Those days are gone when the blockchain trilemma, saying only two of its three pillars of decentralization, security, and scalability can be accommodated at a time, meant an inevitable trade-off which in most cases was privacy. Blockchain technology has now prioritized implementing privacy-preserving solutions as an essential tool for innovating and securing web3 utility. Oasis has been at the forefront of this privacy-first approach.
Decentralization, scalability, tick please
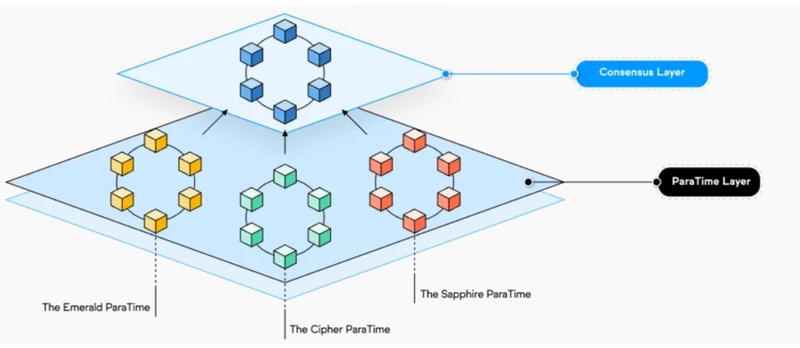
Decentralization was never in question. Scalability is a challenge, of course, but not insurmountable. But the USP of Oasis is its modular architecture.
Oasis separates the consensus layer from the multiple parallel runtimes or paratimes which act as independent computing environments. With smart contract execution functions run in EVM or WASM paratimes which can be confidential or non-confidential, the overarching consensus layer ensures that the nodes follow the rules of the network while also dealing with the generation and verification of blocks. The seamless connection between the two layers and the fact that the paratimes can exist and evolve independently is key to the flexibility and scalability of this design.
Finding the missing puzzle of privacy
Web3 is the overarching use case of blockchain technology where all the decentralized applications or dApps can come into play. The privacy paradox has plagued this space for a long time. Determined to find the ideal solution without compromising a public blockchain's core tenets of decentralization, transparency, and immutability, Oasis introduced the industry’s first-ever and only confidential EVM in production - Sapphire. As a result, it is now possible to enable decentralized confidential computation or DeCC by deploying confidential smart contracts.
At times, the Oasis way of privacy is called smart privacy because it is customizable and amenable to compliance. Customizable means it falls in that confidentiality spectrum where it can be made 100% public or 100% private or anywhere in between. Amenable to compliance means it is private when you need it, and transparent when it matters.
Introducing the privacy-preserving techniques
Since Oasis incorporates customizable privacy-preserving technology as its core enabler of web3 privacy, let's take a look at the most prevalent techniques in use today.
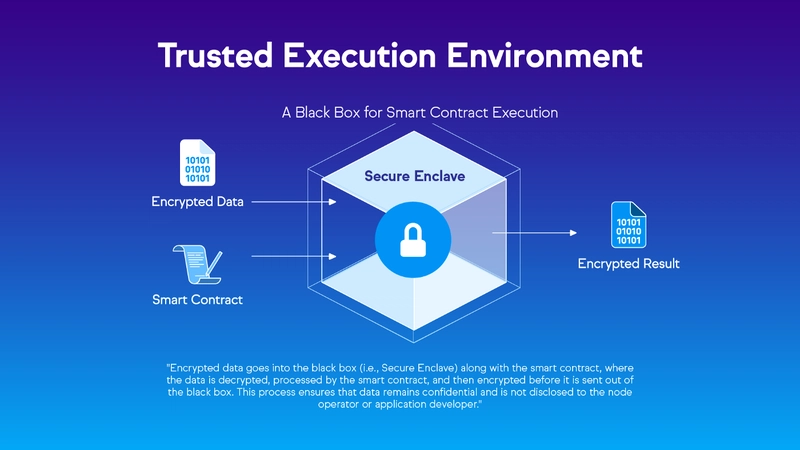
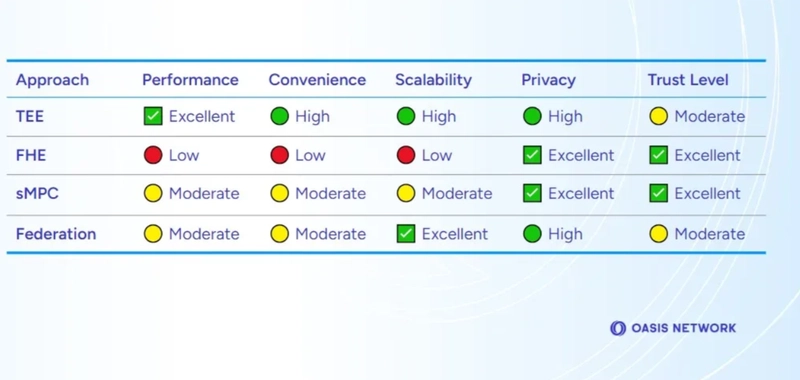
Trusted Execution Environments (TEEs): They are highly impactful in creating web3 privacy by employing black-box-like secure enclaves to run code and data. By eliminating external access even by node operators and dApp developers, a tamper-proof system ensures data privacy and prevents the revealing of any sensitive information.
