- Prerequisite
- The TCP/IP Model
- Understanding the TCP/IP Model
- Functions of the TCP/IP Model
- Understanding Packets
- The Journey of a Packet
- Summary
The internet works through the seamless transmission of packets. Packets are the basic unit of data exchange. This article provides an overview of the journey of a packet across the TCP/IP model. Elucidating its critical role in networking.
Prerequisite:
- Basic understanding of Computer networks
- Familiarity with the OSI model
- Basic knowledge of TCP/IP protocol suite
- Basic networking tools WireShark
The TCP/IP Model
Before we begin our journey, let us first understand what Computer Networking is. Its relevance in IT operations, Cloud services, and the internet.
Computer Networking in Today's Digital Landscape
Computer networking involves transferring and exchanging data between interconnected computing devices or nodes over physical or wireless technologies, following a set of rules known as communication protocols. Computer networking enables devices and endpoints to connect on a local area network (LAN) or larger networks like the internet or private wide area networks (WANs). This connectivity is essential for service providers, businesses, and consumers worldwide to share resources, access services, and communicate. Networking supports a wide range of activities, from telephone calls and text messaging to streaming video and the Internet of Things.
Cloud services and internet functionality enable seamless integration and communication between on-premises infrastructure and cloud platforms, facilitating data transfer, application deployment, and access to cloud-based resources. Networking provides the underlying infrastructure for cloud services such as virtual private clouds - VPCs load balancers, and content delivery networks (CDNs), ensuring reliable and scalable cloud solutions.
The Significance of Networking to End-Users
End-users should care about networking because it is essential for accessing shared resources, internet connectivity, and optimal application performance. Networking directly impacts productivity and efficiency by enabling seamless communication and collaboration. It also plays a crucial role in ensuring the security and privacy of data and protecting against unauthorized access and cyber threats. Moreover, staying informed about networking helps end-users leverage emerging technologies like cloud computing and IoT, enhancing their digital experience and personal or professional growth.
Benefits of the TCP/IP Model
Global Adoption: The TCP/IP model is the foundation of internet communication, enabling seamless connectivity among devices across different vendors and platforms, thus promoting worldwide interconnectivity in the digital realm.
Scalability and Adaptability: With its modular architecture the TCP/IP model effortlessly integrates new technologies and protocols, ensuring it can meet evolving networking needs and readily accommodate future advancements.
Cross-Platform Compatibility: The TCP/IP model facilitates smooth communication across diverse devices and platforms, allowing for data exchange between various protocols and technologies and enhancing connectivity in the digital landscape.
Standardization of the Internet: As the standard for Internet communication, the TCP/IP model guides the development and implementation of networking protocols and technologies. With a unified framework, it promotes compatibility and consistency across networks.
Understanding The TCP/IP Model
The TCP/IP model is a structure that outlines the protocols and standards governing data transmission across networks. It consists of four interlinked layers, each responsible for facilitating network communication. Named after its primary protocols, TCP guarantees dependable data delivery, while IP manages data packet routing and addressing.
| Internet Model | Description |
|---|---|
| Application | Bidirectional reliable byte stream between two applications, using application-specific semantics (HTTP, BitTorrent) |
| Transport | Guarantees correct, in-order end-to-end delivery of data |
| Network | Delivers datagram end-to-end. Best effort delivery - with no guarantees. Must use the Internet Protocol (IP) |
| Link | Delivers data over a single link between an end host and router or between routers |
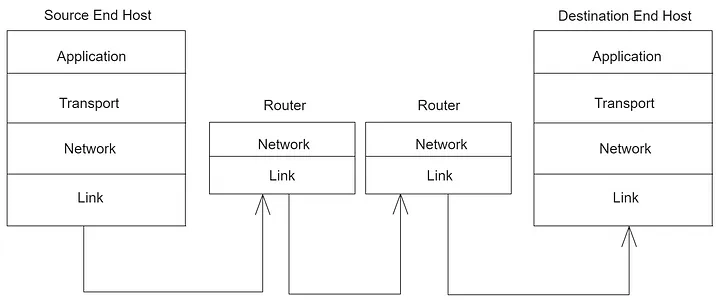
At the top of the TCP/IP model is the Application layer, with applications like BitTorrent and WorldWideWeb, which communicate to its peer layer. When the application has data to transmit, it sends it to the transport layer, whose job is to deliver the data reliably or otherwise to the destination. The transport layer then forwards this data to the network layer responsible for segmenting the data into packets, each tagged with the correct destination and address. Subsequently, the link layer receives the packet, which ensures its delivery from one node to the next along its path. The data progresses hop by hop through routers until it reaches the destination. All four layers facilitate reliable communication between applications in the end hosts. Each layer has a different responsibility, with higher layers building upon those beneath them, culminating in a bidirectional, reliable byte stream communication between applications.
