Attempt for Secret Communication is nothing new. Ever since we started to communicate with each other, we wanted to hide the details of our conversations from prying eyes and ears. Over the years, people have been working on this leading to the invention of “Encryption” as a result. But, encryption has a problem. Even if the encryption can hide the content of the conversation, it cannot hide the fact that a secret conversation is present. For that, we need something uncannier than encryption: which is called the Covert Channels.
To understand this in a practical way, let’s have a look at a popular dilemma called The Prisoners’ Problem.
The Prisoners’ Problem
Two prisoners locked in two near-by cells are planning their escape. They are allowed to talk with each other, but there’s a jailer who can hear their conversation. Talking with each other is the only way of communication between the two of them, but they need to be careful. If the jailer senses that they are planning for something, he might move them to distant cells, which will jeopardize their escape plan. How can the prisoners plan their escape without making the jailer suspicious?
Encryption vs Covert Channels
Let’s say that the prisoners decided to transform their conversation using a secret code, which the jailer is unaware of. This is called “Encryption” in general. In this case, only the two prisoners can translate the transformed messages back to the original because only those two know the secret code used to transform the messages. But, even though the jailer cannot understand the conversation, the inability to understand the conversation could easily make him suspicious. Therefore, Encryption is not the solution to the prisoners’ problem.
Finding a solution to the prisoners’ problem introduces a new way of secret communication called Covert Channels. The goal of a covert channel is to provide communication between two parties in an unusual way so that an intermediate party can hardly notice that there’s such communication.
For example, a covert channel between the two prisoners could be that the number of words in a sentence serves as the actual information to be passed.
e.g: The prisoners can successfully pass the message “ 345 ” by using 3 irrelevant sentences as follows.
“Are you okay? I feel like sleeping. The food was not good.”
- Are you okay? => 3
- I feel like sleeping => 4
- The food was not good=> 5
This is a primitive example of a covert channel. But the most important fact is, both entities in the covert channel should understand how it works in order to successfully pass messages.
Covert Channels are not efficient in terms of throughput. But they are quite good at hiding their presence, hence providing security by obscurity. If a covert channel is detected, it’s very likely to be entirely compromised unless the content is further protected by encryption.
Covert Channels are established over the network by using networking protocols in unexpected ways. In this article, I’ll be talking about, Network-based covert channels and how they work, practical examples and identifying and blocking covert channels.
Encryption vs Steganography? If you have heard about Steganography, you might find it very similar to the concept of Covert Channels. However, Steganography does not misuse any network protocols to transport secret data. Instead, it conceals secret data inside another payload such as an image/video.
Abusing Network Protocols
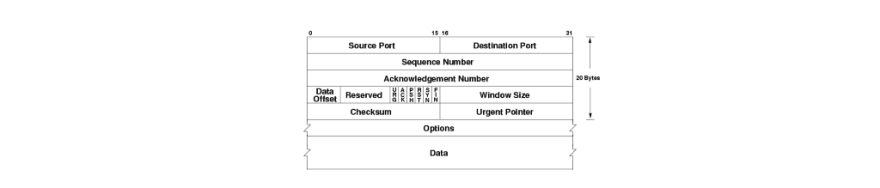
A network protocol is basically a contract between a sender and a receiver, where the sender sends structured information in a format that can be interpreted by the receiver. This ‘structure’ of the information is defined as the ‘network packet’ structure. A packet mainly consists of 3 parts which are called the header , data, and an optional trailer. Firewalls and Intrusion Detection Systems (IDS) are particularly interested in the data section of a packet as it carries the actual payload of the transmission.
Network protocols were implemented in the early days where security was not a major concern, but ‘reliable communication’ was a concern. Therefore, passing information secretly by misusing header fields was certainly possible without triggering firewall or IDS rules, hence giving birth to covert channels.
Transmitting information in the header fields is not the only way for setting up covert channels. There are two main kinds of covert channels based on how data transmission is done.
Storage Channels — Storage Covert channels encode covert data in the packets themselves (encoded in headers as I mentioned before)
Timing (temporal) Channels —Delay between the packets is used to transmit data.
Timing channels are not as reliable as storage channels and are mostly research-oriented. Therefore, during the rest of the article, we’ll be discussing storage covert channels.
Storage Covert Channels
Single Protocol Covert Channels
A single protocol covert channel is the most common type of covert channel which is established using only one protocol for covert communication. This type of covert channel usually encapsulates covert data into a protocol header. A popular example of this type is a tool called ptunnel.
ptunnel lets you tunnel TCP connections using ICMP Echo Request and ICMP Echo Reply packets reliably. We’ll see an example of a covert channel using ptunnel at the end of this article.
