🔘What is ethical hacking?
Ethical hacking, also known as penetration testing or pen testing, is legally breaking into computers and devices to test an organization’s defenses. It involves an authorized attempt to gain unauthorized access to a computer system, application, or data. Thus, unlike malicious hacking, this process is planned, approved, and more importantly, legal.
Ethical hackers improve the security posture of an organization. Ethical hackers use the same tools, tricks, and techniques that malicious hackers used, but with the permission of the authorized person. The purpose of ethical hacking is to improve the security and to defend the systems from attacks by malicious users.
Ethical hackers are often referred to as white-hat hackers. Ethical hackers learn and perform hacking in a professional manner and they are hired by organizations to look into the vulnerabilities of their systems and networks and develop solutions to prevent data breaches.
Types of ethical hacking
We can define hacking into different categories, based on what is being hacked:
· Web application hacking
· Social engineering
· System hacking
· Hacking wireless networks
· Web server hacking
🔘The process of ethical hacking
There is a six-step process that is usually performed by ethical hackers in ethical hacking.
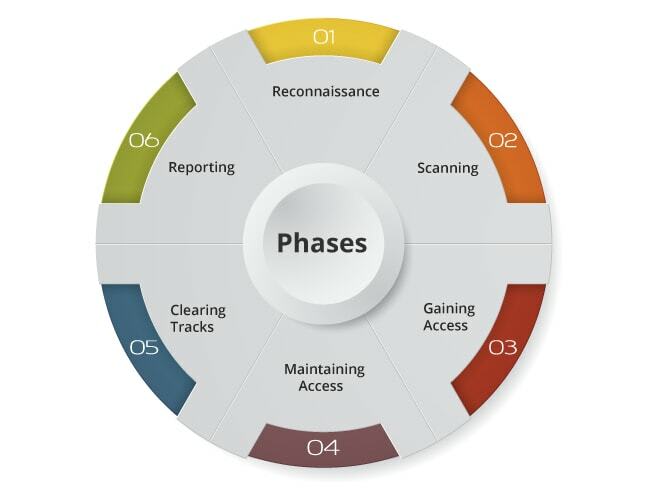
▪ Reconnaissance
It is the principal stage. Here the white-hat hacker attempts to gather information about the objective. It incorporates Identifying the Target, discovering the objective’s IP Address Range, DNS records, Network, and so on.
▪ Scanning
In the stage of scanning, the hacker starts to effectively test an objective machine or organization for weaknesses that can be abused.
▪ Gaining Access
In this stage, the hacker plans the outline of the organization of the objective and concludes that they have a few alternatives to access the organization.
▪ Maintaining Access
In this stage, the hacker has effectively gotten entrance into a framework and introduces a few secondary passages to go into the framework when he needs access in this possessed framework in the future.
▪ Clearing Track
In this stage, hackers clear their track. This step ensures that the attackers leave no clues or evidence behind that could be traced back.
▪ Reporting
In this last stage of the process, the ethical hacker create a report on the findings like weaknesses found in the system and the work that was done.
🔘There are some limitations of ethical hacking=>
💫Limited scope. Ethical hackers cannot progress beyond a defined scope to make an attack successful. However, it’s not unreasonable to discuss out of scope attack potential with the organization.
💫Resource constraints. Malicious hackers don’t have time constraints that ethical hackers often face. Computing power and budget are additional constraints of ethical hackers.
💫Restricted methods. Some organizations ask experts to avoid test cases that lead the servers to crash (e.g., Denial of Service (DoS) attacks).
🔘Benefits of ethical hacking
▪ Implementing a secure computer network that prevents security breaches.
▪ Discovering vulnerabilities from an attacker’s point of view, so that weak points can be fixed.
▪ Helps in taking preventive actions against hackers.
▪ Helps in building a system which prevents any kinds of penetration by hackers.
▪ Gaining the trust of customers and investors by ensuring the security of their products and data.

Thank you very much for reading. Hope you get an idea about Ethical hacking.



Top comments (0)