The Link Layer
The link layer is the foundation of the TCP/IP protocol model, functioning as the interface between the network hardware and the rest of the network stack. Its primary role is to facilitate the transmission and reception of data across the physical network, providing a means for devices to communicate within the local area network (LAN).
The key responsibilities of the link layer include managing communication with the network adapter, coordinating data transmission according to the appropriate access method (Ethernet, token ring), formatting data into frames for transmission, handling errors in incoming frames, and acknowledging receipt of data frames while ensuring reliable delivery. Additionally, the link layer assigns addresses to network interface devices, which allows communication with devices on other networks.
The Network Layer
The network layer's primary function is to ensure the end-to-end delivery of packets across the internet - from the source and reaching the destination. Packets serve as a fundamental component in the network. They denote data accompanied by a header, its content, destination, and origin.
Network layer packets are called datagrams. They include the data and a header containing the - to and from - addresses. The network layer hands the datagram to the link layer, telling it to send it to the first link. The link layer says if you give me a datagram to send, I will transmit it over one link for you.
At the other end of the link is a router. The link layer of the router accepts the datagram from the link and hands it up to the network layer inside the router. The network layer on the router examines the destination address of the datagram. It then routes the datagram, one hop at a time, to its eventual destination. And it does this by sending it to the link layer again. To carry it over to the next link, which is passed to the network layer on the next router and so on, until it reaches the network layer of its destination.
The network layer does not need to concern itself with how the link layer sends the datagram over each link. This separation of concerns between the network and link layers allows each to focus on its job without worrying about how the other layer works. It also means that a single network layer has a common way of talking to many link layers by simply handling the datagrams to send. The modularity of each layer makes this separation of concerns possible, coupled with a well-defined API to the layer below.
When we send packets to the internet, we must use the internet protocol (IP). It is the IP that holds the internet together. The IP strives to deliver datagrams to their intended destinations. But it does not guarantee successful delivery. Datagrams can be lost, delivered out of sequence, or not delivered. Despite these potential issues, the internet can still function effectively. Applications often require another protocol layered on the IP to ensure reliable data delivery. This protocol operates at the transport layer and its responsibility is managing end-to-end communication between applications.
The Transport Layer
The Transmission Control Protocol — TCP — is the most common Transport layer. The TCP’s job is to guarantee that the data sent by an application at one end of the internet is delivered correctly to the application at the other end. If the network layer drops some datagrams, the TCP will transmit them multiple times if needed. If the network layer delivers them out of order — perhaps if two packets follow a different path to their destination. TCP will put the data back into the correct order again.
TCP provides applications with a service that ensures that data is delivered correctly and in the intended order - despite the unreliable nature of the underlying network layer's datagram delivery service. This means that TCP guarantees the correct sequencing and delivery of data packets, addressing issues like packet loss, out-of-order delivery, and duplication. Applications like web and email clients greatly benefit from TCP's reliability because it allows them to focus on their core functionalities without complex internal error-handling mechanisms. By relying on TCP, these applications can delegate the responsibility of reliable data transfer, thus abstracting away the complexities of network communication and ensuring seamless and dependable data transmission.
However, not every service requires a reliable delivery of data packets. Consider a scenario of a video snippet transmission via packets during a WhatsApp call. If there is a network latency, multiple re-transmissions of packets may not be essential. Opting to forego re-transmission could be the optimal choice. UDP: User Datagram Protocol can be used for applications that do not need a reliable delivery service.
The Application Layer
The application layer is at the top of the TCP/IP model, and it defines TCP/IP application protocols and facilitates the interface between host programs and Transport layer services for network usage. The Application layer includes several high-level services such as DNS (Domain Naming System), HTTP (Hypertext Transfer Protocol), Telnet, SSH, etc.
Every application interacts with the transport layer through a well-defined API, originating from the application layer to access the underlying TCP or UDP service. Applications mostly want a bidirectional reliable byte stream between endpoints, using their protocols to define the syntax of data exchange.
For example, when a web client sends a GET request to a web server, it sends the request as an ASCII string along with the URL. From the application layer's viewpoint, the request is sent straight to its peer at the receiving end (the web server application) without knowing the underlying transmission configurations. The application layer delegates the GET request to the TCP layer for accurate delivery, which in turn utilizes the services of the network layer and relies on the link layer for transmission.
