Did you know that cloud misconfigurations cause almost 70% of all data breaches? AWS Config offers a way to continuously monitor and assess your AWS resources. It helps you maintain compliance and enhances your security. Automation, reduced risk, and better governance are valuable benefits.
Understanding AWS Config
AWS Config gives you a detailed view of the configuration of AWS resources in your account. It solves the problem of tracking changes. It's designed to help you understand how your resources are set up, and how they've changed over time.
What is AWS Config?
AWS Config provides continuous monitoring and resource inventory. It tracks changes made to your AWS resources. It works with services like CloudWatch, CloudTrail, and Security Hub. AWS Config helps you see configurations and how they relate.
Benefits of Using AWS Config
AWS Config provides several key advantages. It helps with automated compliance checks. It also strengthens your security stance. Plus, you get simplified auditing and cost optimization.
Automated Compliance Checks
Do you have to meet regulatory rules? AWS Config lets you define rules to check if your resources comply. This makes meeting requirements much simpler. It can check configurations against standards like HIPAA or PCI DSS.
Improved Security Posture
AWS Config gives real-time detection of misconfigurations. Imagine knowing right away if a security group has the wrong settings. You can quickly fix problems before they become bigger issues.
Simplified Auditing
Auditing can be a hassle, right? AWS Config streamlines tracking changes and configurations. You can easily see who changed what and when. This makes audits far less painful.
Cost Optimization
Who doesn't want to save money? AWS Config identifies unused or over-provisioned resources. This lets you optimize your spending and avoid wasting money. You can right-size resources to actual usage.
How AWS Config Works: Deep Dive
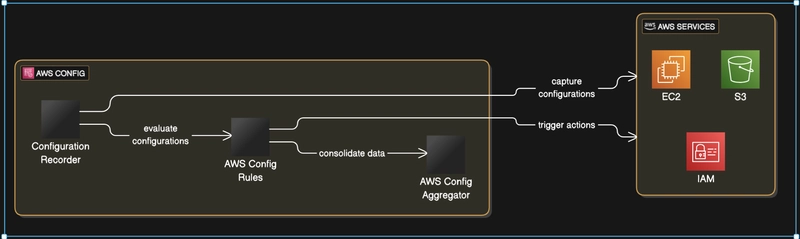
AWS Config has a few important parts. These include the configuration recorder, rules, and aggregator. They all work together. This helps you manage AWS resources.
AWS Config Architecture
Configuration Recorder
The configuration recorder does an important task: It grabs resource configurations. It tracks every snapshot and change to your resources.
Configuration Item (CI) Tracking
It tracks snapshots and changes. Think of it like taking notes on everything that happens. You always know the latest status and history.
AWS Config Rules
AWS Config Rules are really where the magic happens. They check if your resources comply. You have options for managed or custom rules.
Managed vs. Custom Rules
Managed rules are ready to use. Custom rules are created by you. Use managed for common checks. Go custom when you need something special.
Rule Evaluation Process
Rules evaluate resources for compliance. It's like a checklist that makes sure things are how you want them. Non-compliant resources get flagged for review.
Remediation Actions
Non-compliant resources get fixed. AWS Config can take action automatically. Think of it like having a robot that fixes problems.
AWS Config Aggregator
The aggregator pulls everything together. It provides a central view across accounts and regions. This simplifies managing lots of resources.
Centralized View
See all your configurations in one place. This makes it easier to monitor and manage compliance. Get a bird's-eye view of everything.
Benefits of Using the Aggregator
Enterprise-wide visibility is a huge benefit. You can spot problems quickly, no matter where they are. This gives peace of mind across your organization.
Implementing AWS Config: A Step-by-Step Guide
Setting up AWS Config takes a few steps. We will guide you on setting up AWS Config. The process will also touch on configuring it properly.
Prerequisites and Permissions
First, you need the right permissions. IAM roles and policies are important. Set them up right to access your resources.
IAM Roles and Policies
You need to grant AWS Config access. Create IAM roles with the necessary permissions. Follow AWS's security advice to keep it safe.
Setting Up Permissions
Make sure AWS Config can see your resources. Without this, it cannot monitor and assess them. Carefully review the permissions before enabling.
Enabling AWS Config
You can use the AWS Management Console or CLI. Pick the way you like to work. Set up the configuration recorder and resource types.
