AWS: Trusted Advisor, part 1 - features overview
AWS Trusted Advisor is another service that allows monitoring your accountant its resources in use for their cost-effectiveness, performance, security, and more.
Keep in mind, that Trusted Advisor’s checks that are available for you depend on the AWS Support Plan of your account. вашего аккаунта. Fortunately, we have Premium so I’m able to how all Trusted Advisor’s features.
Check its general documentation on the AWS Trusted Advisor check reference page, and documentation about its checks here — AWS Trusted Advisor check reference.
- Cost optimization
- Performance
- Security
- How can I find a resource that is using a specific AWS SecurityGroup?
- Fault tolerance
- Service limits
- Preferences
Go to the AWS Console > Trusted Advisor, enable it, and you’ll see a dashboard with its recommendations:
Here:
- Action recommended : Trusted Advisor believes that you have to pay attention asap as there is something serious, for example — a leak of an IAM key
- Investigation recommended : Trusted Advisor believes, that you have to pay attention to check some services, for example when you’re about some AWS service’s quotes
- Excluded items : well — just exclusions
And on the left side, you’ll see its categories — cost optimization, performance, and so on, where all checks are grouped.
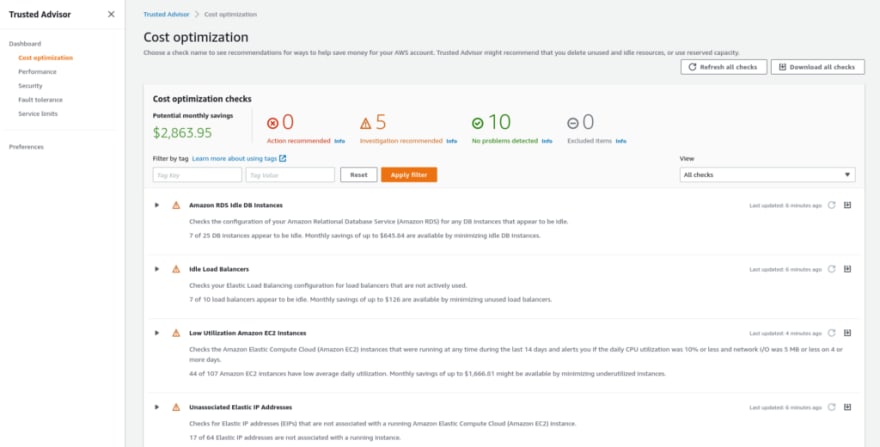
Cost optimization
Let’s start from the Cost optimization category, as it’s the most interesting for me now.
Go to the category and you’ll see a list of findings:
For example, let’s examine the Amazon RDS Idle DB Instancescheck_:_
So, here we can see that Trusted Advisor found some RDS servers that are not being used.
Go to check on of them:
Indeed, the server has had no CPU load, and even no connection for the last week, so it’s good to point to delete it or downgrade to a cheaper instance type.
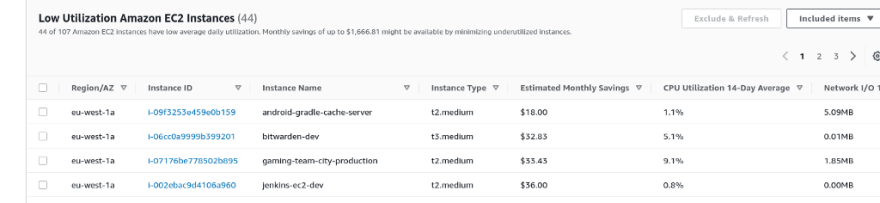
Similar findings for the EC2 service:
Performance
Just what it sounds like, here are finding of everything that possibly affects the performance of your AWS services used:
For example, let’s take a look at the Large Number of EC2 Security Group Rules Applied to an Instance check:
Will be interesting to run some performance tests using different Security Groups.
