Exam Domains & Weightage:
- General Security Concepts (12%)
- Threats, Vulnerabilities, & Mitigations (22%)
- Security Architecture (18%)
- Security Operations (28%)
- Security Program Management & Oversight (20%)
General Security Concepts (12%)
Key Topics
✅ CIA Triad (Confidentiality, Integrity, Availability)
✅ Access Control Models (RBAC, DAC, MAC, ABAC)
✅ Authentication & Authorization (MFA, SSO, Federated Identity)
✅ Cybersecurity Frameworks (NIST, ISO 27001, CIS Controls)
✅ Common Cybersecurity Roles & Responsibilities
✅ Basic Cryptographic Concepts (Hashing, Symmetric & Asymmetric Encryption)
CIA Triad (Confidentiality, Integrity, Availability)
The CIA Triad is the foundation of cybersecurity. Every security control, policy, or mechanism must align with one or more of these principles.
1️⃣ Confidentiality – Protecting data from unauthorized access.
Example: Encrypting emails using PGP to prevent eavesdropping.
Controls: Encryption (AES, RSA), Access Control (RBAC), MFA, VPNs.
2️⃣ Integrity – Ensuring data remains accurate and unaltered.
Example: A hashing algorithm (SHA-256) ensures a file wasn't modified.
Controls: Digital Signatures, Hashing, Checksums, Data Validation.
3️⃣ Availability – Ensuring data is accessible when needed.
Example: Redundant servers ensure a website stays online even if one server crashes.
Controls: Load Balancers, RAID, Cloud Backups, DDoS Mitigation.
🔹 Real-World Scenario:
A hospital uses role-based access control (RBAC) to restrict patient records to doctors only (Confidentiality). Each update to a patient record is logged and digitally signed (Integrity). The system uses redundant power supplies to ensure medical data is always available (Availability).
✅ Security Mechanisms & CIA Alignment:
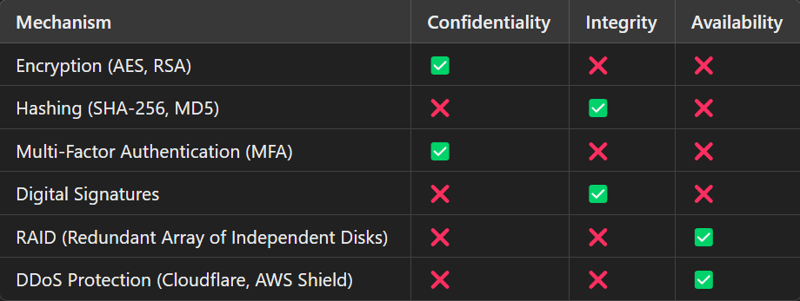
Access Control Models
Access control determines who can access what in a system.
1️⃣ Discretionary Access Control (DAC) – Owner decides access.
Example: A user creates a file and assigns read/write permissions.
Weakness: Susceptible to insider threats.
2️⃣ Mandatory Access Control (MAC) – Enforced by a central authority.
Example: The military uses MAC to classify documents as "Top Secret."
Weakness: Less flexibility, high administrative overhead.
3️⃣ Role-Based Access Control (RBAC) – Permissions assigned by role.
Example: Employees in HR can access payroll records, IT cannot.
Best for: Businesses & organizations.
4️⃣ Attribute-Based Access Control (ABAC) – Permissions based on conditions.
Example: A doctor can only access patient records during their shift.
Best for: Dynamic & cloud environments.
🔹 Real-World Scenario:
A hospital uses RBAC to ensure that only doctors can access medical records, and nurses can access only certain patient details. An ABAC system adds a rule that limits access to working hours and physical location of the hospital.
🔹 Authentication & Authorization
🔹 Authentication = Verifying identity (e.g., passwords, biometrics).
🔹 Authorization = Granting access based on permissions.
✅ Common Authentication Methods :
1️⃣ Single-Factor Authentication (SFA) – Just a password (Weak).
2️⃣ Two-Factor Authentication (2FA) – Password + OTP (Better).
3️⃣ Multi-Factor Authentication (MFA) – Password + OTP + Biometrics (Best).
4️⃣ Federated Identity – Use a third-party identity provider (Google Login, SAML).
🔹 Real-World Scenario:
When logging into a banking app, users enter their password (something they know) and receive an OTP via SMS (something they have). This is 2FA.
Cybersecurity Frameworks
These help organizations manage cybersecurity risks.
1️⃣ NIST Cybersecurity Framework (CSF)
Five core functions: Identify, Protect, Detect, Respond, Recover
Best for: Government agencies & enterprises.
2️⃣ ISO 27001 – International standard for Information Security Management Systems (ISMS).
Best for: Global businesses needing compliance.
3️⃣ CIS Controls – 18 security controls (e.g., asset management, logging).
Best for: Small businesses.
🔹 Real-World Scenario:
A healthcare company follows HIPAA (a U.S. standard) and implements ISO 27001 to ensure strong security policies.
Cryptographic Concepts
Encryption is key to confidentiality.
✅ Types of Encryption
1️⃣ Symmetric (AES, DES, 3DES) – One key for encryption & decryption.
Fast but less secure (key distribution is a challenge).
2️⃣ Asymmetric (RSA, ECC) – Public & private key pair.
Used in SSL/TLS for secure communication.
✅ Hashing (SHA-256, MD5, HMAC)
Ensures integrity (not reversible).
Digital Signatures use hashing + encryption to verify authenticity.
🔹 Real-World Scenario:
When you visit a secure website (HTTPS), your browser uses RSA encryption to establish a secure connection.
Next post will cover 'Threats, Vulnerabilities, and Mitigations'. Stay Tuned ...



Top comments (0)
Some comments may only be visible to logged-in visitors. Sign in to view all comments.