This blog post originally appeared on my blog QAInsights.
Recently I read an article about all new Windows network sniffer tool called pktmon which got released in Windows 10 October 2018 update. It took a while to reach the tech community. In this blog post, we will see how to get started with pktmon and a quick walk through.
What is pktmon?
pktmon is a built-in network sniffer for Windows operating system. Just like tcpdump in Linux. pktmon.exe is shipped in Windows 10 October 2018 update. Using pktmon you can diagnose and analyze the network packets.
Other popular network sniffer for Windows is Wireshark.
How to launch pktmon in Windows?
Make sure you have the latest release of Windows. Go to Settings > System > About to check the version. I am using Windows 10 Pro 1909 OS build 18363.836.
To launch pktmon, you need to have administrative privilege, otherwise you may not able to run the program.
You can use Windows Terminal or command prompt to launch pktmon.
pktmon is located under C:\Windows\System32\PktMon.exe location.
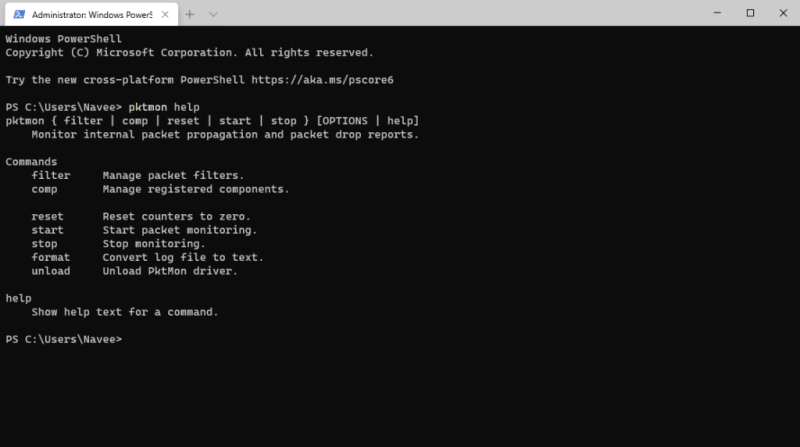
pktmon is a command line utility. You should good in remembering commands to work.
If you need help type pktmon help to view the syntax.
How to capture the network using pktmon?
Let us capture the http traffic of http://example.com. The IP address of http://example.com is 93.184.216.34.
Before we begin monitoring, it is important to configure the filter in pktmon.
Issue the below command to add the port 80 filter. You can add multiple filters as well.
After configuring the filter, you can also add the network interface by issuing the below command. Note down the ID which you can use it in the start command.
To start capturing the network, use the command pktmon start --etw -p 0 and hit enter. This will capture all the interface traffic.
Now launch your favorite browser and open example.com. Once the page is successfully loaded, return to the terminal/command prompt to stop capturing the traffic.
The log file will be generated and placed it in the current directory. ETL file will not be in readable format. You need to convert ETL into TXT file using the below command. Text file will give an overview about the packets.
pktmon format .\PktMon.etl -o output.txt
In the output.txt file, you can search for the example.com IP.
Alternatively, you can also use Microsoft Network Monitor 3.4 to view the ETL file.
After capturing the traffic, you can remove the filter using the below command.
pktmon filter remove
Future release of pktmon will have real time monitoring and converting ETL to PCAPNG format to view the traffic in Wireshark.
How are you planning to use pktmon for your performance testing purposes? Please let me know in the comments.








Top comments (0)