This article "Using ColdFusion to Generate Pre-Signed Wasabi Download URL" has been moved to myCFML.
There was an internal decision to use Wasabi Cloud Storage instead of Amazon S3 and I needed to use ColdFusion to generate a pre-signed URL to allow access to AI-generated content for a limited time. I had used the Sv4Util.cfc and aws-cfml libraries before with Amazon and thought it was just as simple, but I got confused somewhere along the way and it just wasn't working.
The Wasabi documention listed several approaches to generate a valid pre-signed URL...
- Using the AWS CLI
- Using the AWS Tools for Powershell
- Using the S3 Browser
- Using Wasabi Explorer
- Using pre-signed S3 URLs for temporary, automated access in your application code
- Python and Boto3
- aws-sdk for Nodejs
- AWS SDK for PHP (V2)
... but none of these solutions were very helpful for my environment and I didn't want to have to fallback to using the command line.
I thought it'd be an easy function for AI to generate, but the results still weren't working.
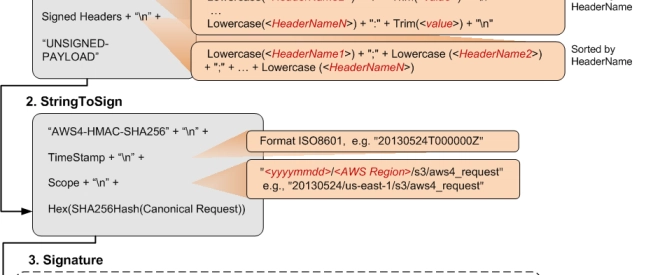
After some additional searches on Google, I came across an Amazon API reference regarding Authenticating Requests: Using Query Parameters (AWS Signature Version 4) and it outlined a step-by-step approach with detail instructions, detailed descriptions and static example (with example output). Whenever I'm working with a third-party API, I always look for basic CURL examples so that I can see all the explicit settings and this example was perfect.
I was able to quickly debug & identify the issues that caused the calculation to be wrong. After finding out how to do it right, I took another look at the aws-cfml library and shared the cfml example with Wasabi (but I don't think they'll update their webpage to include links to AWS documentation or CFML examples.)
While I'm not currently using this generateS3PresignedUrl UDF in production, I thought I'd share it in case other developers can benefit from it.
Source Code
https://gist.github.com/JamoCA/bbdb652e4390898ea27eee489923ede3
Here's an example using the aws-cfml library.
https://gist.github.com/JamoCA/d2d38c5eaacba400decb21010124b159


Top comments (0)