1. Introduction
Amazon Web Services (AWS) and Microsoft's Azure stand as two giants in the cloud computing realm. With a wide array of services ranging from data storage to machine learning, both have carved out significant market shares. While AWS and Azure are the giants in the cloud, emerging platforms like Five are shaping how businesses build applications on these giants. So let's uncover AWS security vs Azure security and see how platforms like Five leverage them.
- 1. Introduction
- 2. The Evolution of Cloud Security
-
3. Identity and Access Management (IAM)
-
4. Virtual Network Security or VPN
-
5. Data Encryption Solutions
-
6. Monitoring and Management
-
7. Threat Detection and Management
-
8. Cryptographic Key Management
-
9. Cost Implications
- 10. Building Business Applications with AWS: The Case of Five
- 11. Conclusion
2. The Evolution of Cloud Security
A brief history of security in cloud services.
Cloud security, though a contemporary concept, has a rich history. In the developing stages of cloud computing, security was often an afterthought, largely due to the novelty of the platform and the lack of awareness about potential threats. However, as cloud adoption surged, so did the variety and sophistication of cyber-attacks. This evolution compelled providers to re-think and revamp their security protocols, transitioning from basic firewalls to intricate, multi-layered security strategies.
Challenges that online businesses face today.
The digital age, while bringing numerous advantages, has also unveiled a set of challenges for online enterprises. The rise of cybercrime, including data breaches, ransomware attacks, and phishing scams, continually test the resilience of cloud security measures. Additionally, regulatory pressures, like GDPR and CCPA, add another layer of complexity as businesses grapple with ensuring compliance. As cloud platforms become more intricate and multi-faceted, securing them demands a holistic approach, one that AWS and Azure both strive to perfect. Amidst these challenges, platforms like Five are leveraging the advancements in AWS's security to provide a safer environment for application development.
3. Identity and Access Management (IAM)
Winner = AWS
a. AWS Identity and Access Management
Overview and primary features.
AWS Identity and Access Management (IAM) allows users to control access to resources in AWS securely. It offers a blend of services, including role-based access control, user and group management, and identity federation. By facilitating granular permissions, AWS IAM ensures that users have only the necessary access to perform their roles. Think of IAM like a security guard. It lets certain people (or systems) use specific AWS resources and keeps others out. You can group people (or systems) and decide what each group can and can't do.
The pros and cons of AWS IAM.
Pros:
- Fine-grained control.
- Integrates well with other AWS services.
- Supports multi-factor authentication (MFA) out of the box.
Cons:
- Can be complex for newcomers.
- Overly permissive policies might lead to security vulnerabilities if not configured correctly.
b. Azure Active Directory (AD)
Overview and primary features.
Azure Active Directory (AD) is Microsoft's cloud-based identity and access management service, which helps employees sign in and access resources. Features include multi-factor authentication, device registration, and a comprehensive suite of identity governance capabilities. Azure AD is like IAM but for Microsoft's cloud. It's the gatekeeper, deciding who gets in and who stays out.
Costs associated and comparison with AWS IAM in terms of features and cost-effectiveness.
Azure AD has various pricing tiers, each offering a different set of features. When compared with AWS IAM, certain functionalities might come at an additional cost. Here, businesses need to weigh the benefits versus the investment, especially when considering large-scale deployments.
Strictly in terms of security:
- Both AWS IAM and Azure AD support multi-factor authentication (MFA) for added security.
- Azure AD might have an edge in enterprise settings with features geared towards larger organizations, such as conditional access, identity governance, and more.
4. Virtual Network Security or VPN
Winner = AWS
a. AWS Virtual Private Cloud (VPC)
How it works and benefits.
AWS VPC lets users provision a logically isolated section of the AWS Cloud where they can launch AWS resources in a virtual network. This provides complete control over the virtual networking environment, including IP address range, subnets, and route tables.
Unique offerings, customer-centricity.
AWS VPC stands out with its flexibility. Users can customize their VPC's network configuration, which can be particularly useful for workload migrations or hybrid cloud architectures.
b. Azure Virtual Network (VNet)
Key features and benefits.
