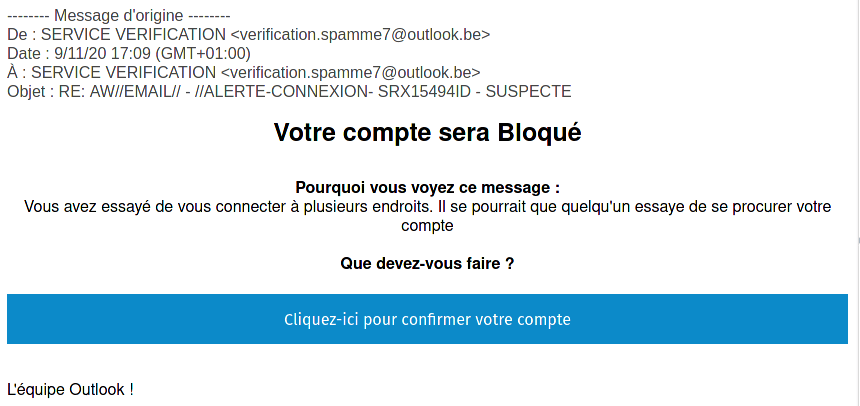
The other day, I got an email from my mom asking me if the email she transferred me was a spam or not. Without any doubt it was but I wanted to a have some fun and train some of my new investigation skills.
The email is telling the user some malicious activity has been seen on the account and asks the user to click on the link to confirm the account. The sender email is verification.spamme7 (at) outlook.be which is probably fake.
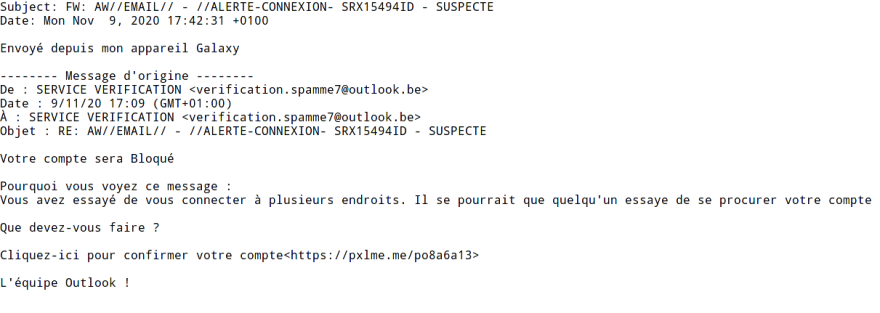
When looking at the text version of the email, we can see the link is not linked to Outlook:
So we have our first link that we can investigate: hxxps://pxlme.me/po8a6a13.
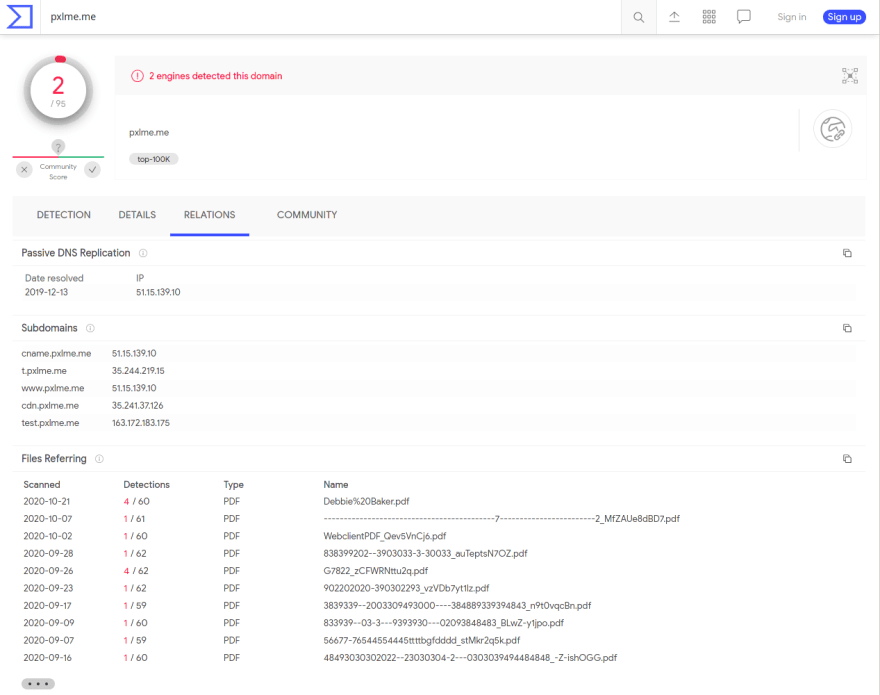
Running the domain in VirusTotal gives us a sign that this might be malicious:
After we run more intel scan with harpoon a CLI based open-source threat intel tool.