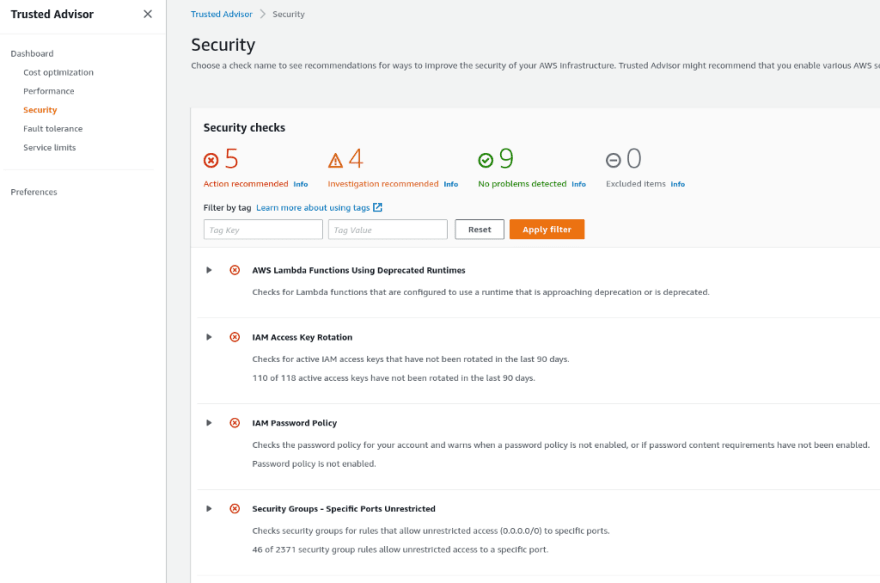
Security
And the very interesting part is the Security:
Expected for me, we have a notification that our IAM keys are not being rotated, and it’s a good point to review.
Also, a helpful check is the Security Groups — Unrestricted Access:
And really — there is a SecurityGroup (SG) with full access to the Internet:
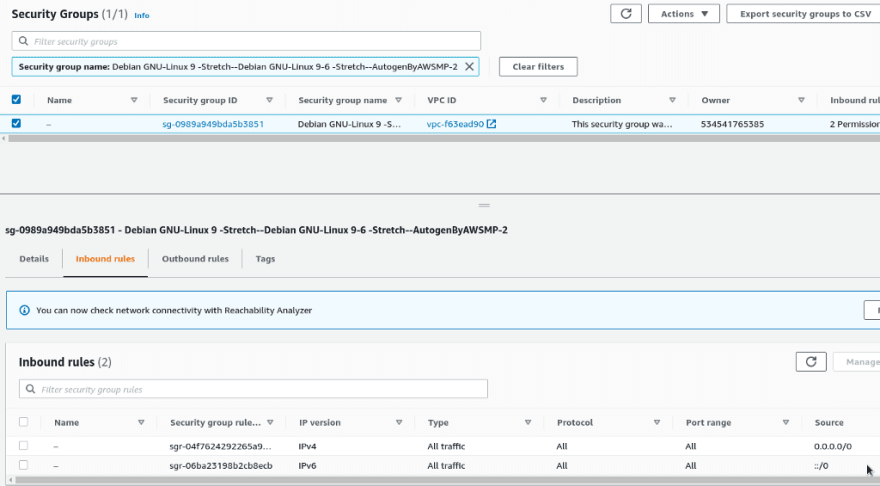
How can I find a resource that is using a specific AWS SecurityGroup?
Copy a group’s ID группы, go to the EC2 > Network Interfaces, and look for interfaces by using this ID:
On the right side, you can see an Instance ID which has this ENI (AWS Elastic network Interface) attached and, respectfully, the SecurityGroup used.
In case of the “No matching network interfaces found” error, the SG isn’t attached to any resources and thus can be removed.
Also, a good check is about LoadBalancer Listeners, that haven’t SSL configured:
Fault tolerance
Here we have findings, that are related to your resources stability:
For example, we have some RDS servers deployed as a Single-AZ instead of being deployed to a few data centers:
Service limits
And the last category is the Service limits, where you can find notifications about AWS Quotes that soon can be reached or are already reached:
In the case of the VPC service quotas, now we are warned that we will not be able to create a new AWS VPC in the us-east-1 region:
Preferences
In the Preferences you can configure emails to be sent with the latest findings:
Also, for the monitoring purpose, you can configure AWS CloudWatch Alarms, and send its notifications to a Slack channel.
Read more bout this in the second part of this post — AWS: Trusted Advisor, part 2 — CloudWatch Alarms and Slack notifications.
Originally published at RTFM: Linux, DevOps, and system administration.
















Top comments (0)