🚀 Authentication
Authentication is the mechanism of associating an incoming request with a set of identifying credentials. The credentials provided are compared to those in a database of the authorised users’ information.
🚀 Identity Vs Trust
Identity can be defined as existential attribute associated with a given object or entity. This attribute is independent, absolute, and constant throughout the object's life. Trust on the other hand can be defined as an object/entity's acquired attribute that is relative and dependent on others. Trust is a derived attribute.
🚀 Traditional Authentication Protocols
I refer to all authentication protocols that depend on a user's Identity as traditional because of the following serious flaws that are in-built in all of them:
- Most platforms discourage authentication in an insecure environment. Secure environments are rare to find especially in restricted and/or public places like airports. Majority of the authentication platforms also cannot differentiate secure and insecure environments used by users.
- Validation of an identity simply means, "If you have the correct keys combination, then you must be the valid owner". How the user gets the correct key combination is irrelevant to the protocol.
- They have no comprehensive ways to detect keys duplication. Valid keys are often used to grant unauthorised access. Most platforms can only detect duplication if a different device is used.
- Once unauthorised access is detected, most entities initiate their nuclear options which not only cut-off the affected user(s) but also subject them to extremely tedious proof of identity methods.
- Since identification credentials do not change that often, tracking someone's activities becomes very easy.
- Users' identity information is scattered among thousands of platforms which make it very hard and expensive to enforce data protection rules within a given jurisdiction i.e. GDPR for platforms within European Economic Area.
- Authentication keys are supposed to either be memorised or managed by a third-party software which could be the source of a leak if not properly vetted before installation. Memorised keys often get lost if the user's memory becomes impaired.
- Most AI and Large Language Models have become so advanced that they can be said to have passed the Turing test. Deep fakes with near perfect abilities to replicate most biometric security features make it extremely hard for an identity-based authentication protocol to differentiate a human from a bot.
🚀 Data-Age Authentication protocol
This describes a data intensive authentication protocol that is based on trust where a cryptographically-signed key with a one-time-password feature in used. This trust key is issued and mutated by the trust organisation. For each successful authentication operation a new trust key with no user identifying data is used.
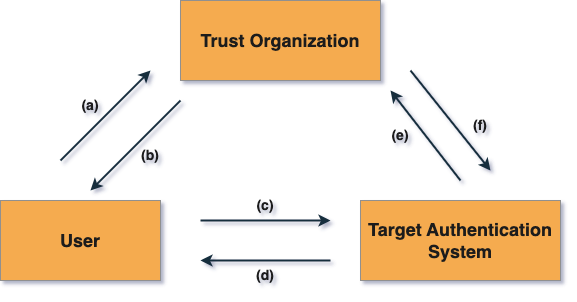
To successfully implement this protocol, the following entities must mutually authenticate each other:
- Trust Organisation - A 3rd party that holds users' personal identification information on behalf of the target system(s).
- Target Authentication System - Requires the trust organization approval to successfully validate a user's trust key.
- User - Carries a trust key that is only backward traceable to the parent trust organisation and is mutated after every successful authentication.
This authentication protocol makes it nearly impossible to identify a specific user during the authentication process and ensures all the authentication operations are unique for the specific trust organisation.
🚀 Strengths of Data-Age authentication over the Traditional Authentication Protocols.
- Advancements of the modern technologies in NFC, powerful GPU's and Ready AI models make it very easy to rollout the protocol in a large-scale. The NFC can used to store an OTP trust key while the AI models and powerful GPU's can be used scale up the efficiency of a trust organisation.
- The OTP nature of the trust key after every successful authentication means that duplicate valid trust keys cannot exist simultaneously.
- Validation using trust key simply means, "The trust key you have and how you use it, determines how much of the valid owner you are". By default, the protocol assumes that every user is malicious/a bot and only grants the necessary permissions depending on the kind of trust held.
- Since personal information is only managed by a few trust organisations on behalf of very many target systems; more user-friendly disaster recovery and business continuity policies can be implemented cheaply.
- The trust key is exclusively stored in an NFC tag, allowing characters longer than an average human being can memorise, to be mutated after every successful authentication.
- GDPR can be best enforced on the few trust organisations that meet the strict requirements needed to safely and securely handle sensitive personal data. This allows a user to be 100% aware of how their personal information is being used.
- Since target systems can no longer identify an individual user, they can monetise the data acquired from the authentication operations with zero risk to the users.
- Mutual authentication for all the three entities involved, implies that any entity that misbehaves it can be punished by the rest. Trust Organisation with malicious users will not be accepted by the Target System, Trust organisation can reject all authentication requests from a malicious target system. Users can also be rejected for being associated with malicious Trust Organisations or Target Systems.
🚀 Conclusion
Identity-based protocols consider the security of the authentication Keys as the individual responsibility of a specific user. The Target Authentication System has minimal to no consequences of mishandling users' sensitive data.
Trust-based protocol considers the security of the authentication keys belonging to a specific user as a collective responsibility of all the entities involved. All the entities involves must be responsible in how they handle the sensitive users' data otherwise grave consequences with follow them.


Top comments (0)