Fuzz Testing Overview
Fuzz testing, often called fuzzing, is a software testing technique used to identify vulnerabilities and flaws in computer programs, specifically in software applications, operating systems, and network protocols. The technique involves sending intentionally malformed or random data inputs to a target program to observe its response. The primary objective of fuzz testing is to detect security vulnerabilities, unforeseen behavior, system failures, stability concerns, or any other anomalies inside the targeted software.
Types of Fuzz Testing
Here are some common fuzz testing types:
• API Fuzzing: It targets Application Programming Interfaces (APIs) to find vulnerabilities and defects in software libraries or services that provide these APIs.
• Input Fuzzing: It modifies input data sent to the program, including command-line arguments, file inputs, and user inputs.
• File Format Fuzzing: It focuses on testing file parsers and interpreters for different file formats like PDF, JPEG, or Office documents.
• Mutation Fuzzing: It randomly alters valid input data by flipping bits, inserting or deleting characters, or making minor changes to test program robustness.
• Protocol Fuzzing: It tests network protocols and communication by sending malformed or unexpected data packets.
• Generation Fuzzing: It creates entirely new input data from scratch, often conforming to the target's input specifications.
• Web Fuzzing: It involves applying fuzzing techniques to web applications by sending malformed HTTP requests, forms, or URL parameters.
• Differential Fuzzing: It compares the behavior of two similar programs, often one being a reference implementation, to uncover discrepancies.
• Smart Fuzzing: It uses intelligent algorithms to prioritize and guide the fuzzing process for more efficient bug discovery.
• Grammar-Based Fuzzing: It includes grammar rules to generate valid and invalid input data, ensuring comprehensive test coverage.
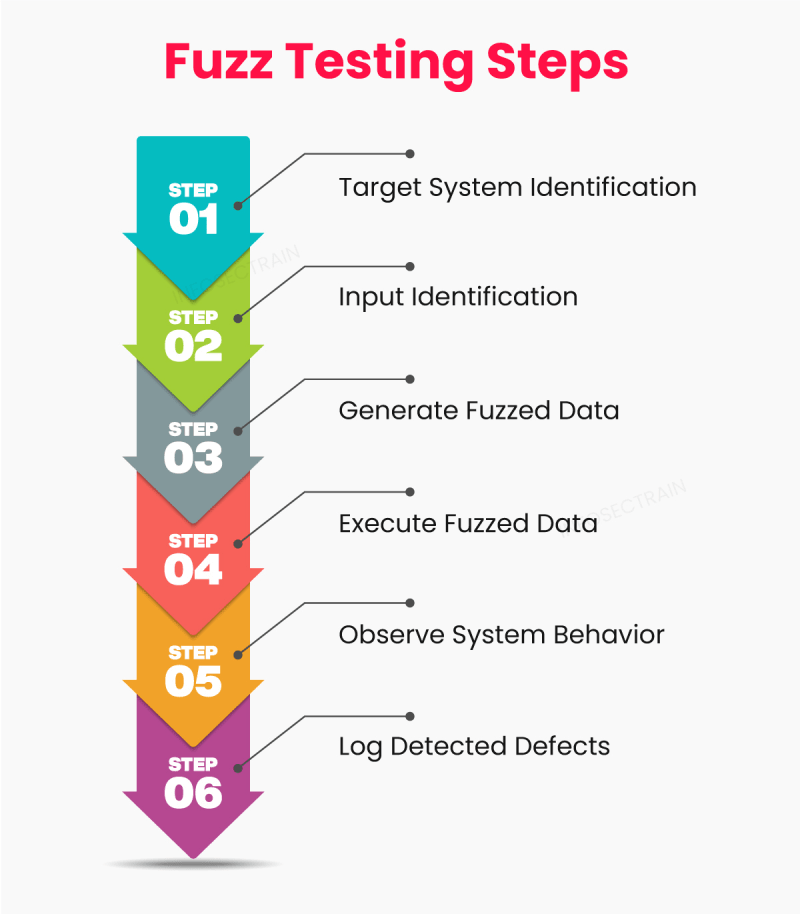
How does Fuzz Testing Work?
Here are the steps of fuzz testing:
1. Target System Identification: Choose the system or software component to test for vulnerability.
2. Input Identification: Identify the various input points or interfaces where the system interacts with external data.
3. Generate Fuzzed Data: Create a diverse input data set, including malformed, random, and boundary test cases.
4. Execute Fuzzed Data: Inject the generated data into the target system through input interfaces.
5. Observe System Behavior: Monitor the system's behavior to detect crashes, hangs, or unexpected responses.
6. Log Detected Defects: Record and document any issues or defects identified during the fuzz testing process for further analysis and remediation.
Related blogs:
● Top Penetration Testing Trends to Follow
● How to Build a Successful Career in Security Testing in 2023?
● Black Box vs. White Box vs. Grey Box Penetration Testing
● Difference Between Internal and External Penetration Testing
How can InfosecTrain Help?
Acquire an in-depth understanding of fuzzing and its associated techniques through InfosecTrain's CompTIA CySA+ and CPENT (Certified Penetration Testing) certification training courses. These courses provide participants with thorough insights into fuzz testing, enhancing their expertise in security assessment and vulnerability identification.



Top comments (0)