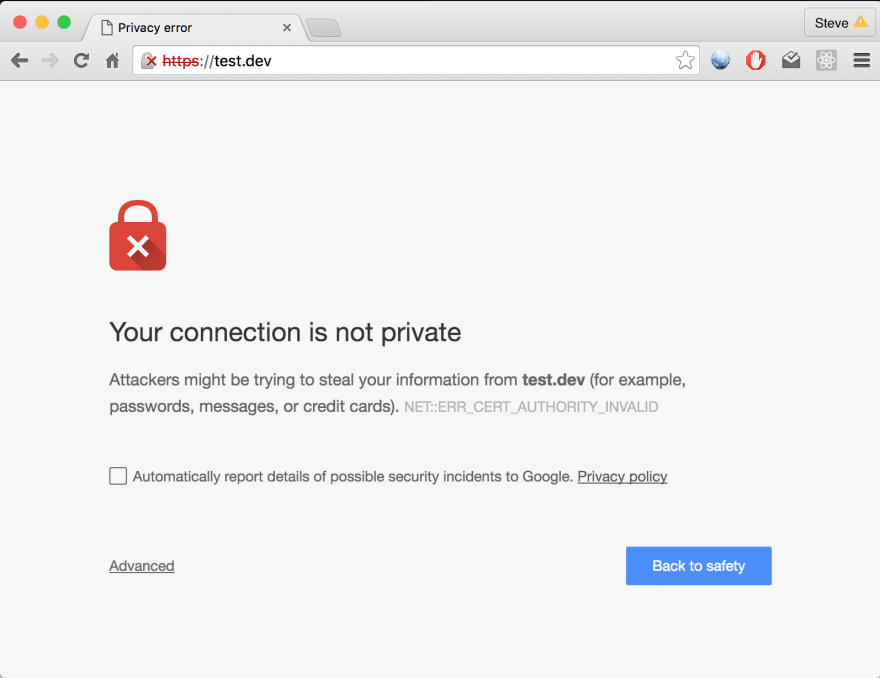
Certificates are one of those terms that are redefined for you once you embark on the journey of learning web development. It was certainly discussed in college within my computer science curriculum, but if you hadn't taken a network security class I'd imagine certificates may have come up within an exploration into encryption, networks or privacy of some sort. For those not in tech, your relationship to them might arise only when a reference to certificates appears in puzzling ways, like the following screen I'm sure many of us are somewhat familiar with:
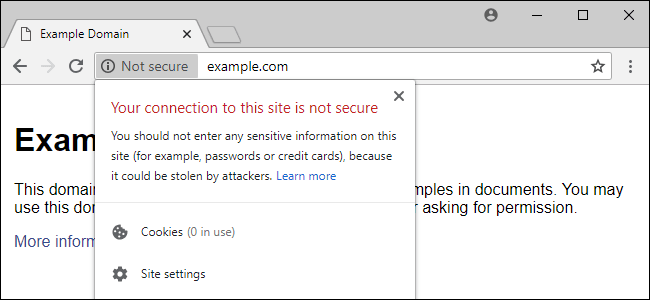
Or the details within this top-left lock icon on Chrome that some may or may not know are always accessible:
I was interested in revisiting what I had learned in my network security class 3 years ago as well as closing a few other broad gaps I had in the field. So, I gathered some answers and thought to share my findings here.
HTTPS and Handshakes
Before we dive in, there's a few concepts I want to surface that ties all of this together. The first one being the HTTPS protocol. The internet in all its glorious pandemonium of networks was created with rules in place to ensure the safety of those who surf and store their secrets within it. These rules are known as the HTTPS protocol. It's job is to secure and encrypt data going back and forth between you and a website.
Handshake is another one of those terms that we are going to redefine. In network security, a handshake is a series of steps that must take place in order to ensure a secure connection has been established. The "handshake" term comes from the idea that the client and server need to establish trust, much like a handshake can do for people. The steps to establish this trust include:
- Client says "hello" by providing information needed to communicate with server
- Server says "hello" by providing information needed to communicate with client
- Client authenticates the server's certificate
- Client creates a "secret" for the session and encrypts the secret with the server's public key. It sends the encrypted secret to the server
- Server decrypts secret with its private key. Server and Client generate the secret with the agreed upon cipher
- Client and server exchange messages to confirm future messages will be encrypted
User vs Website Certificates
In another swing of clarity, I want to distinguish between what is a user certificate and what is a website certificate.
User certificates help the server to authenticate your identity. Some examples of where they can come up are: signing into a VPN, using a bank card or using an ID card to gain access to a building.
Website certificates validate that the user is actually connected to the site they think they are connected to so that the process of encrypting communications between the client and server can begin.
When you tour an apartment complex, you have to give your driver's license to the tour guide beforehand. This is to ensure two things: 1 - ensure your identity should anything suspicious happen and 2 - hold you accountable for maintaining good behavior. This is similar to the concept of how certificates verify identify and establish trust.
Certification Authorities
How does one actually get a certificate for their website? Certificates are issued by a trusted Certification Authority, or CA. A natural next question may be how does one become a CA? Various organizations can become a CA, from private companies to governments. Browsers, operating systems, and mobile devices hold CA membership programs where you must meet strict criteria to become a member. Once you're in, your certificates can be trusted.
Secure Sockets Layer
While there are a variety of certificates, Secure Sockets Layer or SSL Certificates are currently the preferred certificate of choice - particularly for websites involving purchases, authentication or storing information about you because it encrypts the connection between you and the site. There are various types of SSL Certificates you can obtain. While the encryption process is the same for all of them, what differs is the process of verification and screening needed for each one.
Here's a wonderful analogy from GoDaddy in regards to the purpose of SSL Certificates - "Think of an SSL certificate as a giant windshield for when you drive on the information super-highway." SSL is a way to protect you from the bad-intentioned web creatures looking for vulnerabilities in your connection to compromise your data.
Transport Layer Security
The next-in-line and improved version of SSL is known as Transport Layer Security, or TLS. The TLS protocol functions very similarly to SSL, but with more secure features. SSL is still such a commonly used and more familiar term however, that often you'll find companies selling SSL certificates that actually allow for both SSL and TLS protocols to take place.
This mini expedition into a few of the words that kept coming up while being in the web development space helped me make sense of more of the conversations happening around security. During this particularly demanding time of information exchange, this could be the start of a journey rooted in creating a safer, more reliable internet experience for everyone.
Shoutout to Arana Studio for the certificate animation on the cover




Top comments (0)