This week was a big one for the authentication part of starchart, or it should have been.
I started this week by taking up an issue I had written to add a SAML Server that configures the Identity Provider and the Service Provider objects from SAMLIFY with the appropriate metadata and settings and although the authentication flow seems to work I kind of doubt that it really does.
This week started with me pulling from the Offical SAMLIFY docs and the Remix SAML example. I got the authentication process to work but I did not add signature requirements or validation of signatures, and I was also importing the sp and idp objects and exposing them in every file where there was supposed to be some SAMLIFY logic, and I also fetched the idp xml metadata from the endpoint the simple saml php container exposes it on, I changed this in a consequent commit so that we have the file locally and read it using fs, all of this is kind of subject to change and that is the essence of the problem.
This week I got my PR in on Thursday, which is pretty late, especially considering there was an influx of other PRs that would come in on the weekend as well, for a PR that has as many problems as mine does (currently 46 comments and probably more to come), the weekend is not enough time to sort it all out and land it properly. So one of the take aways from this week is to either make smaller PRs or get the PR up earlier in the week, in any case be more pro-active.
Now about failure
My code has a lot of problems, for example I keep on missing potential simplification by adding guard clauses on my conditional logic and I exposed the IDP and SP when I could have kept the SAMLIFY objects localized to a file and only exported functionality, and there are a bunch of other things like not to put else conditions after returns which I did on some of my redirects.
Apart from these better coding practices I am failing to fundamentally achieve my goal in understanding exactly how to get this SAML process to work. I initially thought that I wanted every request and response signed, then I thought that I just want my assertions from the IDP signed, then I realized more recently that those are not being signed despite me specifying in the SP config that they ought to be because in the extract there should be an additional signature attribute for claims I believe.
Something like this:
{
samlContent: "<samlp:Response ...",
extract: {
audience: "https://sp.example.org/sso/metadata",
attribute: {
email: "user@esaml2.com",
lastName: "Samuel",
firstName: "E"
},
conditions: {
notbefore: "2015-10-26T11:41:43.500Z"
notonorafter: "2015-10-26T11:46:43.500Z"
},
issuer: ['https://sp.example.org/sso/metadata'],
nameID: "user@esaml2.com"
signature: "<Signature ... </Signature>",
statuscode: {
value: "urn:oasis:names:tc:SAML:2.0:status:Success"
}
}
}
https://github.com/tngan/samlify/blob/master/docs/saml-response.md
Granted our extract looks really similar, the signature field wasn't there last I checked.
EDIT: Upon closer examination we might be getting it signed actually, I was only looking at the extract but the signature is not WITHIN the extract object, I will double check this soon. Could it be that I am too quick to write off what I make as bad? Tune in in 20 mins to find out.
EDIT 2: WSL and Docker are acting up again.
I am doing my best to quickly learn about and fix the things I don't know but the documentation is not as easy to navigate as I thought. There's not a great deal of detail in it despite the presentation being great.
As it stands I do not really know how I am going to go about parsing the response from logout, or whether SP initiated logout is even supported using SAMLIFY. What I wrote "works" but it also isn't being validated and I don't really know what I did. I know that I configured a POST binding for logout and that it manifests as a get request on the callback route but the way that I make the logout request and how the response comes back as a query param and then parsing it, I have a lot of work to do to figure out if that is the correct way of doing it and then how to do it.
I have taken to trying to also look through some of the test cases for inspiration but sometimes I feel like it just makes my head hurt more than it helps. This idea that the POST binding acts like a REDIRECT for logouts is already weird and reading stuff like this
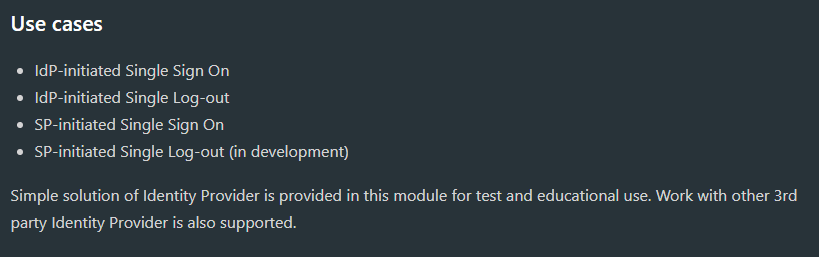
in the docs makes me wonder if I am trying to do something that can't be done in the first place.
In any case there are clear next steps, clean up my code and land this signature-less, essentially validation-less SAML code because it works well enough to get logged in with the local IDP, then get the signature working on the assertions, unless it's the message that I am supposed to sign, not the assertions, because those are separate things and now I am unsure about that as well. Then figure out logout properly, also does logout have to be signed? Also, are the dependencies for the XML validator that I imported good?
I'm making a mess of things again, but that's not always bad, hence the title.
Failing Forward
I mean, I did add a saml server, a few callbacks and actually login and out through simple saml php idp from the docker container so that's something I guess.


Top comments (0)