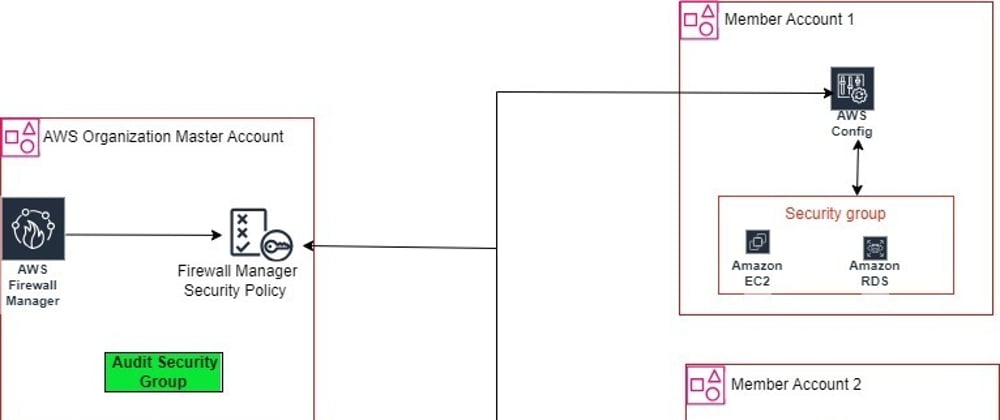
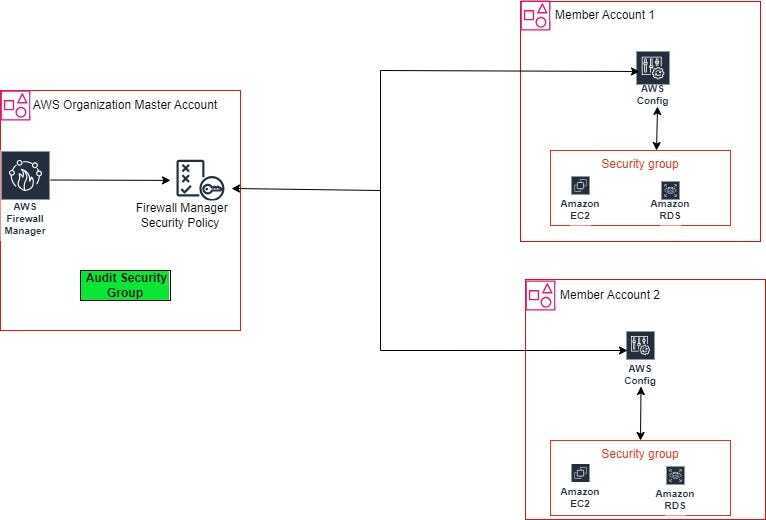
Managing security at scale in a multi-account AWS environment can be challenging. One common concern is ensuring security groups are configured according to your organization's security policies. AWS Firewall Manager simplifies this by enabling centralized management and auditing of security groups across AWS Organization accounts.
In this post, we’ll walk through the process of setting up AWS Firewall Manager to audit security groups in an AWS Organization.
❓What is AWS Firewall Manager?
AWS Firewall Manager is a security management service that makes it easier to centrally configure and manage firewall rules across your accounts and applications in AWS Organizations. You can use Firewall Manager to manage AWS WAF, AWS Shield Advanced, VPC, security groups, AWS Network Firewall, and more.
One powerful feature is Security Group policies, which allow you to audit and enforce security group rules at scale.
✍🏾 Why Audit Security Groups?
Improperly configured security groups can expose resources to unnecessary risk. Auditing ensures:
No overly permissive rules (e.g., allowing 0.0.0.0/0 for SSH or RDP)
Consistent rules across accounts and VPCs. Identification and correction of non-compliant security groups.
This Demo is specifically for auditing security groups in AWS organizations accounts.
⚗️ Pre-Requisites
- AWS Organizations Setup
i) In this Demo we are not setting up the AWS Organization and all accounts should be part of an AWS Organization.
ii) AWS Config must be enabled in all member accounts (Firewall Manager relies on AWS Config for resource visibility).
- Firewall Manager Administrator Account
i) You need to designate an administrator account for Firewall Manager in AWS Organizations. This account will manage and deploy policies across the org.
- Permissions
i) The administrator account needs the necessary IAM permissions to manage Firewall Manager policies and read AWS Config data.