Azure VNet provides a similar isolated and highly-secure environment to run virtual machines and applications. It offers integration with Azure's wide array of services, DNS customization, and enhanced security through Network Security Groups.
Comparison with AWS VPC in terms of flexibility and customer focus.
While both services offer comprehensive virtual networking solutions, their approach varies. Azure VNet provides tighter integration with other Microsoft products, making it ideal for businesses heavily invested in the Microsoft ecosystem. AWS VPC, on the other hand, often appeals to those looking for broader customization and granular control options.
To put it simply:
AWS VPC and Azure VNet are both great tools for creating private, isolated cloud environments. AWS VPC is known for its adaptability, allowing users to tailor their virtual network, which is great for specific workloads or combined cloud structures. Azure VNet, however, emphasizes integration with other Microsoft services and offers custom DNS and enhanced security. If you're deep into the Microsoft world, Azure VNet might be a better fit, but if you want more customization, AWS VPC is the way to go.
5. Data Encryption Solutions
Winner = AWS
a. AWS Encryption Methods
- Data encryption features and services: AWS's commitment to data security is evident through its diverse encryption solutions. AWS provides tools and services to encrypt data both at rest and in transit. The platform uses robust algorithms and methodologies, such as AES-256, ensuring data remains confidential and tamper-proof.
- Introduction to AWS Key Management Service: Central to AWS's encryption strategy is the AWS Key Management Service (KMS). KMS offers a centralized control to create and manage cryptographic keys, which are then used across multiple AWS services to encrypt data.
b. Azure Blob Storage and Encryption
- Overview and main features: Azure Blob Storage provides scalable and durable storage for unstructured data. Beyond its storage capabilities, Azure offers integrated encryption functionalities, ensuring data stored within blob containers remains secure, leveraging Advanced Encryption Standard (AES) mechanisms.
- Comparison of encryption robustness between AWS and Azure: Both platforms adhere to industry standards when encrypting data. However, there are nuances in their approaches, offerings, and key management methodologies that may make one platform more suited to specific organizational needs than the other.
6. Monitoring and Management
Winner = AWS
a. AWS Monitoring Tools
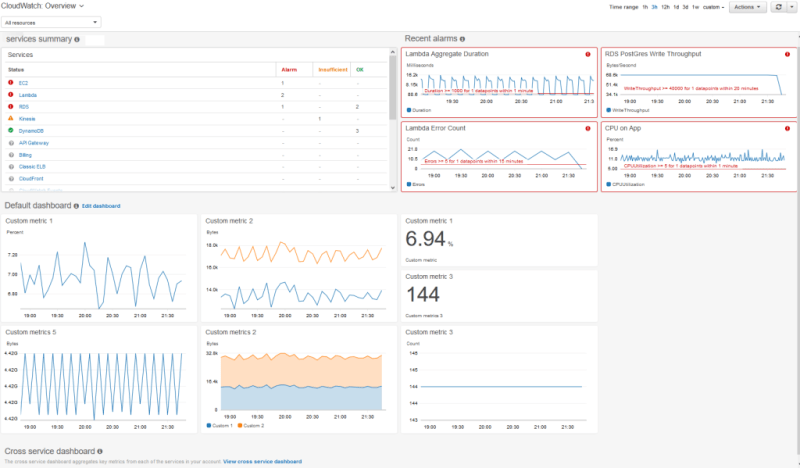
- Amazon CloudWatch: Features and benefits: Amazon CloudWatch serves as the monitoring backbone for AWS resources. It provides actionable insights into application health, system performance, and resource utilization. With its customizable dashboards and alarms, users can actively oversee their AWS ecosystem in real-time.
