In the fast-paced realm of AWS networking and network security, staying ahead of the curve is essential to safeguarding your infrastructure. To empower you with a deeper understanding and practical insights, this blog post will take you on a captivating journey to unravel the enigmatic nature of Jump-Box EC2 instances. We will delve into their purpose, inner workings, and the diverse array of advantages they offer. Moreover, we will conscientiously explore the potential security threats and vulnerabilities associated with Jump-Box EC2 instances, equipping you with invaluable best practices to fortify your infrastructure effectively.
Introduction Jump-Box EC2
At the core of secure AWS networking lies the Jump-Box EC2 instance, also referred to as a bastion host. This specially configured EC2 instance acts as an intermediary gateway, providing a controlled and fortified access point to reach other instances within a private subnet or Virtual Private Cloud (VPC). By design, the Jump-Box EC2 instance strengthens network security by serving as a singular entry point for remote administration of other instances. Let's take a look at how it works:
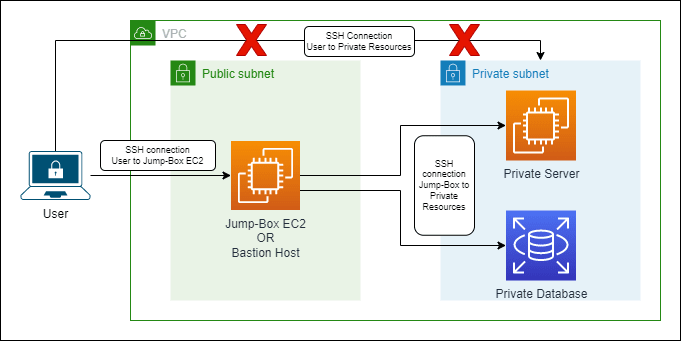
When an administrator or user seeks to access instances residing within a private subnet, they establish a secure SSH (Secure Shell) connection with the Jump-Box EC2 instance. Once connected, the Jump-Box EC2 instance acts as a secure "jumping-off" point, enabling users to securely reach other instances within the private subnet by leveraging their private IP addresses.
Leveraging the Advantages of Jump-Box EC2 Instances
The integration of Jump-Box EC2 instances brings forth numerous benefits in terms of network security and administrative efficiency:
1. Simplified Network Segmentation: Jump-Box EC2 instances facilitate clear network segmentation by acting as a secure gateway, allowing controlled access to specific instances within private subnets. This enhances overall network organization and reduces the risk of unauthorized access.
2. Augmented Security Measures: Through the strategic limitation of direct access to instances within private subnets, Jump-Box EC2 instances act as an additional security layer, reducing the attack surface and fortifying sensitive resources.
3. Centralized Access Control: Administrators can conveniently manage and monitor access to instances within the private subnet by exclusively managing SSH access to the Jump-Box EC2 instance.
4. Streamlined Logging and Auditing: Given that all SSH connections to instances within the private subnet traverse through the Jump-Box EC2 instance, it simplifies the process of logging and auditing remote access activities, enabling comprehensive oversight.
5. Efficient Resource Management: By consolidating SSH access through the Jump-Box EC2 instance, administrators can streamline resource management, eliminating the need for individual SSH configurations on each instance.
Addressing Security Threats and Vulnerabilities
While Jump-Box EC2 instances offer significant security advantages, it is crucial to proactively address the potential threats and vulnerabilities they may encounter. By understanding these risks, you can implement robust security measures to safeguard your infrastructure effectively. Let's explore some common security challenges associated with Jump-Box EC2 instances and their corresponding solutions:
1. Compromised Jump-Box:
Threat: If the Jump-Box EC2 instance is compromised, attackers can gain unauthorized access to instances within the private subnet.
Solution: To prevent unauthorized access, employ the following measures:
- Apply strict security group rules to limit access to the Jump-Box instance.
- Enable multi-factor authentication (MFA) for SSH access to the Jump-Box.
- Regularly update and patch the Jump-Box instance to mitigate known vulnerabilities.
2. Brute-Force Attacks:
Threat: Attackers may attempt to crack SSH credentials used to access the Jump-Box EC2 instance.
Solution: Mitigate the risk of brute-force attacks by implementing these measures:
- Enforce strong password policies or passphrase authentication.
- Implement rate-limiting mechanisms to detect and block multiple failed login attempts.
- Utilize intrusion detection and prevention systems (IDPS) to monitor and mitigate brute-force attacks.
3. Insider Threats:
Threat: Malicious insiders with access to the Jump-Box EC2 instance may exploit their privileges to compromise other instances within the private subnet.
Solution: Safeguard against insider threats with these preventive measures:
- Implement robust access controls and privilege management, granting access only to authorized personnel.
- Regularly review and update user permissions, revoking access when necessary.
- Enable comprehensive user activity monitoring and logging for the Jump-Box instance.

4. Inadequate Configuration:
Threat: Improperly configured Jump-Box EC2 instances may expose vulnerabilities in the network.
Solution: Prevent misconfigurations by implementing these best practices:
- Apply least privilege principles and configure strict security group rules for the Jump-Box instance.
- Regularly conduct configuration audits to ensure adherence to security standards.
- Leverage automation tools and infrastructure-as-code (IaC) frameworks for consistent and secure deployment.
5. Lack of Encryption:
Threat: Insufficient encryption of data transferred between the Jump-Box EC2 instance and other instances within the private subnet.
Solution: Ensure secure communication by implementing the following measures:
- Enable SSL/TLS encryption for SSH connections to the Jump-Box instance.
- Implement encryption and decryption operations using the data encryption key (DEK) in the Jump-Box instance using KMS or other customer managed solution.
6. Failure to Update and Patch:
Threat: Neglecting regular updates and patches for the Jump-Box EC2 instance may leave it vulnerable to known security vulnerabilities.
Solution: Maintain the security of the Jump-Box instance by:
- Establishing a patch management process to regularly apply software updates and security patches.
- Utilizing automated patch management tools to streamline the patching process and ensure timely updates.
Image Credits:
- Image by macrovector on Freepik
- Image by pikisuperstar on Freepik



Top comments (0)