This article was originally published on Codica blog.
Computers and networks have transformed many aspects of our everyday routines. The evolution resulted in new learning and communications techniques as well as security requirements for virtual systems.
This article explores the crucial concepts necessary for robust security. Also, we share Codica’s experience in using them to ensure safety in custom web solutions.
What is security, and why is it important?
Security is the protection of your systems against outer threats. It relies on different layers and procedures. When your solution is protected, it helps avoid the relevant business risks and instability of your solution’s work.
It is worth noting that security is not a limited set of tools. It is rather a set of both tools and guidelines that help protect your solution. As threats constantly change, so do the security guidelines.
The most common model that represents typical threats is STRIDE, developed by Microsoft. The acronym denotes different security leaks, such as unauthorized modification or distribution of data.
The most important security tools include the following:
- Firewalls,
- Intrusion Detection System (IDS),
- Antivirus,
- Encryption tools,
- Packet sniffers,
- Penetration Testing.
The instruments constantly evolve. For example, firewalls changed, as presented in the image below.
Security concepts are standardized under CIA and AAA models, which help us in our practice.
CIA stands for confidentiality, integrity, and availability. It states the importance of protecting data against unauthorized access and changes.
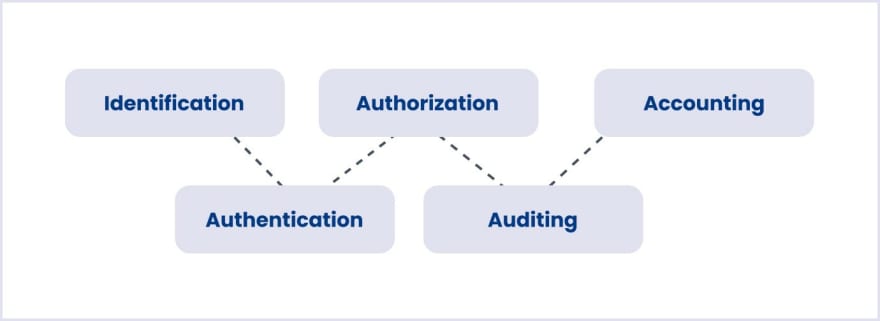
The AAA term means authentication, authorization, and accounting. It means verifying the user’s identity through a step-by-step verification process. You can see the whole process in the picture below.
The security concepts and models help streamline an efficient approach to protecting solutions. We discuss Codica’s practices below as an example of the successful implementation of the security principles.
Security pillars in product development: Codica’s experience
At Codica, we use AWS cloud services for managing infrastructure security. We manage our infrastructure with code. The Infrastructure as Code (IaC) approach allows for scaling and cost saving. Also, it enables you to move the vast security processes to the primary cloud provider.
That is why we use Terraform for our web projects. It allows creating and updating of the AWS infrastructure. Through Terraform, you can ensure an accurate result “as expected”. Furthermore, you can create more infrastructures if you need better fault tolerance and higher availability.
For monitoring API activity, we use CloudTrail. This is a service for a continuous record of events in an AWS account. You can read more in AWS Documentation.
With that said, we will discuss with examples how you can improve security with AWS tools and services.
Infrastructure security
As we work with the AWS infrastructure as a service, we care that this environment is protected from our side.
For example, when creating any resource, you can run the code through a tfsec security scanner and see what improvements and security-related fixes you can make. These may include adding descriptions for better auditing, as well as reworking security groups' ingress rules. Also, usually, it is essential to allow only inside-VPC traffic, which helps make ingress rules more efficient.
Besides, we recommend using this security group rule resource. Thus you will be able to modify security groups without recreation.
Inventory and configuration management
These operations are necessary to monitor the architecture’s state. For example, thanks to configuration recording, we can see that our server configuration or security groups changed and take some actions in response.
To see the current state of architecture, we use tfsec, terrascan, and dritfctl for security scans and config recording (with Terraform states). Below is a typical layout of Terraform infrastructure.
Cloudwatch metrics filters against the CloudTrail log group help us in work as well by notifying us about changes or unauthorized API activity. We also follow GitOps practices, which enables us to keep updates on the infrastructure configuration in the repository.
Cost control and cost optimization are also vital when building solutions. To optimize the costs, we use Infracost.
Data encryption
Encryption means turning data into a secret code. It conceals the data that you send or store.
In our practice, we do not encrypt all data as it is inefficient. But it is necessary to understand what data need to be encrypted. For example, we encrypt confidential data. We use KMS for that. This is the Amazon service that helps create and control keys for data encryption kept in AWS.
Also, we encrypt a database and place it in private subnets within our subnet group. This is done in combination with a well-made ingress rule and choosing a long username and password (or using IAM authentification). These methods will help you keep your database secure and save you from a lot of problems in the future.
Identity and access
Access control is vital for protecting the environment against unauthorized and harmful actions. So, we use AWS Identity and Access Management (IAM). This instrument helps us create users and assign them certain policies.
So, we can control which AWS resources and services they access. In our practice, we also always use multi-factor authentication (MFA) for console users.
When we need to provide developers or applications with access to AWS, we apply strict policies. For application credentials, we use per-service policies and create separate users and roles.
Monitoring and logging
In simple words, logging means recording information about processes in an application or environment. To do this, we write to them to cloudwatch log streams. You need to set up tools for that.
If monitoring is tuned right, we get notified about downtime in just a few seconds as they appear. Thanks to monitoring, we see if the application stopped working for some reason and understand why there is an issue in performance.
Based on our DevOps security practice, we’ve chosen the Prometheus stack as the best set of tools for our needs. It includes Alertmanager for notifications, Grafana for visualization, and a list of different exporters.
Also, we use Pagerduty to see if there are any alerts. This tool also sends us notifications to a few different endpoints, including Slack and email.
Container security
It means the protection and securing of the containerized environment OS and host OS as well as applications.
In our practice, we use multi-stage Dockerfiles, custom users, and we do not add any sensitive data to Dockerfiles. Other recommendations that come from our experience include packing minimum data to images.
Also, we create images that will not install or pull any updates or similar processes at the start. In our practice, we use docker’s BuildKit and Kaniko image-building engines.
Conclusion
Security is one of the vital aspects of a solution. At Codica, we ensure it with proven tools and by applying best practices. If we get a request from our client on scaling a solution, we are eager to revise the security aspects of the solution architecture.




Top comments (0)