AWS Management Console or CLI Setup
The AWS Management Console gives a graphical interface. The CLI lets you use commands. Pick the method you know best.
Configuring the Configuration Recorder
Tell AWS Config which resources to watch. You can pick specific types like EC2 or S3. This decides what AWS Config monitors.
Creating and Managing Config Rules
You'll want to create config rules. These tell AWS Config what to check. You can pick ready-made rules, or build your own.
Selecting and Customizing Managed Rules
Start with AWS's managed rules. Customize them if you need. You can tweak rules to match your specific requirements.
Developing Custom Rules
Create your own rules with AWS Lambda functions. This gives you full control of what to check. You can define almost any condition.
Monitoring and Remediation
Use the AWS Config dashboard to monitor compliance. Automate fixes with AWS Systems Manager. This keeps your environment in good shape.
AWS Config Dashboard
The AWS Config dashboard provides a central place to monitor compliance. See which resources are non-compliant at a glance. Drill down for more details.
Automating Remediation Actions
AWS Systems Manager lets you automate fixes. This ensures non-compliant resources are fixed quickly. Set it and forget it for simple tasks.
Real-World Use Cases for AWS Config
AWS Config has various uses in the real world. Many organizations use it for compliance and security. It also helps with cost optimization.
Compliance with Industry Standards
Meet standards like PCI DSS and HIPAA. AWS Config checks for the right settings. This simplifies audits.
Example: Ensuring Encryption for S3 Buckets
Ensure encryption is enabled for all S3 buckets to meet PCI DSS requirements. AWS Config can automatically check and alert you to issues. This keeps data secure.
Automated Reporting
Use AWS Config to create compliance reports. Show auditors your resources meet requirements. Automated reports save you time and effort.
Security Best Practices
Catch common security issues like public EC2 instances. Enforce least privilege security group setups. This helps you keep your AWS account secure.
Detecting Publicly Accessible EC2 Instances
AWS Config can detect and remediate public EC2 instances. You can quickly isolate and secure your systems. Reduce the risk of unauthorized access.
Ensuring Least Privilege
Make sure security groups follow least privilege rules. This limits potential damage from breaches. AWS Config helps you maintain tight security.
Cost Optimization
Find and stop underutilized EC2 instances. Right-size resources based on usage. Waste less money on resources you don't need.
Identifying Underutilized EC2 Instances
AWS Config can spot idle EC2 instances. Shut them down to save money. Use the savings for other projects.
Right-Sizing Resources
Adjust resource sizes to match usage. AWS Config can suggest the right size. Avoid over-provisioning, save on costs.
Best Practices and Optimization Tips
Follow these tips to improve AWS Config. Get the most out of the tool. This makes things more efficient.
Tagging Strategy
Tag resources properly. This helps you apply rules and create reports. A good tagging policy is important.
Importance of Tagging
Tagging helps you organize your resources. Rules can target specific tags. This improves compliance and tracking.
Creating a Tagging Policy
Create a clear tagging plan. Use consistent tags across your resources. This simplifies management and reporting.
Rule Scope and Granularity
Balance the amount and complexity of rules. Optimize rule scope to reduce the amount of work. This keeps things running well.
Balancing Rule Complexity
Too many rules can slow things down. Find the sweet spot between security and performance. Regular review is key.
Optimizing Rule Scope
Target rules to specific resource subsets. Avoid checking everything all the time. Narrowing the scope makes things more efficient.
Monitoring and Alerting
Connect AWS Config to CloudWatch for alerts. Set up notifications for non-compliant resources. Know right away when something goes wrong.
Integrating with CloudWatch
CloudWatch provides real-time monitoring. Connect it to AWS Config for instant alerts. Quickly react to problems.
Setting Up Notifications
Configure notifications for non-compliant resources. Get alerts via email or chat. The faster you know, the faster you can fix.
Conclusion
AWS Config is a powerful tool for automating cloud compliance and security. Continuous monitoring helps you stay compliant. Implement AWS Config to explore its capabilities.
In our next article, we will be seeing how to deploy a custom comformance pack using terraform and automating the process. Stay tuned
Happy Coding✌️
Ref:
What is AWS config
Credits to aws for the cover page image i used


Top comments (0)