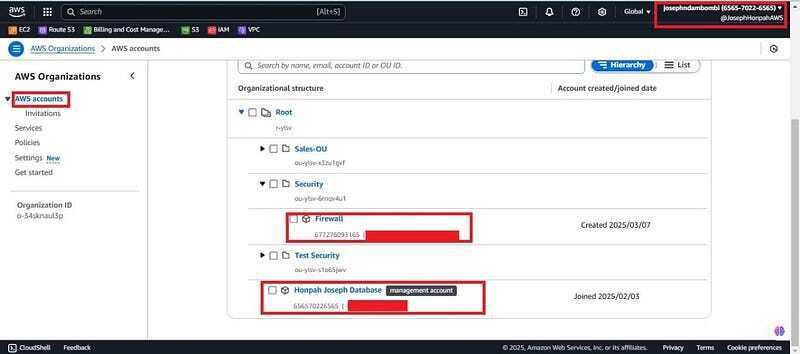
With all the above present in your good to go. I have AWS organizations setup already with management account “Josephndambombi” ending with ××××××××6565 and member account “Firewall1” ending with ××××××××3165, which was used for this Demo.
1️⃣ STEP 1: Setting up Firewall Manager from the management account of AWS Organization and resources such as SG, EC2 and AWS config from member account.
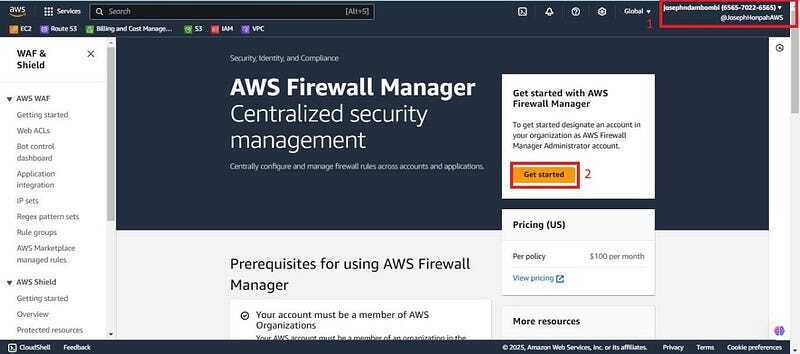
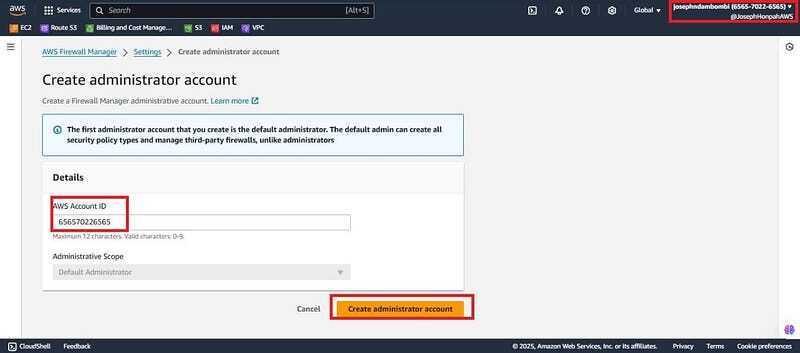
- Firstly, you need to log into the management account (Josephndambombi “accountID xxxxxxxx6565"). Navigate to the search bar of the management console and search for AWS Firewall Manager, click on get started.
- Put in the account Account ID of your management account (xxxxxxxx6565) and click on the Create administrator account.
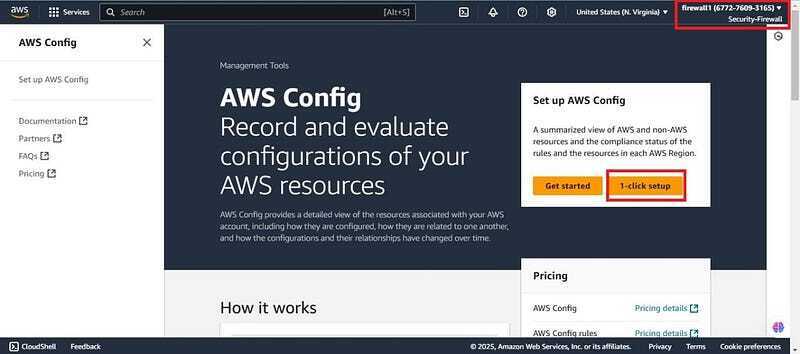
- Login to your member account (firewall1 “account ID xxxxxxxx3165") and the first prerequisite for Firewall Manager is AWS config on member accounts. Search for AWS config on the search bar and if it’s the first time enabling config click on 1-click setup. If it’s not the first time, you should click on settings and enable. Keep everything as default, click on create a bucket and create.
