In this article, we are going to learn building a Clean Architecture application using ASP.NET Core Web API and Angular 11 Front End.
Overview
Building an ASP.NET Core WebAPI using Clean Architecture
Features:
- ASP.NET Core 3.1 Web API.
- API Versioning
- Swagger UI.
- JWT Token Authentication
- Global Error Handler Middleware
- CQRS ( Command Query Responsibility Segregation)
- MediatR
- NHibernate ORM
- Generic Repository Pattern
- Fluent Validation
- SQLSERVER
Github Project
You can refer to the below GitHub project for complete implementation.
 sunilkumarmedium
/
CleanArchitectureApp
sunilkumarmedium
/
CleanArchitectureApp
Clean Architecture Application Design from Scratch using Dotnet Core 3.1 WebApi and Angular 11 FrontEnd
CleanArchitectureApp
Clean Architecture Application Design from Scratch using Dotnet Core 3.1 WebApi and Angular 11 FrontEnd
Technologies
- ASP.NET Core 3.1
- NHibernate
- Angular 11
- Angular CLI 11
- Clean Architecture
- Swashbuckle.AspNetCore.Swagger
- Design Pattern: Command Query Responsibility Segregation (CQRS)
- Fluent Validation
- WebAPI Global Exception Middleware
- Login, Logout and Forgot Password using JWT tokens
- Microsoft Sql Server and Postgresql supported.
Pre-requisites
- .Net core 3.1 SDK
- Visual studio 2019 OR VSCode with C# extension
- NodeJs (Latest LTS)
- Microsoft SQL Server (Optional: If MS SQL server required instead of Sqlite during development)
- POSTGRESQL
Configuration
- Clone the repo: git clone https://github.com/sunilkumarmedium/CleanArchitectureApp.git
- Execute the sql scripts available in the folder
/sql/- MSSQL use CleanArchitectureDB.sql
- POSTGRES use CleanArchitectureDB-Postgres
- Change the database connectionstring in appsettings.json
- Path : CleanArchitectureApp.WebApi/appsettings.Development.json or appsettings.json
-
"DBProvider": "MSSQL" ,UseMSSQLto connect to Microsoft SqlServer OrPOSTGRESto connect to PostgreSQL database "ConnectionStrings": { "MSSQLConnection": "Data Source=DESKTOP-SUNILBO;Initial Catalog=CleanArchitectureDB;User ID=sa;Password=xxx;MultipleActiveResultSets=True", "PostgresConnection": "Server=127.0.0.1;Port=5432;Database=CleanArchitectureDB;User Id=postgres;Password=xxx;Timeout=30;TimeZone=UTC" }'
- cd to…
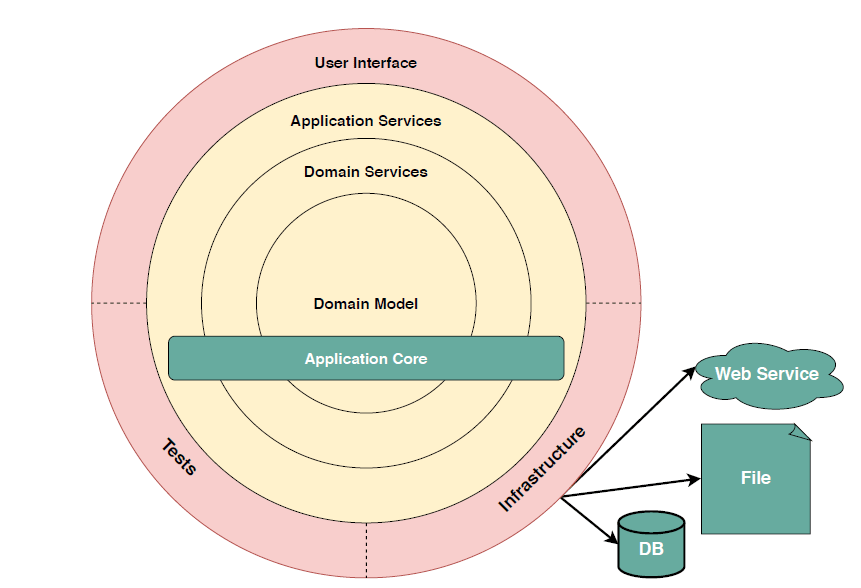
Clean Architecture
The architecture defines where the application performs its core functionality and how that functionality interacts with things like the database and the user interface. Clean architecture refers to organizing the project so that it’s easy to understand and easy to change as the project grows.Command Query Responsibility Segregation is a design pattern to separate the read and write processes of your application. Read operations are called Queries and write operations are called Commands.
Swagger UI Setup
The swagger object model and middleware exposes the JSON objects as Endpoints
Installing Swagger packages using NuGet package console with the below command.
Install-Package Swashbuckle.AspNetCore -Version 5.6.3
Swagger Configuration with Bearer token Authentication
JWT Token Implementation
The JWT Bearer Token is used for accessing the WebApi endpoints securely. Below is the JWT configuration
Token Generation On Successful Login
Global Error Middleware
Server Internal Error Exceptions and Business Validation Exceptions are handled and the response is returned for use of displaying these validations in UI.
NHibernate ORM and Generic Repository Pattern
NHibernate is used to interact with the database. Singleton Session factory is implemented. Below is the Persistence Layer Service Extension.
User Entity
UserMap
Fluent Validation
Package Reference:
<PackageReference Include=”FluentValidation.DependencyInjectionExtensions” Version=”9.3.0" />
To define a set of validation rules for a particular object, you will need to create a class that inherits from AbstractValidator, where T is the type of class that you wish to validate.
Below is the sample Create User Validations.
Summary
Hope enjoyed my first article please feel free to download the code and play around. Next article we will get in touch with Angular 11.
Series Links
Building an ASP.NET Core WebAPI using Clean Architecture

Building Clean Architecture Application using ASP.NET Core Web API and Angular 11 — Backend | by Sunil Kumar | Nov, 2020 | Medium
Sunil Kumar ・ ・ 3 min read
 sunil-kumar-60226.Medium
sunil-kumar-60226.Medium
Building an Angular 11 Application integrated with WebAPI






Top comments (0)