Here we can find out that there is an interesting IP address that comes out of the scans: 51(.)15(.)139(.)10. Also the harpoon scan shows use that other urls as such has been submitted to urlhaus, a service by abuse.ch that specialised in malicious urls.
Something that is interesting here is that when we scan the website pxlme(.)me with urlscan to see what's there, we end up on getpixelme(.)com which looks like a normal website. It's interesting to see that there is a redirection from
pxlme(.)me to getpixelme(.)com. So we need to focus on the entire url.
As the domain itself is not malicious, it might be some kind of redirection as the HTTP query doesn't seem to always send to getpixelme(.)com or it can be just a front to distract people who would check the domain.
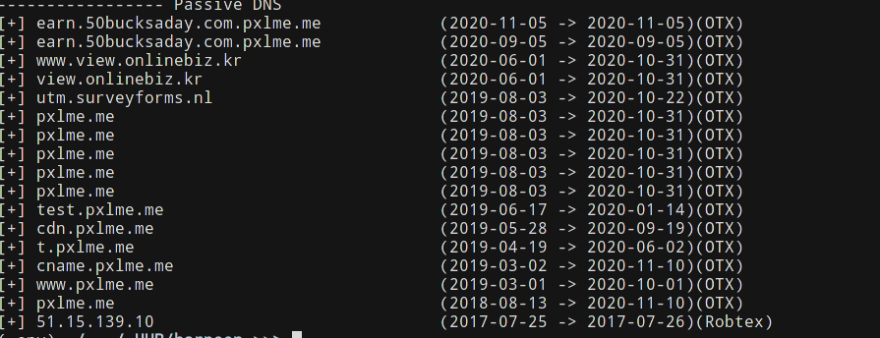
If we look a bit into the passive DNS data from harpoon we can see the resolution for the IP address 51(.)15(.)139(.)10 seem to have changed over time. So one theory would be someone lost access to that domain and then it was used to create spam.
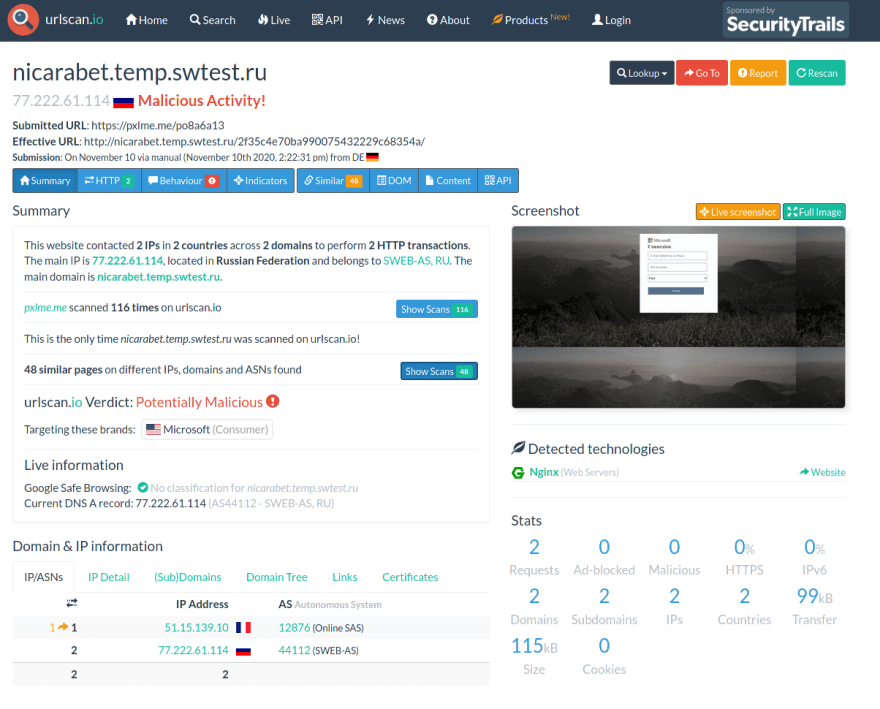
When we scan the phishing url itself, we have much more interesting results:
So clearly phishing and we have even new indicators:
nicarabet(.)temp(.)swtest(.)ruhttp://nicarabet(.)temp(.)swtest(.)ru/2f35c4e70ba990075432229c68354a/77(.)222(.)61(.)114
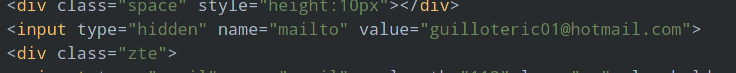
The page itself looks like a fake page for Outlook connection page. On urlscan, we can event look into the source code of the page and we find a very interesting portion:
We truncated most of the code here, just to focus on the most important part. The page is a basic HTML form. It has a 3rd party domain and an hidden field with an email address. HTML forms when submitted will send the content to the form to the designated server. Usually it's the same website but we can see here that it's another website and that there is also another hidden field with a mailto tag. The latter part is a bit weird as usually mailto's tag do not work like that. It looks more like a fake prepopulated field or there is a possibility that the spammer uses this email to get a notification when someone get phished and receives the HTTP POST data directly by mail.
