I haven't visited this blog for a while, I guess, errr..Life got in the way. However, I'm back and keen to get back to writing more about my software life especially in the area of Information Security/Cyber Security.
So for reasons, that escape me, I ended up thinking about Cyber Security and decided to get back into it and start learning as I knew I enjoyed it last time. What I think I find interesting is
The 'Neo, I know Kung Fu' part when I gain a little bit of knowledge.
I'm the sort of person that needs to take the information and use it, I need to follow the breadcrumbs. For example, I'm looking at Wireshark and SMB. What I need are ways to step through and see what response is captured. I can then go, ah...that makes sense.
It's a long journey and I'm hoping to find a way into the cyber security space. I guess this is why I'm blogging, to show the journey and hopefully reach the masses, so when it comes to the question of, "What have you done to improve your knowledge?", I can point to this blog and showcase what I have learnt and more importantly, what I've learnt and realised along the way.
My son also saw what I was doing and he's at the start of is IT knowledge as he's used to press an app icon and it's there. Unlike me when I was his age, I had to figure out how to configure the extended memory to get the PC games to work, I was wondering why pressing RUN STOP and the reset button made you go into the lower levels so you could look at the machine code (I think). So I ended up teaching him what I think is the basis of all this.
"How to research for the answer", it's a section on Try Hack Me, but I think it's so important and it helps him in his other studies. Once he got used to looking at the text for clues, he started answering the questions on his own. I then showed him some basic linux commands as well as trying to explain what an IP address was and how all the computers were on a network. I kept it to 10-15 minutes as I didn't want to explode his mind.
I must have done a decent job as he sent me a video saying that I was a cool dad and that the cyber security stuff seemed interesting. #majordadpoints.
I did give him the following advice
What I got up to over the weekend.
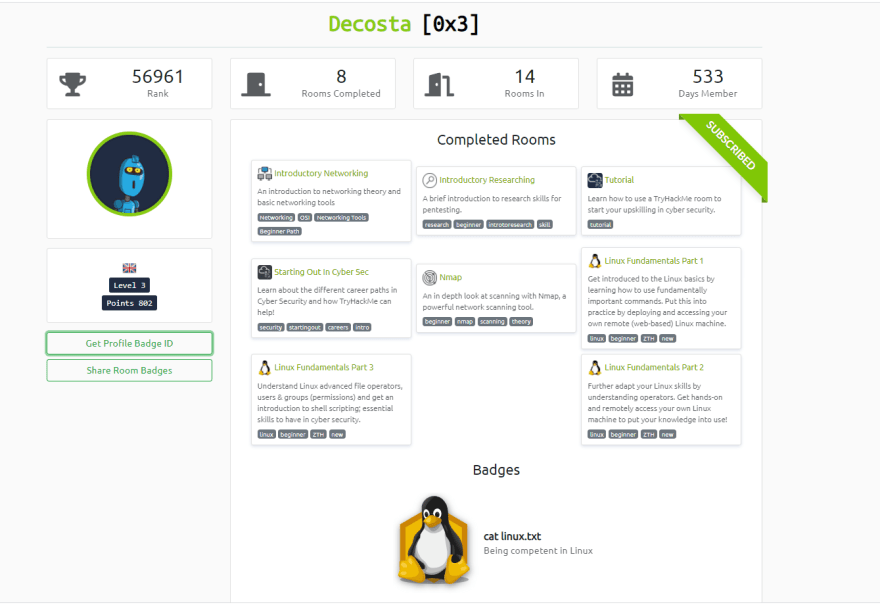
Try Hack Me Profile
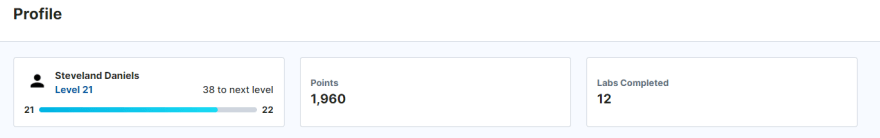
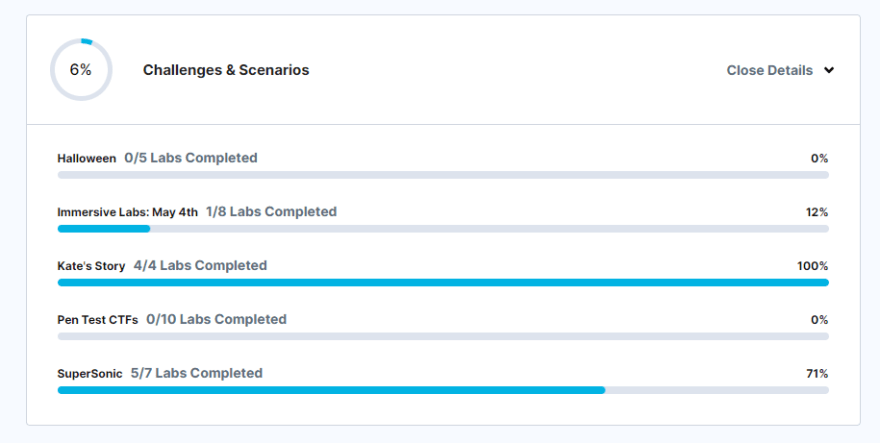
Immersive Labs Profile
There are various challenges that I attempted but didn't get anywhere with but that's part of the fun. Write down some notes to investigate later.
There was one where a countdown was occurring and my brain automatically went to, if I can stop the countdown, then it will stop. Well, what is a countdown. It's potentially a process, so let's investigate that (ps, top?). Ok, that doesn't seem to work so far. Just as I'm writing this, I'm thinking, maybe it's a cron job, so potentially, I should look into the /etc/cron section of the directory. It might not work, but the trial and error nature is interesting and doesn't demotivate me.
There was another challenge where I had to run a script and it'll return the token. So, without revealing what it is, the steps that "seem" to be on the right path was to run it normally and see what outputted. I then used file to see what type of file it was, and strings to see if there were any readable text. Once I did that, then I was able to see some sort of code (it looked like C). I then used objdump to show the assembly functions of the script. This was all done with intensive googling. Do I understand what's going on..No, but again, the fun is in finding out. What I need to do is find a way of stepping through the code to 'follow the data'.
It may seem like I'm failing on the labs on Immersive Labs but I'm finding that it strikes a nice balance. It provides you with enough information to get started, but not enough to spoon fed you the information. I like that.
The same with TryHackMe, it goes into more depth, but I do like the learning path which is why I didn't mind subscribing.
Areas I seem to find really interesting (so far, I have a long way to go).
OSINT aka 'Someone that is really good at finding out information'. - Doing the challenges made me get a nice warming fuzzy feeling on finding out snippets of information, putting it all together and answering the questions. If there is a way to continue to hone my OSINT, I'm always open to suggestions.
Networking - From reading, it's come to my attention, that the more you know about networking, the better. So again, at the start of my journey but over the weekend, I read about the OSI model, the different types of scans. Even Wireshark didn't look like a foreign language to me. I could map back the various layers back to the OSI, TCP/IP model. I could see the SYN and ACK going back and forth.
As I go through the various modules, I'll be sure to report back on my thoughts and opinions.
What I want to do again is connect with more people, listen to more podcasts (I tend to only listen to Darknet Diaries at the moment). So again, suggestions are welcome.
I wonder if BsidesCardiff is going to run again in the near future?




Top comments (0)