Introduction
In our increasingly interconnected world, the significance of cybersecurity has never been higher. Irrespective of our tech proficiency, we're all potential targets. Here's a comprehensive look at the current cyber landscape and why everyone should be equipped with knowledge. 😎
The Expansive Landscape of Cyber Threats
- Phishing and Spear Phishing
Explanation: Phishing can be likened to a fisherman casting a wide net, hoping to catch anything. Cyber attackers send deceptive emails, hoping that even a small percentage will click on malicious links or provide sensitive info. Spear phishing, however, is targeted. It's like a fisherman who knows exactly what fish he's after and what bait to use. Attackers use personal details, often gleaned from social media, to craft convincing deceptive messages.
Why It Matters: These attacks are especially dangerous because of their deceptive nature. Unsuspecting individuals can inadvertently provide access to personal accounts, leading to financial loss or even identity theft.
- Ransomware
Explanation: Imagine coming home and finding your valuables in a locked safe, with a note demanding payment for the combination. Ransomware operates similarly. Once it infiltrates a system, it locks (encrypts) files, demanding a ransom for their release.
Why It Matters: Beyond immediate financial implications, ransomware poses threats like data loss and operational disruption. For businesses, this could translate to days or even weeks of downtime, causing significant economic impact.
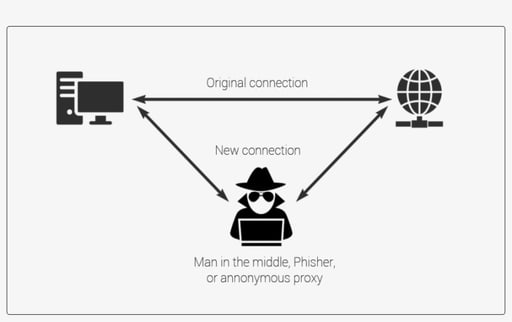
- Man-in-the-Middle Attacks (MitM)
Explanation: These are eavesdropping attacks. Attackers intercept communication between two parties. Think of it as someone secretly listening to your private conversation. This can happen on vulnerable Wi-Fi networks or though malware.
Why It Matters: Such attacks compromise the confidentiality of data. Sensitive information, including passwords or bank details, can be stolen, leading to financial fraud or unauthorized account access.
- Malware and Viruses
Explanation: Malware is a broad category of malicious software, which includes viruses, worms, trojans, and more. These malicious entities can corrupt files, monitor user activities, or provide a backdoor to attackers.
Why It Matters: The implications range from system slowdowns to servere data breaches. Personal, financial, or business data can be compromised, leading to a myriad or consequences.
Essential Practices for Cyber Safety
- Update Regularly
Explanation: Just as one would fix vulnerabilities in a physical structure, software updates patch digital vulnerabilities. Outdated software is a goldmine for cyber attackers.
Why It Matters: Regular updates ensure that known vulnerabilities are patched, significantly reducing potential attack vectors.
- Use Strong, Unique Passwords
Explanation: Passwords are akin to digital locks. Using easily decipherable or duplicate passwords is like using a flimsy lock that's easy to break or pick.
Why It Matters: Strong, unique passwords act as robust barriers, making unauthorized access challenging for attackers.
- Two-factor Authentication (2FA)
Explanation: 2FA adds another layer of security. After entering a password, users are required to provide a second verification, typically a code sent to their mobile.
Why It Matters: Even if an attacker cracks a password, the second layer of authentication acts as a deterrant, safeguarding the account.
- Be Wary of Unknown Links and Attachments
Explanation: Cyber attackers are crafty, often disguising threats as legimate-looking emails or messages.
Why It Matters: Exercising caution prevents inadvertant downloads of malicious software, safeguarding data integrity
- Secure Your Wi-Fi
Explanation: Wi-Fi networks are gateways to the internet. Leaving them unsecured is like leaving your front door open.
Why It Matters: A secured Wi-Fi network ensures that unauthorized individuals cannot snoop on or intercept your data
Advanced Measures for Enhanced Security
- Virtual Private Network (VPN)
Explanation: A VPN acts as a secure tunnel for your data, encrypting it and masking your IP address. It's like sending a letter in a tamper-proof envelope. You can also use a VPN to access content that is only available in another country.
Why It Matters: Especially crucial when using public networks, VPNs ensure data privacy and prevent potential eavesdropping
- Regular Backups
Explanation: Backups are digital safety nets. By regularly backing up data, one ensures that in the face of cyber threats or system failures, a recent copy is always available.
Why It Matters: Backups are especially crucial to mitigate the impact of ransomware, ensuring data isn't permanently lost.
- Educate and Train
Explanation: Knowledge is power. Regular training sessions can keep everyone updated about the latest cyber threats and best practices
Why It Matters: A well-informed individual is less likely to fall prey to scams or phising attempts, acting as a human firewall.
- The Significance of the Human Element
Every individual, regardless of their tech-savviness, plays a vital role in cybersecurity. While tools and software provide substantial protection, it's essential to remember that many cyber attacks aim to exploit human tendencies. Being cautious, staying informed, and always questioning suspicious or too-good-to-be-true offers can make the difference between staying safe and becoming a cyber victim.
Caution with AI Tools
- Understanding AI Conversational Tools
Chatbots or conversational AIs like ChatGPT and Bard etc are designed to generate human-like text based on the input they receive. They don't have emotions, intentions, or consciousness.
- Data Privacy
While many platforms ensure user data is not stored permanently, it's crucial to avoid sharing sensitive personal, financial or propriety information with these tools. Even if data isn't stored, transimitting sensitive information online always carries inherent risks.
- Misinformation
Rely on these tools for general information or entertainment, not critical decisions. Always cross-reference any vital information provided by AI tools with other sources.
- Manipulation Risks
Be ware that just like humans, AI tools can be used maliciously. Malicious actors might deploy AI chatbots to extract information from you. Always be cautious where and how you interact with AI interfaces.
Conclusion
The digital realm, while offering unprecedented conviences, is fraught with risks. By understanding these risks and adopting a proactive approach, everyone can navigate the digital sphere with confidence. Cybersecurity isn't just an IT concern; it's a societal responsibility. 👍
Like me work? I post about a variety of topics, if you would like to see more please like and follow me.
Also I love coffee.
If you are looking to learn Algorithm Patterns to ace the coding interview I recommend the following course
If you are interested in using a VPN, I recommend ExpressVPN. If you use the below link you get 30 days for free






Top comments (0)