Protocol Channels
As its name implies, a Protocol Channel is a type of covert channel which is established over two or more protocols. An example would be a covert channel that uses ICMP and HTTP packets interchangeably to transmit data. This type of covert channel is more obscure compared to single protocol covert channels and makes it difficult.
Protocol Switching Covert Channels (PSCC)
PSCC also uses more than one protocol but unlike Protocol Channels, data is not encoded in the packets. Instead, in a PSCC, a packet itself should be interpreted as a message. Consider the following example.
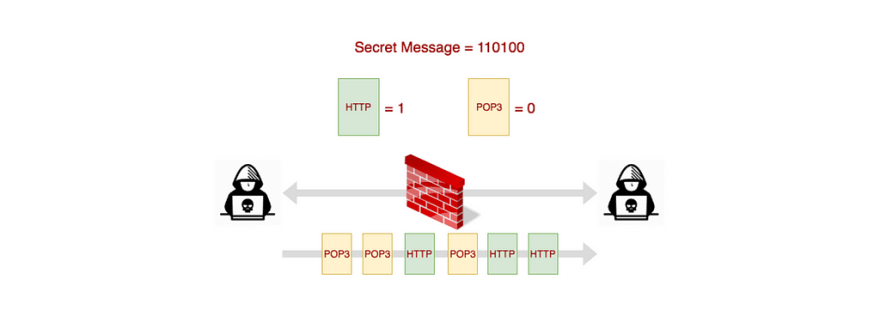
In the above example, an HTTP packet is binary 1 and a POP3 message is binary 0. Therefore, to transmit the message 110100, the sender has to send the sequence of packets as HTTP, HTTP, POP3, HTTP, POP3, POP3. The bandwidth of a PSCC can be improved by using more than two protocols and assigning a larger binary value for each protocol.
e.g: Using 4 protocols and each protocol is assigned values subsequently 00, 01, 10, 11.
Protocol Switching Covert Channels are not efficient in terms of throughput compared to Protocol Channels. But for small messages, they are much more stealthy.
Use Cases of Protocol Channels
Enterprise Data Exfiltration — The most popular use case of covert channels is to exfiltrate confidential data out of a protected network.
Bypassing Firewalls to access forbidden content — Covert Channels can also be used to access forbidden content otherwise forbidden by a firewall. An example is tunneling TCP traffic over ICMP using a ptunnel proxy as described at the end of this article.
Botnet Communications, Remote Backdoors, and Reverse Shells — Some Botnets use protocol channels in order to stealthily communicate with their command and control (C&C) centers. Also, remote backdoors or reverse shells can also use covert channels to download additional malicious scripts without detection.
Implementation Concerns
Although Covert Channels are a great way for obscure communication, setting up a reliable covert channel is not easy. The following are the key problems that have to be catered when implementing a covert channel.
Throughput vs Stealth
- Encoding more data into packets could increase the risk of the channel being exposed because the packets contain a significantly high amount of data.
- The number of packets sent at a time has to be increased if less amount of data was encoded into a single packet, leading to the channel being discovered due to the unusual network activity.
Catering packet loss and out-of-order delivery
Covert channels do not use network protocols as is, but rather misuse them. Hence, they do not have the luxury of using network protocols’ reliability mechanisms such as TCP re-transmission, re-assembly, etc. Therefore, the implementation of the covert channel should define its own protocol which implements these reliability mechanisms so that it can withstand the packet loss and the out-of-order delivery of packets.
Setting up an ICMP-based Covert Channel with ptunnel
In this example, we’ll see how to access an unauthorized web resource through a firewall with the help of a covert channel. For this, we use a tool called ‘ptunnel’ (i.e, Ping Tunnel) which provides the facility to tunnel a TCP connection over ICMP Echo Requests/Replies.
Let’s imagine the following hypothetical scenario.
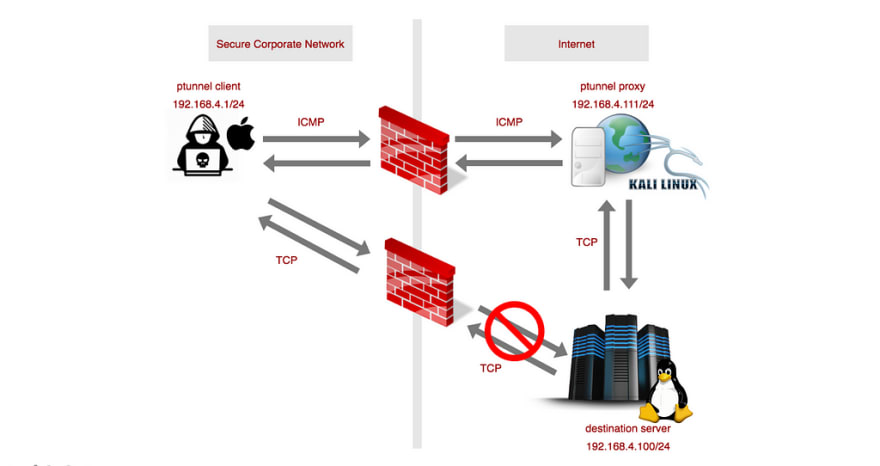
- We are located in a secure corporate network and we need to access a particular webpage that is blocked by the company’s firewall.
