Amazon Virtual Private Cloud (Amazon VPC)
Amazon VPC is a networking service that users can use to establish boundaries around their AWS resources.
Consider millions of users who use AWS. Imagine the millions of resources that these users have created such as Amazon EC2 instances. Without boundaries across all these resources, there would be an unrestricted network traffic flowing between these resources.
By using Amazon VPC, users can provision an isolated section in the AWS Cloud so that they can launch resources in a virtual network that they define.
Subnets
Subnet is a section of a VPC in which users can group resources based on security or operational needs.
Subnets are of two types as follows:
- Public Subnet - These contain resources that need to be accessible by the public.
- Private Subnet - These contain resources that should be accessible only through user's private network.
In a VPC, subnets can communicate with one other. It means that Public subnet can send or receive data from Private subnet and vice versa.
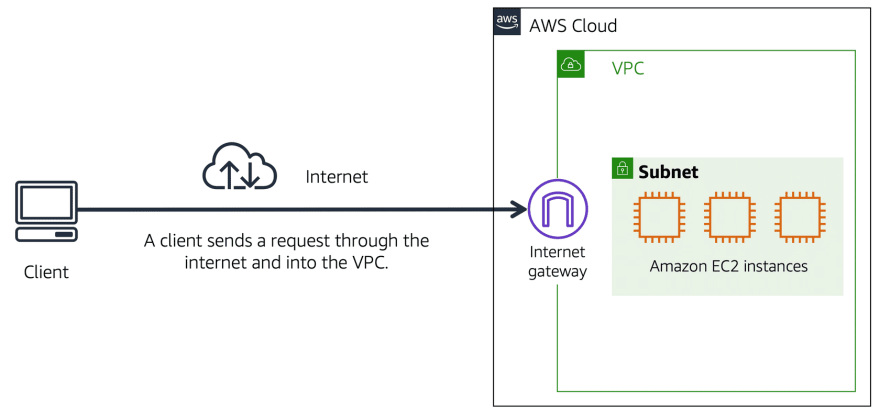
Internet Gateway
An Internet Gateway is a connection between a VPC and the internet. To allow public traffic from the internet to access VPC, users attach an Internet Gateway to the VPC. Without an Internet Gateway, no one can access the resources within your VPC.
Virtual Private Gateway
What if users have a VPC that includes only private resources?
To access private resources in a VPC, users can use a Virtual Private Gateway.
Virtual Private Gateway only allows protected internet traffic (data coming from an approved network) to enter into the VPC. It establishes a Virtual Private Network (VPN) connection between VPC and a private network, such as an on-premises data center.
AWS Direct Connect
AWS Direct Connect is a service that establishes a dedicated private connection between on-premises data center and a VPC. It helps to reduce network costs and increase the amount of bandwidth that can travel through the private network.
Network Access Control Lists (ACLs)
Network Access Control List (ACL) is a virtual firewall that controls inbound and outbound traffic at the subnet level.
Every AWS account includes a default Network ACL. By default, AWS account’s default Network ACL allows all inbound and outbound traffic, but it can be modified by adding own rules. For custom Network ACLs, all inbound and outbound traffic is denied until rules are added to specify which traffic to allow. Additionally, all Network ACLs have an explicit deny rule. This rule ensures that if a packet doesn’t match any of the other rules on the list, the packet is denied.
Network ACLs perform stateless packet filtering. They don't remember anything and check packets that cross the subnet each way: inbound and outbound.
Example - In the airport, travelers are trying to enter into a different country. Think of the travelers as packets and the passport officer as a Network ACL. The passport officer checks travelers ID proof when they are both entering and exiting out of the country. If a traveler is on an approved list, they are able to get through. However, if they are not on the approved list, they cannot come in.
Similarly, consider a request is send out from an Amazon EC2 instance to the internet. When a response for that request comes back to the subnet, the Network ACL does not remember the previous request. The network ACL checks the response against its list of rules to determine whether to allow or deny.
Security Groups
Security Group is a virtual firewall that controls inbound and outbound traffic for an Amazon EC2 instance.
By default, a Security Group denies all inbound traffic and allows all outbound traffic. Users can add custom rules to configure which traffic to allow or deny. If there are multiple instances within a subnet, they can be associated with the same Security Group or use different Security Groups for each instance.
Security Groups perform stateful packet filtering. They remember previous decisions made for incoming packets.
Example - Consider a building with a door attendant who greets the incoming guests. Think of the guests as packets and the door attendant as a Security Group. As guests arrive, the door attendant checks a list to confirm they can enter the building. However, the door attendant does not check the list again when guests are exiting the building.
Similarly, consider a request is send out from an Amazon EC2 instance to the internet. When a response for that request returns back to the instance, the Security Group remembers your previous request. The security group allows the response to proceed, without checking the inbound security group rules.
Please feel free to write @ rewooparth.rp@gmail.com for any queries on Network Security in AWS - Basics & stay tuned for next write-up.
Thank you!












Top comments (0)