Introduction
From malware to phishing attacks, the internet is full of potential security risks that can compromise your business and your customers' data. Fortunately, Cloudflare Tunnels (formerly called Argo Tunnels) can help you defend against a few common attack vectors.
In this post, we will discuss how Cloudflare Tunnels work, and how you can use them to successfully secure your network. We will also talk about how they can be used to expose self-hosted services to the internet without messing with your router configuration. Finally, we will address a few frequently asked questions about Cloudflare Tunnels.
How do Cloudflare Tunnels work?
Cloudflare Tunnels work by creating persistent outbound connections to Cloudflare's data centers. When an external request is made to your server, it will pass through Cloudflare's data centers before being "routed" to your server through the connection opened earlier. Since visitors never make direct requests to your server, they never know its IP address. This protects you from attacks like Denial of Service (DoS), brute force, or port scanning.
One major benefit of Cloudflare Tunnels is the server never needs to accept any inbound requests for the tunnel to work. Most networks will block incoming requests and allow outgoing requests unless they're configured to do something else. Typically, one might allow incoming requests to expose a service to visitors; doing this comes with the potential for attacks discussed earlier. With Cloudflare Tunnels, you can expose your service without allowing incoming requests. This also allows you to expose services behind a NAT like a typical home router.
Getting started with Cloudflare Tunnels
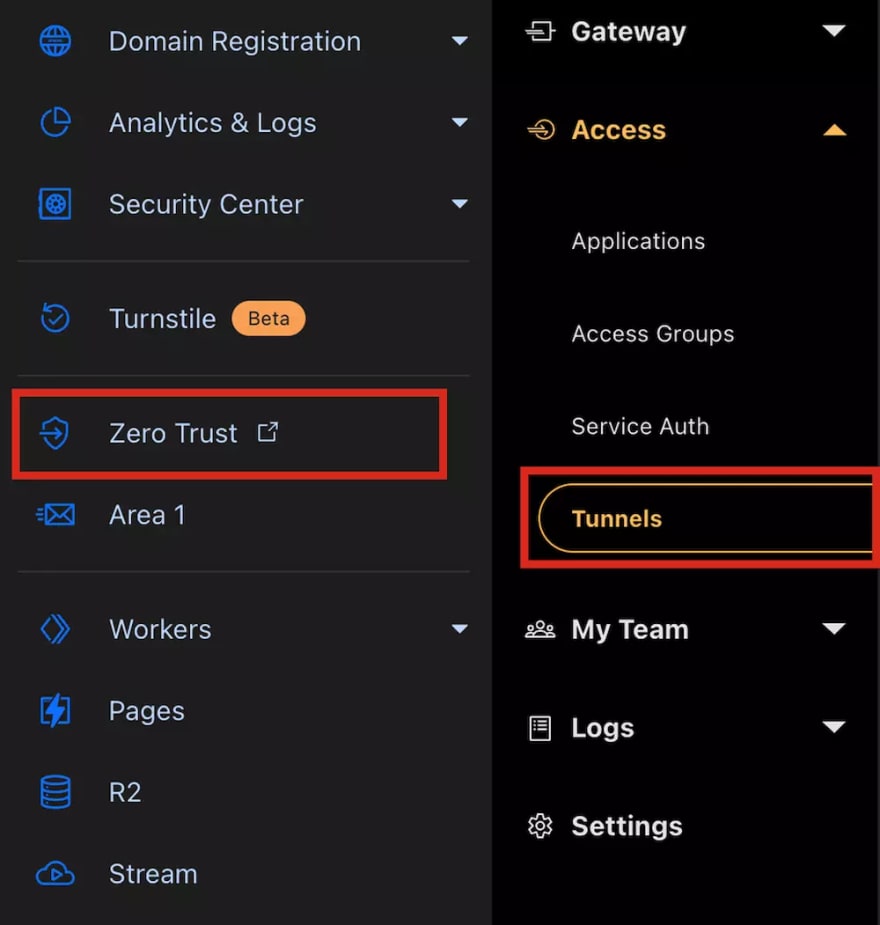
Before starting with Cloudflare Tunnels, you will need a Cloudflare account (duh) with at least one domain. If you don't have a Cloudflare account, you can make one for free on their front page. Then head over to the Zero Trust panel (on the left) then click on Tunnels under Access on the left:
Then follow the instructions to install the Cloudflare connector on your system. Now you can add a public hostname (the URI visitors will use) and a private hostname (the URL that's accessible internally), and Cloudflare Tunnels will automagically make your private service available publicly.
💡
If you are using a self-signed certificate, you will need to tell Cloudflare to ignore the validity of the certificate. You can do this by enabling "No TLS Verify" under the TLS settings.
Restricting access to a Cloudflare Tunnel
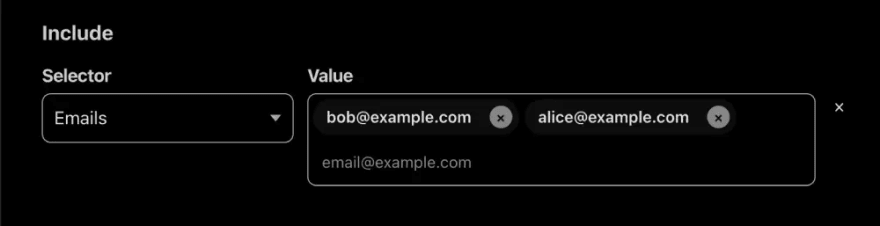
If you want to expose your service to known visitors only, you can add the service as an application and configure a custom access policy. To do this, click on Applications under Access , and add an application. Choose Self-hosted as the application type. Enter the URL you want to restrict and select an Identity Provider. The default provider is a one-time PIN sent to the visitor's email; you can add additional identity providers in the Authentication section in the Zero Trust panel. Next, add your desired rules to your policy. For example, if you only want Bob or Alice to access the service, you can add a rule like this:
Frequently Asked Questions
What's the difference between Cloudflare Tunnels and a VPN?
While both Cloudflare Tunnels and VPNs can help you protect your network, they work in fundamentally different ways. A VPN, as the name suggests, is a private network of hosts. Only hosts inside the network are able to communicate with each other. On the other hand, Cloudflare Tunnels are a secure connection between a host and Cloudflare's servers, and anyone can access the host with Cloudflare acting as a middleman.
How do Cloudflare Tunnels protect against DDoS attacks?
Cloudflare Tunnels route all the traffic your service receives through its servers. Any bad actor wanting to DDoS your service will need to go through Cloudflare first. Cloudflare is an industry leader in DDoS mitigation with an enormous 24 TBps network, making it extremely resistant to DDoS attacks.
What ports do Cloudflare Tunnels use?
Cloudflare Tunnels use port 7844 to establish an outgoing connection to their servers.
I don't want to use Cloudflare, are there any other Tunnels I can use?
Yes, there are other tunnelling services available if you do not want to use Cloudflare Tunnels. Some popular alternatives include ngrok, Dataplicity, and PageKite. Each of these services has its own unique features and benefits, and you should consider which one best suits your needs before making a decision.
If you want a self-hosted solution, consider frp (fast reverse proxy), localtunnel, and sshuttle.



Top comments (0)