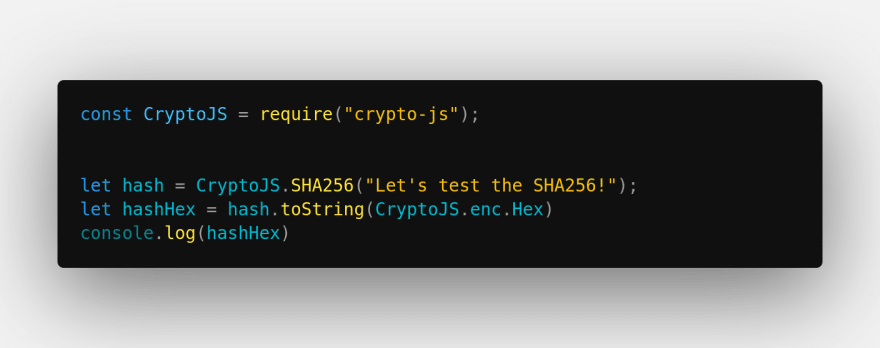
let hash = CryptoJS.SHA256("Message")
This step will create a Word Array based on the message input. So let's change the input and add a functionality that will encode the Word Array into a hexadecimal string:
let hashHex = hash.toString(CryptoJS.enc.Hex)
And then, to log it to our terminal, we'll use a regular console.log
console.log(hashHex)
In the end, the code will look more or less like this:
Now, time to test it. By running a node sha256.js, we can get the result in the terminal
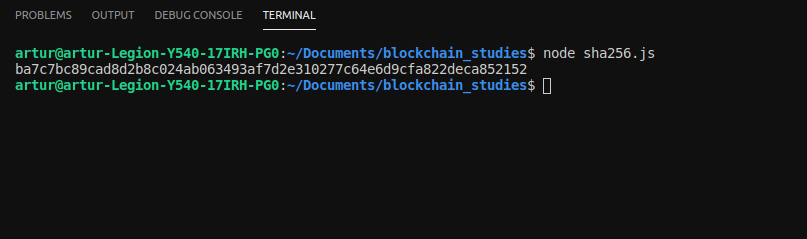
We got a hexadecimal value ba7c7bc89cad8d2b8c024ab063493af7d2e310277c64e6d9cfa822deca852152ba7c7bc89cad8d2b8c024ab063493af7d2e310277c64e6d9cfa822deca852152.
If we go back to our hashing companion AndersBrownworth.com and write the same input, we get the same result! Nice, it worked! (:

With this we conclude our first approach to SHA256, understanding how it works, why it's used in blockchain technologies and how to easily implement it with JavaScript.
If you want to keep studying this subject, I'll leave down below some links that might be useful to kickstart your research! Keep coding!



Top comments (0)