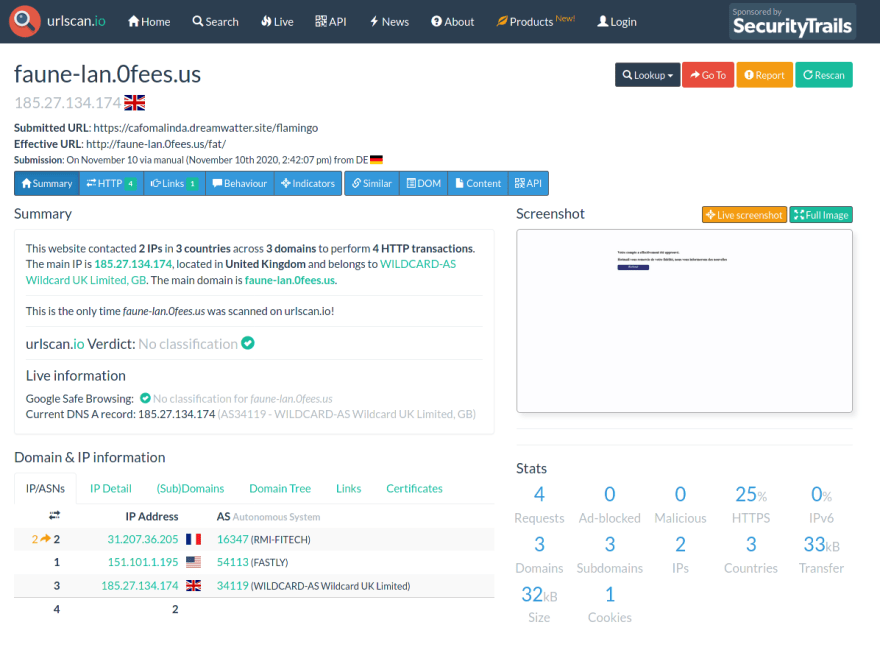
After scanning the redirecting spam, we can see that it's redirected to yet another url: faune-lan(.)0fees(.)us. More interestingly, the button on this page will actually lead you to the official outlook page (live(.)outlook(.)com) where you will probably have to login again. But it's too late, your email credentials have been phished by the spammer.
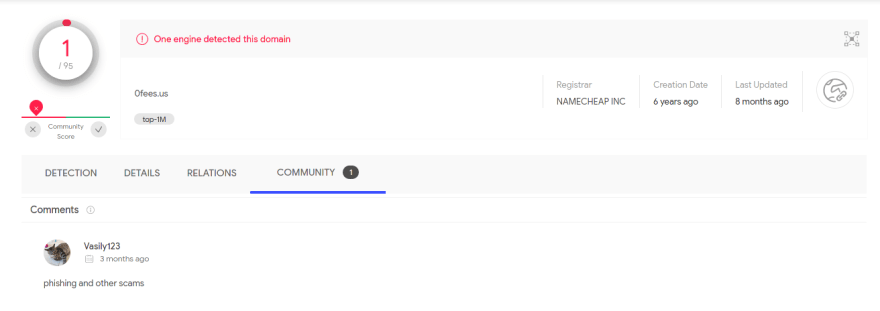
Scanning the final domain on VirusTotal, it seems that it has been flagged as spam:
So the general steps here are:
- phishing email redirecting to a fake page
- HTML form that will log the credentials to the spammer
- redirection to the safe website
- hops through various domains and IPs
Note: I used webtools so I don't create direct queries to potential malicious domains with curl or other tools. It's a good rule of thumb to always create some layers of protection during an investigation.





Top comments (0)