In my previous post, I showed how to use Tailpipe to query your AWS CloudTrail logs locally with SQL. Now let's take it to the next level: visualizing those logs with powerful dashboards for advanced threat detection and investigation.
Threat Detection Benchmarks
When investigating suspicious AWS activity, having both powerful queries and interactive visualizations can make all the difference. Whether you're responding to a security incident or proactively hunting for threats, you need to quickly separate normal activity from potential risks.
Enter Powerpipe AWS CloudTrail Detections mod: pre-built dashboards and detections that work with your locally collected CloudTrail logs from the Tailpipe AWS plugin to provide security insights based on industry frameworks like MITRE ATT&CK. And the best part? It all runs locally without sending your sensitive log data anywhere.
Getting Started
If you haven't set up Tailpipe to collect your CloudTrail logs, you can learn how to do that from our prior post.
After you have Tailpipe set-up, add Powerpipe to visualize this data:
# Install Powerpipe
brew install turbot/tap/powerpipe
# Or using the install script
sudo /bin/sh -c "$(curl -fsSL https://powerpipe.io/install/powerpipe.sh)"
# Create a directory for the dashboards and install the mod
mkdir dashboards
cd dashboards
powerpipe mod install github.com/turbot/tailpipe-mod-aws-cloudtrail-log-detections
And now start the dashboard server:
powerpipe server
Visit http://localhost:9033 in your browser, and you're ready to explore your CloudTrail logs dashboards.
Viewing CloudTrail Activity Through a Security Lens
The mod provides multiple benchmarks with 100 pre-built detections to help visualize suspicious activity. Let's walk through the key views and capabilities this gives you:
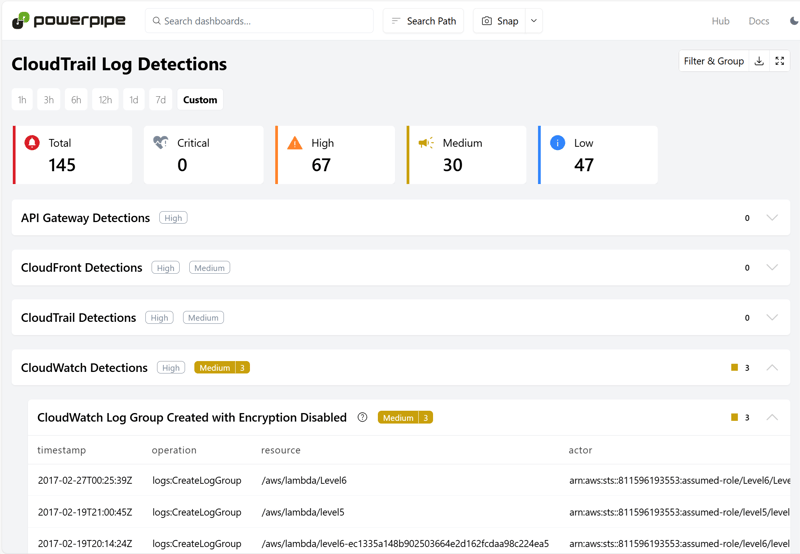
Detections by AWS Service
The CloudTrail Log Detections Benchmark organizes findings by AWS service, making it easy to focus on specific areas like IAM, S3, or EC2.
Each detection is pre-built to identify potentially suspicious activity, such as:
- IAM root user console logins
- S3 bucket policy changes
- EC2 security group modifications
- CloudWatch log deletion events
Click on any detection to see the specific CloudTrail events that triggered it, complete with timestamps, usernames, and other contextual details.
Hunt for Bad Actors
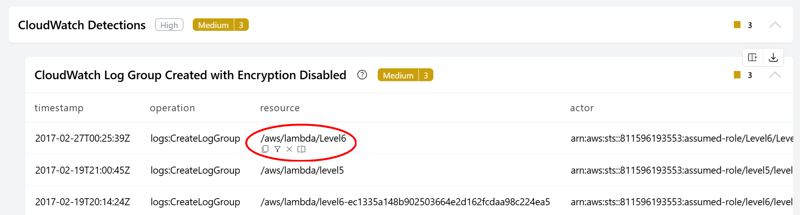
Security analysis is all about finding needles in haystacks. Powerpipe has built-in filtering capabilities to help you narrow down and focus on the log entries found by detections; hover over any cell to reveal a row of four icons:
- Copy value: Quickly grab data for use in other tools
- Filter by this value: Focus only on rows with this specific value
- Exclude value from results: Remove these rows from your current view
- View row: Examine all details about a specific event
If you want to keep only rows with the /aws/lambda/Level6 resource, select the Filter icon. Conversely if you want to toss that set of rows to focus on everything else, select the Exclude icon. Using these tools you can refine the set of detected rows to ignore those that are benign and focus on the ones that might be malicious.