- But we identify that we can successfully ping through the firewall, which indicates that ICMP Requests and ICMP Replies are not blocked by the firewall.
- Then, we set up a ptunnel proxy outside the firewall. ptunnel proxy will establish a TCP connection with the destination server and will tunnel our HTTP requests to the webserver and server response back to us via ICMP.
Our setup is as follows:
- Our local machine. Runs the ptunnel client (macOS — 192.168.4.1/24)
- ptunnel proxy (Kali linux — 192.168.4.111/24)
- Destination webserver (Metasploitable Ubuntu— 192.168.4.100/24)
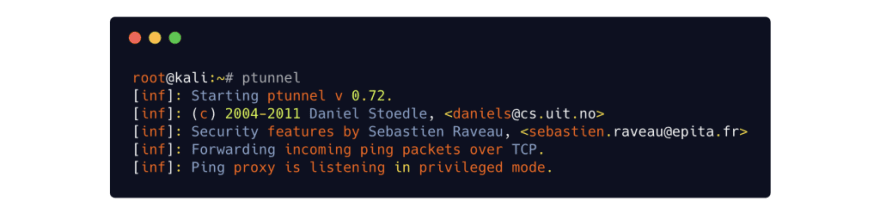
Setting up ptunnel proxy
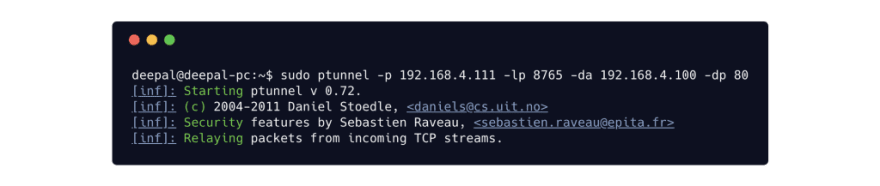
Starting up the ptunnel proxy is as trivial as running the ptunnel command.
Setting up ptunnel client
We then start up the ptunnel client on our local machine (located inside the protected network). Ptunnel client will start listing on a local port (-lp)for TCP connections which it will tunnel to the destination address (-da) and port (-dp) via the proxy (-p).
Accessing the remote resource
Once the server and the client are up and running, we can now access the restricted resource via the local TCP port as follows.

If we intercept the communication between the ptunnel client and the proxy, we could see how HTTP response secretly encoded inside the ICMP replies as indicated below.


Obviously, using a ptunnel covert channel to create a covert channel is not bandwidth efficient (150 kb/s download and about 50 kb/s upload as per the author). However, it can still come in handy for an attacker in order to secretly download a malicious script or exfiltrate secret data outside a secure network.
Identifying and Blocking Covert Channels
Covert Channels can be used with good intent, as well as malicious intent. Therefore, identifying and blocking them is also equally important. Though it is very hard to identify and 100% block covert channels, there are certain ways to make it difficult to set up covert channels.
IDS Packet Signatures — Configuring Intrusion Detection Systems with rules to identify the packet signatures of the common types of covert channels.
Traffic Anomaly Detection — Mostly research-oriented. For example, analyzing packet size variation, header size variation and bandwidth usage vs time of the day can lead to discovering unusual network activities.
Active Warden (Wendzel, Steffen & Keller, Jörg. (2012). Design and Implementation of an Active Warden Addressing Protocol Switching Covert Channels) — A firewall-like service which randomly delays packets if protocol switching is detected, making it hard to establish reliable covert communication. This is useful to prevent protocol switching covert channels.
Packet Data Padding — Intercepting and padding packet header fields that are likely to be used for covert communication.
Still, though, it’s difficult to 100% prevent covert channels without disrupting the legitimate traffic. There’s so much research work done in this area and new types of covert channels and protection mechanisms are invented from time to time.
PS: The content of this article was originally presented by me at the Colombo Secure Programming Meetup.
References:
- Wendzel, Steffen & Keller, Jörg. (2012). Design and Implementation of an Active Warden Addressing Protocol Switching Covert Channels.





Oldest comments (0)