Functions of the TCP/IP Model
Logical Addressing:
TCP/IP implements logical addressing to accommodate numerous hosts across diverse networks. IP manages this mechanism, ensuring data packets reach the appropriate networks and nodes.IP Manages Routing:
Handling the critical task of routing data packets, IP determines the next node along the transmission path from source to destination. This ensures that data packets reach their intended destinations, even if the sender is unaware of the specific location.TCP Ensures Error and Flow Control:
Establishing a virtual connection between senders and receivers, TCP maintains continuous communication and incorporates error and flow control mechanisms. Enabling reliable data transfer and ensures connection stability throughout the transmission process.TCP Supports Applications:
TCP assigns unique TCP and UDP ports to applications, which allows for the seamless differentiation of specific applications and their communication link.
Understanding Packets
A packet consists of the data intended for delivery and a header containing information about its destination and origin within the network. When a user requests to load an image, the image file is not transmitted from the web server to the user's computer as a single entity. Instead, the image is broken into bits of packets, transmitted across the internet via cables, and then reassembled by the user's computer to reconstruct the original image.
The efficiency, reliability, scalability, and flexibility make packets vital in internet communication. Breaking data into smaller packets or sizes optimizes network resources, while error detection and correction mechanisms enhance reliability. The internet employs packet switching. Packet switching divides data into smaller packets for efficient transmission between computers. This approach enhances network performance by allowing multiple connections in parallel over the same wires and enabling networking equipment to process packets independently. Packet switching also enhances network resilience and efficiency by permitting packets to take various paths to their destination, encouraging data exchange among billions of devices.
What is in a packet header?
Examining the IPv4 packet header, we can see what travels with a packet to its destination.
- Bit 0: Typically refers to the first bit in a bit sequence. In networking, the order in bits transfer can depend on the network protocol used. For instance, Ethernet and IP do not specifically define the order in which individual bits travel on the wire, but rather the order of bytes and fields.
- IPv4 Header: Contains several critical fields for routing and handling packets. The most important fields include:
- Destination IP Address: Indicates the packet's intended recipient.
- Source IP Address: Indicates the packet's origin.
- Protocol ID: Specifies the higher-level protocol used in the data field (e.g., TCP, UDP). This field helps the destination host demultiplex arriving data, routing it to the appropriate protocol handler. For example, a Protocol ID value of 6 indicates that the data contains a TCP segment and is thus passed to the TCP processing module.
The Internet Assigned Numbers Authority (IANA) defines over 140 different protocol numbers representing various transport and network layer protocols.
Version: This 4-bit field specifies the IP version in use. The values are 4 for IPv4 and 6 for IPv6. The header described here is for IPv4.
Total Length: This 16-bit field specifies the entire packet size - including the header and data in bytes. The maximum size is 65,535 bytes (64 KB).
Time to Live (TTL): This 8-bit field prevents packets from circulating indefinitely. Each router that forwards the packet decrements the TTL by 1. TTL discards the packet when it reaches zero. This mechanism ensures packets do not loop forever.
Packet Identification: This 16-bit field identifies the fragments of an original IP packet.
-
Flags: This 3-bit field controls and identifies fragments. The most significant bit is reserved. The remaining two bits are:
- DF (Don't Fragment): The packet cannot be fragmented.
- MF (More Fragments): Indicates more fragments. If not set, it indicates the last fragment.
Fragment Offset: This 13-bit field specifies the position of fragments in the original packet, measured in 8-byte blocks.
Type of Service (ToS): This field indicates the quality of service desired for the packet. Routers can use the ToS to prioritize packets.
Header Length: This 4-bit field indicates the length of the IP header in 32-bit words. The minimum value is 5 (20 bytes), and the maximum is 15 (60 bytes), accommodating optional fields.
Header Checksum: This 16-bit field checks the header's integrity. It ensures the header is uncorrupted in transit. The header rejects the packet if the checksum does not match the calculated value.
Common Types of Network Packets
| Packet Type | Purpose | Example | Function |
|---|---|---|---|
| Data Packets | Transport user data or application-specific information | Segments of emails or file downloads | Encapsulate user data and ensure delivery from source to destination |
| Control Packets | Manage and control network communications | TCP control packets like SYN, SYN-ACK, and ACK | Facilitate establishment, maintenance, and termination of network sessions |
| Routing Packets | Inform routers about network topology changes and determine the best path | OSPF and BGP packets | Maintain and update routing tables to ensure data takes the most efficient path |
| Fragmentation Packets | Divide large data packets into smaller fragments to accommodate MTU | IP fragmentation packets | Allows the transmission of large packets over networks with smaller MTU sizes |
| Acknowledgement Packets | Confirm successful receipt of data packets | TCP ACK packets | Provide feedback to the sender upon receiving data correctly, ensuring reliable transmission |
| Broadcast Packets | Simultaneously send data to all nodes in a local network segment | ARP requests | Enable network-wide communication for tasks like address resolution and network discovery |
The Journey of a Packet
The TCP/IP Model picks up a stream of data from the application layer, and the transport layer breaks the stream into a segment of data that it reliably delivers to an application running on another computer. The transport layer sends these segments as network layer packets - which the network layer delivers to other computers.
application [streams of data] -> transport [breaks the stream of data into segments] -> network [sends network layer packets to other computers].
