Security is real key thing in any environment and especially on Cloud.In this post I want to put few things that are really essential ( bare minimum ) to keep your AWS environment secure.
Root Access:
Always limit root access only to user creation and billing. It should not be used to create any resources or to perform any other operations on resources.
Implement MFA for root and all users. This will ensure that even if credentials are leaked the other form of authentication is still needed.
Principle of least privilege:
Any resource/role/user should never be given elevated access privileges than required. Always ensure only the required permissions only are granted not more. This will limit the blast radius just in case if there is a compromise in any credentials for any users.
Roles
Always try to use roles where ever possible as roles get temporary tokens to get to a service and they can be revoked if needed.
Services : IAM , Roles
Log everything:
Always log all API calls on all accounts. Use Cloud trail to log all logs to central security account or other and encrypt the logs to implement data integrity.
Logs provide key information in case of any security incident and play a key role in planning risk mitigation. So having all logs in a central location with only limited authorized access ( preferably read only ) will really help in getting to the core of security incident.
Services in AWS : Cloud Trail and S3
Encryption:
It is always best practice to have encryption at rest with all the sensitive data in cloud. AWS has several options depending on where you store the data.
Services : KMS , Cloud HSM , Own keys
Record changes:
It is always recommended to have a record of all changes that happen in any environment. AWS has Config service that allows to assess, audit, and evaluate the configurations of your AWS resources.
AWS config integrates with Cloud watch where cloud based event rules can be configured to notify any changes.
Services : AWS Config , Cloud watch, SNS
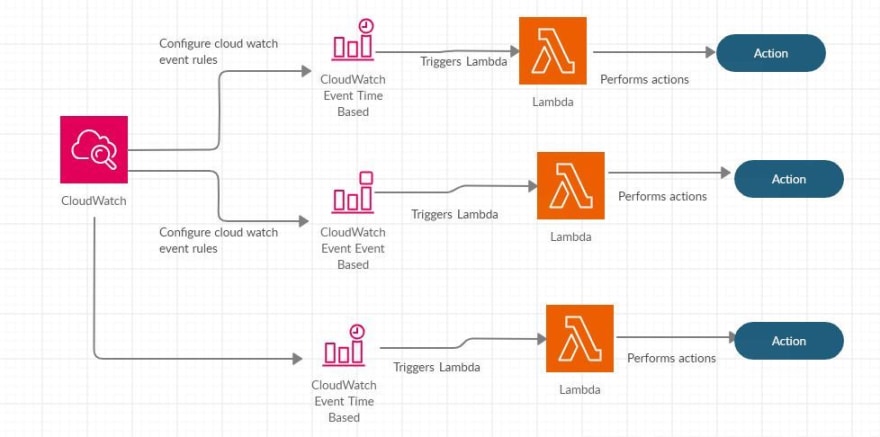
Automate security responses:
The challenge with security compromise is that there is no time on when a security event occurs. Always find ways to automate the security response so the risk of a compromise can be limited.
Use services such as Cloud watch events to trigger event based actions to Lambda so that as soon as something unexpected happens the response is all automated
Services : Cloud watch, Lambda, SNS
Patch regularly:
While there are many managed services on AWS, if your setup has any of the EC2 instances it is always advised to have all of them patched regularly. AWS handles security of the Hypervisor NOT the OS that you use. Understanding this is key in having secure environment for EC2.
Services such as AWS inspector will really help to getting the vulnerability reports for EC2 and AWS patch manager can be leveraged to automate patch cycles.
Services : Patch manager, AWS Inspector
Other key security products:
ACM , AWS Guard duty, AWS shield , AWS WAF are few of the other products for protection against Layer 3/4 and 7 attacks.
Conclusion:
Security is really vast topic and there are many things that still need to implemented depending on where a given environment stands. These are just minimal things that are needed to keep things secure at a very high level.
It is highly recommended to check the AWS security white paper which covers in depth on all aspects.





Top comments (2)
That's eye-opening as I'm not doing most of these, nice contribution!
Thank you !
Some comments may only be visible to logged-in visitors. Sign in to view all comments.