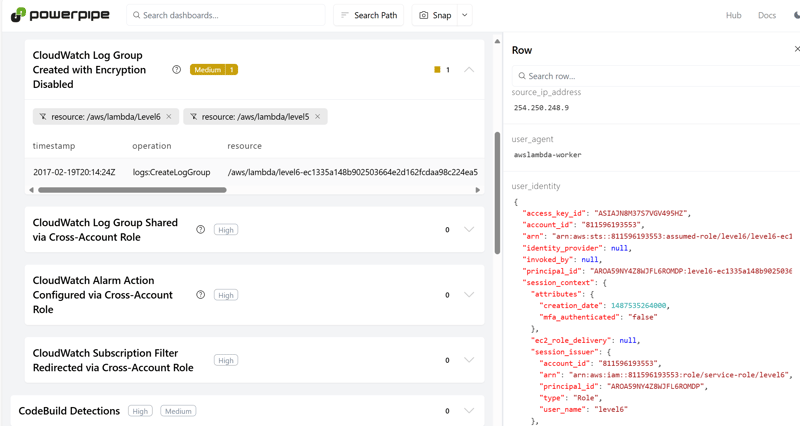
When you find an interesting row, use the View icon to explore it in detail:
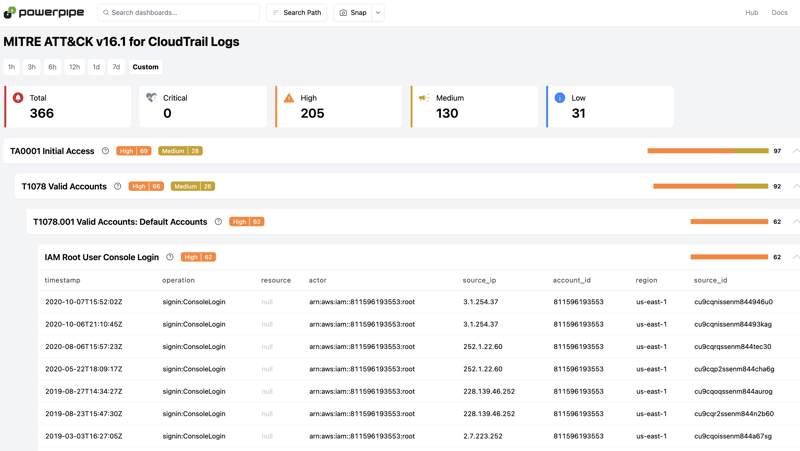
View Through the MITRE ATT&CK Lens
To view results through a different lens, Powerpipe offers a MITRE ATT&CK benchmark that maps the same CloudTrail events to the MITRE ATT&CK framework. This helps security teams understand the potential security implications of each activity and how it might fit into a larger attack chain.
For example, an IAM root user login might appear under:
- TA0001: Initial Access - is a high-level tactic, representing an adversary's goal to gain an initial foothold in a system.
- T1078: Valid Accounts - is a technique related to use of valid credentials (stolen, guessed, or default) to access systems.
- T1078.001: Valid Accounts: Default Accounts - narrows that down to focus on root accounts or accounts with default passwords. That's the context for the IAM Root User Console Login detection.
It's not the only context though, as the same detection also appears under tactic TA0004: Privilege Escalation providing different perspectives to evaluate how an action fits into the overall attack chain.
And the same filtering features are available to investigate further. For example, if the actor performing the login is known and trusted, exclude all console logins from that actor with a single click in order to focus on others that may warrant scrutiny.
Conclusion
With Tailpipe handling log collection and queries, and Powerpipe providing interactive visualization, you have a powerful, local, open-source solution for security analysis. You can analyze logs offline, quickly filter massive datasets, and investigate potential security incidents all while maintaining complete control over your sensitive data.


Top comments (0)