b. Azure Monitor
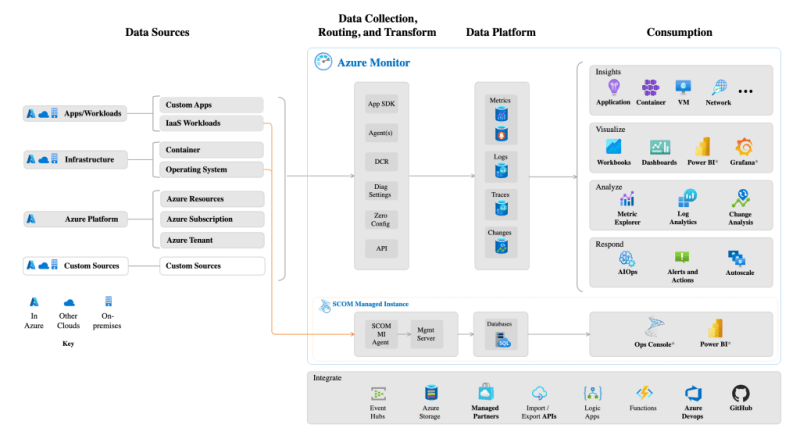
- Overview and key functionalities: Azure Monitor is a comprehensive solution in Azure's toolkit that offers deep insights into application and infrastructure health. By collecting and analyzing data from various sources, Azure Monitor provides a holistic view of the entire application and infrastructure landscape.
7. Threat Detection and Management
Winner = Azure
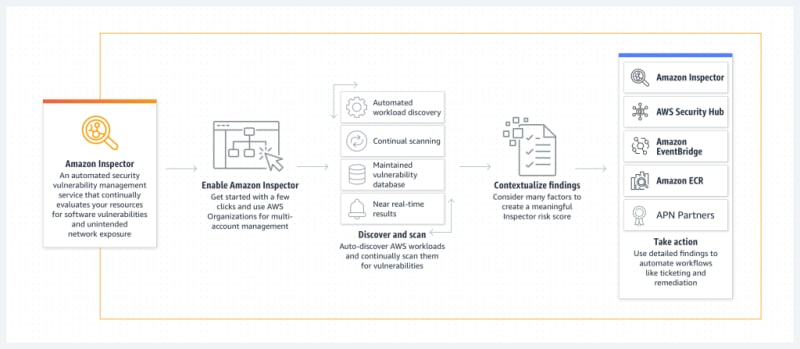
a. AWS Inspector
- Features and benefits: AWS Inspector is a vulnerability assessment service that helps improve the security and compliance of applications deployed on AWS. By analyzing application behavior, Inspector identifies potential security weaknesses, enabling businesses to address them proactively.
b. Azure Security Center
- Key features and advantages: Azure Security Center provides unified security management, granting advanced threat protection across all Azure services. With a wide array of tools, it offers advanced threat detection, network segmentation, and secure score features, ensuring optimal cloud protection.
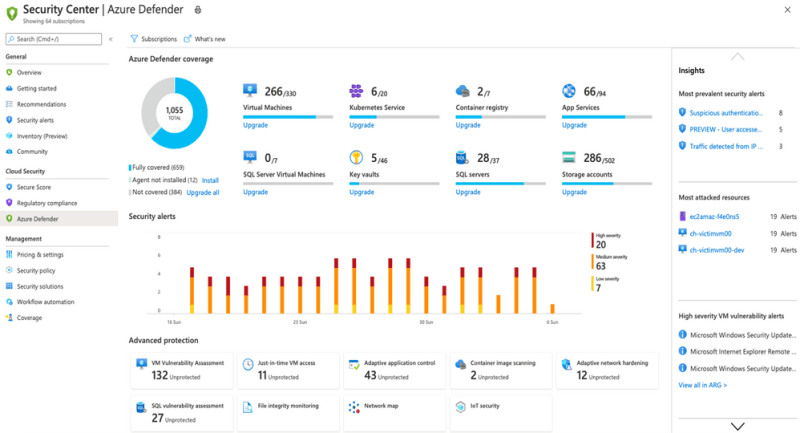
- How Azure outpaces AWS in this segment: Azure's focus on hybrid environments and its extensive integrations give it a competitive edge in certain areas of threat management.