For example, everyone knows that storing private keys for crypto wallets is a hassle. With TEEs, keys are stored with the highest form of confidentiality and users can securely sign transactions that are immune to breach by external parties.
Zero-knowledge proofs (ZKPs): They are a cryptographic mechanism that can be best used where complex smart contract execution involving aggregation of multiple data sources is not required. This technique relies on verifying a statement of proof without having to share the information in a statement and without revealing how the information was received. If the proof is valid, there will be no need to learn the data that was verified, and still, the computations can be run and state changes can be applied.
Fully homomorphic encryption (FHE): This technique enables computation on encrypted data itself and privacy is maintained as with no data decryption involved, no sensitive information ever gets revealed. This, however, cannot make computations cost-efficient.
Secure multi-party computation (sMPC): This technique is very effective but has the drawback of involving too much communication between the parties meaning unavoidable latencies and high computational overheads.
Ring signatures & Stealth addresses: They are sometimes used when the anonymity of transactions is the main objective. Ring signatures mask which of the several users signing a message is the actual signer. Stealth addresses hide the recipient’s address in a transaction and replace it with a uniquely generated address for each transaction. In both techniques, the transactions remain valid yet highly private.
What is the best bet for privacy?
Each privacy-preserving technique has its own sets of risks and rewards, benefits and trade-offs.
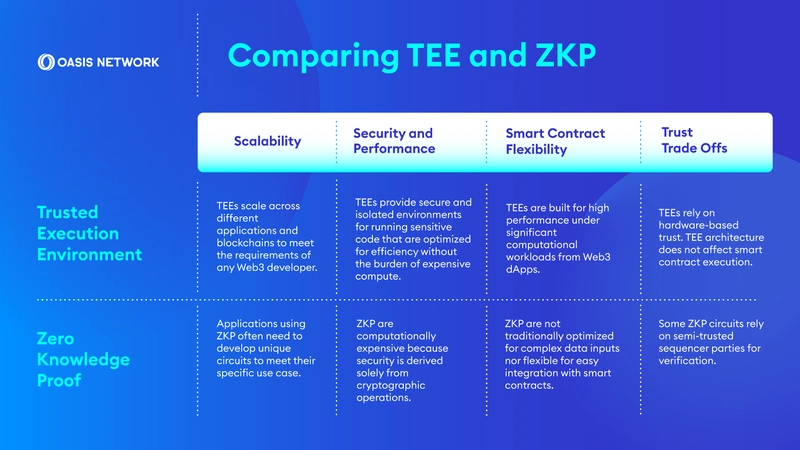
The two techniques that have garnered the most attention with their capabilities and affordability to drive blockchain technology forward are TEEs and ZKPs. It is useful to take a look into them in further detail.
However, the fact remains that web3 is a component of many parts, and as such, not a single privacy technology can be called the only fool-proof way of enabling web3 privacy.
For example, a developer building a dApp involving a large number of concurrent users and humongous datasets can find TEEs to be ideal for integrating confidentiality through end-to-end encryption. But ZKPs are also a force to reckon with, especially for privacy-focused use cases. So, there is scope for utilizing ZKPs to improve the security and robustness of a TEE-based system.
As a result, although Oasis Network uses TEEs, there is the acknowledgment that developers can indeed choose from a combination of tools to ensure the ultimate goal of web3 privacy.
Afternoon TEE Party
Oasis started a brilliant initiative recently where it brought together experts in the field to discuss the scope and impact of TEEs in web3 applications. The first iteration of this Afternoon TEE Party took place in Bangkok last year.
The second iteration of this side event is happening during the ongoing ETHDenver and more than 1k have already registered. Spots are limited, and access is on a first-come, first-served basis, so don't miss out on this event as one of the panels will explore the role of TEEs in the age of AI agents.
In conclusion, we can all agree that data privacy is a fundamental and inalienable right. It therefore stands to reason that data sovereignty can only mean users having complete ownership of their data with full access control of what, with whom, and how much to share. Future-ready web3 dApps will need to be privacy-enabled to ensure this. This is where Oasis, with smart privacy in function and TEEs to implement it, can change web3 for the better.




Top comments (0)