A vulnerability assessment is a systematic/periodic review of security weaknesses in an information system. It evaluates if the system is susceptible to any known vulnerabilities, assigns severity levels to those vulnerabilities, and recommends remediation or mitigation, if and whenever needed.
It can also be defined as the process defining, identifying, classifying, and prioritizing security weaknesses/vulnerabilities in systems which includes servers, applications and network infrastructures.
It evaluates the exposure of the system to known vulnerabilities and assigns severity levels to those vulnerabilities and recommends remediation or mitigation if and whenever needed.
This can be compared to the periodic health check we as individuals carry out to ascertain the state of the various organs and systems within our body. For instance, a cancerous cell detected in its early stage can easily be dealt with compared to when a stage four cancer cell is detected. The whole essence of health checks.
The main goal of vulnerability assessment is to provide the necessary knowledge, awareness and risk background to an organization to take appropriate actions against threats to its IT enviroment.
Vulnerability assessments can help detect but not limited to the following types of threats:
- Escalation of privileges due to faulty authentication mechanisms.
- SQL injection, XSS and other code injection attacks.
- Insecure defaults – software that ships with insecure settings, such as a guessable admin passwords.
Types of Vulnerability Assessment
Beyond types, vulnerability tools can be categorized under the same heading.
- Host assessment – The assessment of critical servers, routers, endpoints which may be vulnerable to attacks if not adequately tested or not generated from a tested machine image.
- Network and wireless assessment – The assessment of policies and practices to prevent unauthorized access to private or public networks and network-accessible resources.
- Database assessment – The assessment of databases or big data can identify weak points in a database to prevent malicious attacks. We look for vulnerabilities and misconfigurations, identifying rogue databases or insecure dev/test environments.
- Application scans – The identifying of security vulnerabilities in web applications and their source code by automated scans on the front-end or static/dynamic analysis of source code.
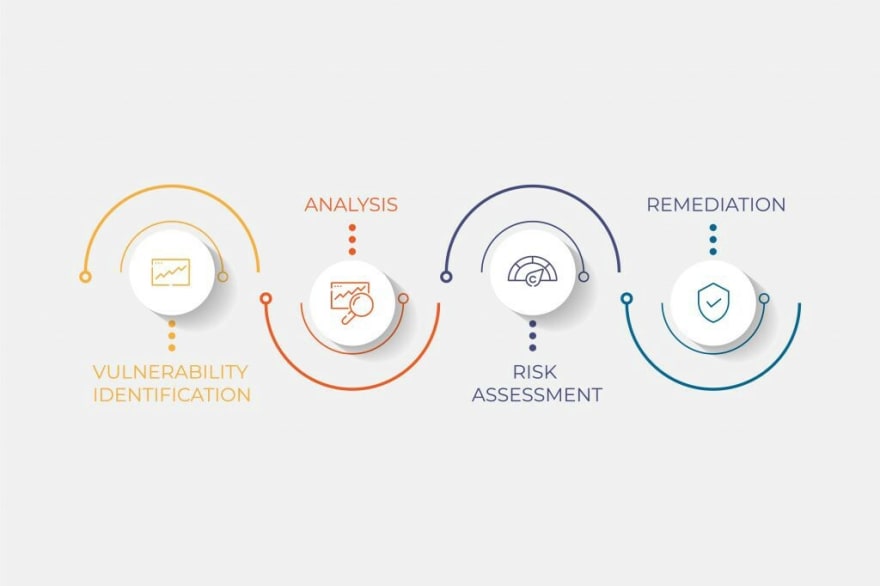
The Vulnerability Assessment Process
The following are the four steps in carrying out vulnerability assessments:
- Vulnerability Identification (Testing) The essence of this step is to make a comprehensive draft of an application’s/environment vulnerabilities/weakness as well as relating vulnerabilities to their threats. Security analysts test the security health of applications, servers or other systems by scanning them with automated tools, or testing and evaluating them manually. Analysts also rely on vulnerability databases, vendor vulnerability announcements, asset management systems and threat intelligence feeds to identify security weaknesses. A vulnerability could be as simple as an unpatched Windows server.
- Vulnerability Analysis The objective here is to identify the source and root cause of the vulnerabilities identified in step one. It involves the identification of system components responsible for each vulnerability, and the root cause of the vulnerability. For example, the root cause of a vulnerability could be an old version of an old version of an application running on a server. This provides a clear path for remediation – upgrading the application to a newer version.
- Risk assessment This step involves the prioritizing of vulnerabilities. It involves security analysts assigning a rank or severity score to each vulnerability, based on such factors as:
a. Which systems are affected.
b. What data is at risk.
c. Which business functions are at risk.
d. Ease of attack or compromise.
e. Severity of an attack.
f. Potential damage as a result of the vulnerability.
For better understanding, vulnerability found on an organization's web server would definitely have a higher severity score than the one found on an old printer not connected to the organizations network.
- Remediation This is where the closing of security gaps takes place. It’s typically a joint effort by security staff, development and operations teams, who determine the most effective path for remediation or mitigation of each vulnerability.
Specific remediation steps might include:
a. Introduction of new security procedures, measures or
tools.
b. The updating of operational or configuration changes.
c. Development and implementation of a vulnerability patch.
Vulnerability assessment cannot be a one-off activity. For it to be effective, organizations must operationalize this process and repeat it at regular intervals. It is also critical to foster cooperation between security, operation and development teams – a process known as DevSecOps.
Vulnerability Assessment Vs Penetration Testing
In the world of information security, these two are almost the same as they are meant to mitigate, prevent or reduce risk.
Unlike penetration testing, vulnerability assessment is passive, non-aggressive scanning as it does not inject malicious software into the network or system or try to bring down a server or application. On the other hand, penetration testing is active and meant to do harm or compromise a system by gaining unathorised access to an internal system. The objective of penetration testing is to test if the organization's security control can be bypassed in order to take security measures before an external party start taking advantage of the loophole.
The Vulnerability Assessment Tools
As earlier stated, vulnerability assessment tools can be categorized based on types of vulnerabilities. They are designed to automatically scan for new and existing threats that can target your application or systems. A few of the popular ones are
Nessus
Nmap
InsightVM/Nexpose
OpenVAS
Nikto2



Top comments (1)
Actually, a single malware request or critical bug can hurt business. To perform a vulnerability assessment it's helpful to use vulnerability scanners. They identify known security weaknesses and provide guidance on how to fix them. I like it because it saves time during code review and development, and reduces repetitive manual work.
What is the best web vulnerability scanner for you?