8. Cryptographic Key Management
Winner = AWS
a. AWS Key Management Service (KMS)
In the world of cloud security, cryptographic key management remains pivotal. AWS Key Management Service (KMS) stands at the forefront of this arena. Designed to create and manage cryptographic keys and control their use across a wide range of AWS services and applications, AWS KMS offers a centralized and user-friendly platform. It ensures robustness and the integrity of data, ensuring that the keys used to encrypt and decrypt data remain secure.
b. Azure Key Vault
Diving into the Azure ecosystem, we're greeted by the Azure Key Vault, Microsoft's response to cryptographic key management challenges. Azure Key Vault isn't just about key management; it's a multipurpose tool that handles secrets. A secret is anything that you want to tightly control access to, such as API keys, passwords, certificates, or cryptographic keys. What makes it stand out is its seamless integration with other Azure products, ensuring that sensitive data, application secrets, and keys remain under a fortified umbrella.
9. Cost Implications
Winner = Depends
In the digital era, while businesses prioritize security, the financial aspect associated with securing their data cannot be ignored. Thus, understanding the cost implications of the security features offered by major cloud providers is crucial.
Overview of AWS and Azure Pricing Models
AWS operates on a pay-as-you-go model, where users pay only for the individual services they need, for as long as they use them, without requiring long-term contracts or complex licensing. This model is beneficial for enterprises that have fluctuating needs.
Azure, on the other hand, also offers a pay-as-you-go model but couples it with short-term commitments which can lead to discounted rates. Its integration with other Microsoft products can also affect the pricing, making it more cost-effective for businesses already entrenched in the Microsoft ecosystem.
While AWS typically offers cheaper compute options, Azure frequently provides more affordable storage solutions. It's vital for potential users to utilize each cloud provider's respective pricing calculator to get an accurate estimate tailored to their specific needs.
How Security Features Impact the Overall Cost for Both Platforms
It's imperative to understand that while base services might seem economically feasible, the inclusion of advanced security features can alter the cost dynamics. For AWS, services like CloudHSM, AWS KMS, and advanced monitoring tools often carry additional charges. Similarly, in Azure, features like Azure Key Vault, advanced threat detection, and Azure Information Protection can increase the total bill.
For businesses, it's not just about understanding these costs, but also evaluating the value proposition. The cost associated with a security breach, both financially and reputation-wise, can far outweigh the preventive measures' costs.
It's also essential to consider how platforms like Five, built on AWS, bring value. With Five, businesses get the robust security of AWS but without some of the complex pricing structures tied to individual AWS security features, making it a cost-effective solution.
10. Building Business Applications with AWS: The Case of Five
In the midst of our in-depth exploration of AWS and Azure security features, it's imperative to recognise exactly how you can use these security frameworks. Enter Five, a low-code development IDE.
While its foundational promise lies in streamlining online database application creation, its integration with AWS offers businesses an enhanced security advantage. Deploying applications on AWS, a platform known for its robust security protocols, Five ensures that businesses not only have a faster way to build their internal applications but also inherit AWS's multi-faceted security infrastructure.
This is particularly beneficial for businesses that aim to build comprehensive standalone web applications without diving deep into the intricacies of full-stack development. By combining the agility of Five with the security robustness of AWS, enterprises can swiftly bring to market applications that are both functional and fortified against cyber threats. This synthesis highlights the future of application development: where ease of creation meets stringent security standards.
11. Conclusion
As we've explored the depths of AWS and Azure's security infrastructures, it's clear that new-age platforms like Five are playing a pivotal role. Leveraging the robust security frameworks of giants like AWS, Five presents a future where businesses don't have to compromise between ease of application development and stringent security.
From IAM to HSM, both AWS and Azure have made substantial strides in ensuring that their ecosystems are robustly secure. When diving deep into AWS Security vs Azure Security, it's evident that AWS stands out in its expansive range of services and deep integration capabilities, and Azure often shines with its integrations, especially for businesses already using Microsoft products.
However, the decision isn't merely about features; it's also about cost implications, scalability needs, and future business trajectories. Comparing AWS Security vs Azure Security, startups operating on a tight budget need to understand the intricacies of the pricing models and the potential long-term implications. Meanwhile, larger enterprises might prioritize feature sets, integrations, and customization capabilities.
In the end, the recommendation isn't a one-size-fits-all. Businesses need to assess their unique requirements, budget constraints, and long-term vision. But one thing remains clear - in the realm of security, both AWS and Azure are formidable contenders, ensuring that businesses, big or small, can operate in the digital space with confidence.




Top comments (0)