Almost all web traffic is over TCP. Its typical operation is between a client and a server. To open a connection a client sends a connection request, which the server responds to. This exchange takes three messages, called the three-way handshake.
The first step of the message is when the client sends a Synchronize message to the server, often called the SYN.
The second step is when the server responds with a synchronized message. Acknowledging the client Synchronize or a Synchronize / Acknowledge message - called a SYN/ACK.
The third and final step is when the client responds by acknowledging the server Synchronize, called an ACK.
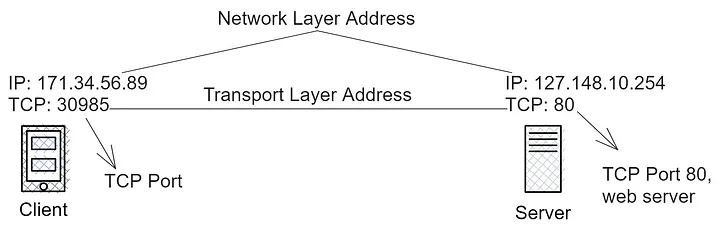
From the network layer point of view, packets sent to different applications on the same computer look the same. Hence, we need two addresses to open a TCP stream to another program.
- The first is the IP address: the address of the network layer.
- The second is a TCP port: this tells the computer software which application to deliver.
Web servers usually run on TCP Port 80. So when we open a connection to a web server, we send IP packets to the computer's IP address. Those IP packets have TCP segments whose destination port is 80.
But how does an IP Packet get to its destination
Given that a direct physical link between a client (say, A) and a server may not exist. Client A often connects to an intermediary, typically a router. This router, in turn, establishes connections with other routers in the network. The journey of IP packets from client A to the server involves multiple stages, known as hops, where each hop represents a connection between two routers. If client A accesses the network via Wi-Fi, the hop involves wireless communication to reach the network access point. Conversely, if client A employs a wired connection like Ethernet, the data transmission traverses physical cables, eliminating the need for wireless hops.
A wired connection from the access point leads to the broader internet. The router forwards client A packet along this wired hop. A router can have many links connecting to it. Upon the arrival of each packet, the router determines the appropriate outbound link for transmission. Routers possess IP addresses, which may lead to delivering a packet to its corresponding software and not forwarding it.
Inside the stream
Inside each hop
For example, IP packets are forwarded to the router IP address when you log in to a router using TCP.
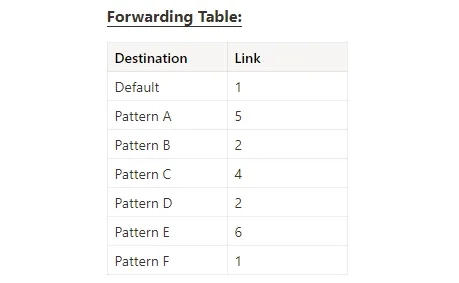
How does a router make this decision
The router achieves this through a forwarding table. It comprises IP address patterns and their associated outbound links. When a packet arrives, it assesses which entry in the forwarding table best matches its pattern and directs the packet through the link specified in that entry. Typically, the term best signifies the most specific match.
The default route is the least specific. It matches every IP address. If a packet arrives and there is nothing but the default one, the router will use the default route.
Summary
In computer networking, packets follow the TCP/IP Model. It begins at the application layer when an app wants to send data. The transport layer, with protocols like TCP and UDP, deals with splitting data, controlling the flow, and finding errors. The packet gets wrapped in an IP header that guides it across the internet at the network layer. Lastly, the link layer ensures the packet goes over the physical network. When the packet reaches its destination, it reverses the steps. It begins at the link layer, where it is received and decoded. The network layer looks at the IP header to discern where the packet should go. The transport layer checks the data for problems and puts it in order if needed. Finally, the Application layer hands the data to the receiving app. Along the way, packets are handled to ensure they go from the source to the destination.











Top comments (0)