Basic Pentesting
It has been a minute since my first CTF, Mr Robot, so I wanted to ease back into it with TryHackMe's Basic Pentesting CTF.
The goal of this VM is to remotely attack the VM and gain elevated privileges and we will track our progress by answering the questions from TryHackMe.
Configuration
I'll be using a Kali Linux VM attack the VM in this CTF through the OpenVPN connection configured to connect our Kali machine to TryHackMe.
Let's start hacking!
After configuring our connection and deploying our machine, well need to...
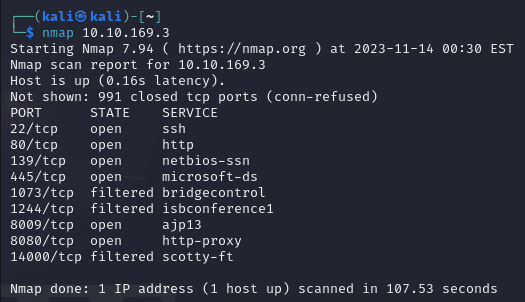
Find the services exposed by the machine: This is the initial reconnaissance to see what we can get started with. Using nmap, we'll check for any open ports or services. Let's run the following command: nmap <MACHINE IP>
Looks like there are a number of services running, but the ones we should keep an eye out for are ssh, http, netbios-ssn, and microsoft-ds.
What is the name of the hidden directory on the web server(enter name without /)? There are a few tools we can use to find the hidden directory (gobuster, ffuf, dirb). In this box, I decided to use ffuf and run the following command: ffuf -w /usr/share/wordlists/dirb/common.txt -u http://<MACHINE IP>/FUZZ -c
There are a plethora of wordlists, but I am using common.txt because it contains names of common URL directories/paths and fits our needs at the moment. Note, that regardless of the tool, using the right wordlist is key to a quick enumeration.
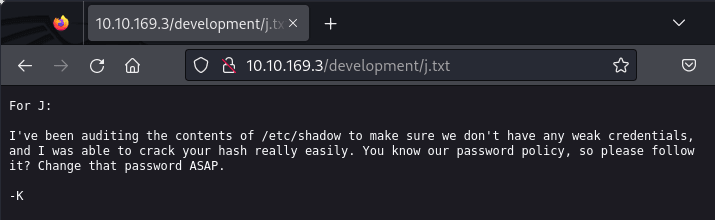
We see there is a hidden directory: /development. When we open the directory in our browser, we see 2 files:
The dev.txt appear to be message logs between "K" and "J". It's noted that Apache is being used and SMB has been configured. A possible vector here, but let's evaluate the other file before we jump in.
The j.txt appears to be memo from "K", warning "J" that their hash was very easy to crack. With that in mind, if we find "J's" full username, we can probably crack their password without too much resistance.
User brute-forcing to find the username & password. Remember earlier how we noted SMB was configured? We have just the tool that interacts with the SMB protocol, enum4linux. It will be used to enumerate any potential users on the target system. Let's run the following command: enum4linux -a 10.10.169.3 | tee enum4linux.log
What is the username? We can correlate the results of the enumeration to conlude that jan is the username.
Referencing back to our previous clue that "J" has weak credentials, we'll use their username to brute force a password.
What is the password? We'll use hydra to brute force the password by running the following command: hydra -l jan -P Desktop/wordlists/rockyou.txt ssh://<MACHINE_IP> -I
After the hydra completes it execution, we our credentials:
- username:
jan - password:
armando
What service do you use to access the server? We'll be using SSH to login with jan's credentials: ssh jan@<MACHINE_IP>
After logging in, we kind of poke around a bit. We see that shadow folder referenced in the chat logs...
Testing if we can use sudo to run any commands with elevated privileges...
...doesn't look like it...
Let’s check back to our other user kay to see if we can find anything in their home directory...
Oh? We see a pass.bak file that look s like a potential lead, but permissions only allow kay read and write access. Will need to get kay credentials and ssh as kay in order to access that file.
Enumerate the machine to find any vectors for privilege escalation: A way we can automate this process is by running LinPEAS (Linux Privilege Escalation Awesome Script). LinPEAS will search for possible paths to escalate privileges on the host machine.
Next step is to install LinPEAS onto our local attack machine and then upload it to our target machine using SCP with the following command: scp /path/to/linpeas/linpeas.sh jan@<MACHINE_IP>:/specific/path/on/machine
Let's verify that the file has been transferred and ensure the executable bit is enabled.
Now we run LinPEAS with this command: ./linpeas.sh | tee linlog.txt
After LinPEAS is was done executing, and with a look through the potential vector ouput, we find that we have a private key file that appears to be in the kay user directory, which we could use to login as kay!
══╣ Possible private SSH keys were found!
/home/kay/.ssh/id_rsa
There appears to be a possible vector with a private SSH key found in the /home/kay/.ssh directory. Let's try navigating to the directory...
Navigation successful, and from the listed permissions, we should be able to read the private key!
cat and extract the id_rsa private key
We'll save it to our local attack machine using nano → kay_id_rsa and setting chmod 600 (read only setting).
What is the name of the other user you found? From our earlier enumeration, we can confirm that kay is the other username.
If you have found another user, what can you do with this information? See if there are any privilege escalation vectors that might be associated with this other user, kay, which we achieved with LinPEAS in the last section.
Now, let’s try logging into kay:
Unfortunately, the private key is passphrase protected, but that shouldn't be too much trouble for our good friend, JtR (John the Ripper). JtR is a password cracking tool which we will use to crack the passphrase for our private key. First we'll need to extract the hash values from the private key with ssh2john:
This will allow us to pass the hash to John The Ripper to crack it using the wordlist rockyou.txt.
And boom, we have our private key passphrase: beeswax. Let's try logging in as kay one more time:
Let's see that what's in kay's home directory.
What is the final password you obtain? And after a quick cat, we have our final password:heresareallystrongpasswordthatfollowsthepasswordpolicy$$
Conclusion
Overall, the Basic Pentesting CTF was not too difficult, but complex enough to where it tests my baseline knowledge of what tools to use in the appropriate scenario. Another CTF under the belt and more tools for the utility belt to crack the next one. Happy hacking!👾

























Top comments (0)