CREATING SECURITY GROUP
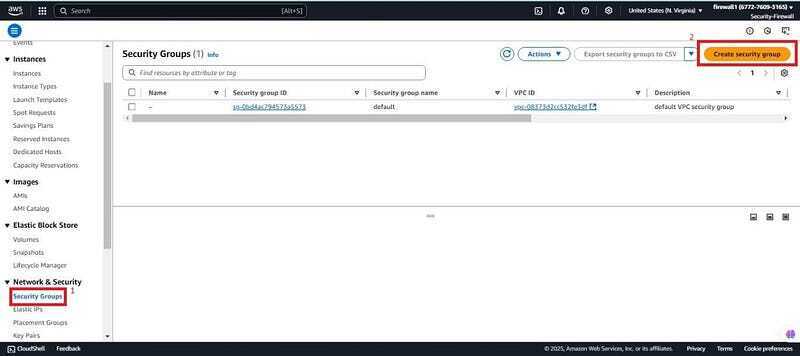
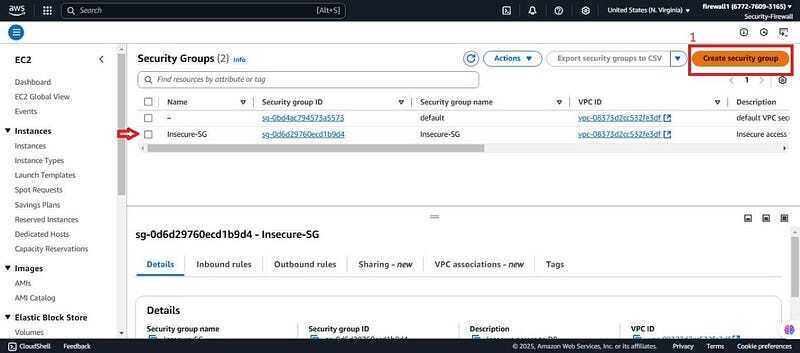
- Once the AWS config is created, we will be needing two SGs. One which will act as the insecure SG for firewall manage to detect as non-complaint and one which will be secure to test if the firewall manager will detect complaint SG. Navigate to the EC2 console. Scroll down, click on the security group and create a security group.
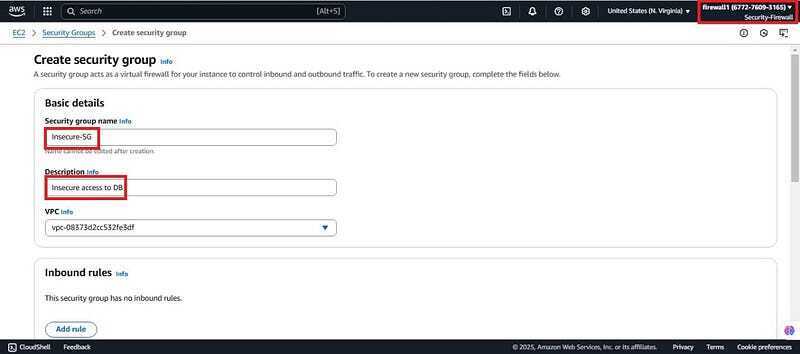
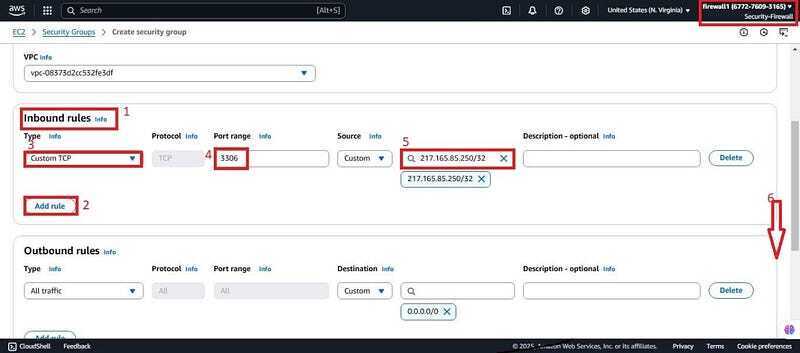
- Give it a name (Insecure-SG) , a description and scroll down to inbound rules.
- For inbound rules, click on add rule and add port 3306 for MySQL DB. For IP address put any public IP (215.165.85.250/32). Since databases are not allowed to be accessible by public addresses this will be insecure SG and want FWM to detect this insecure access. Scroll down and click to create SG.
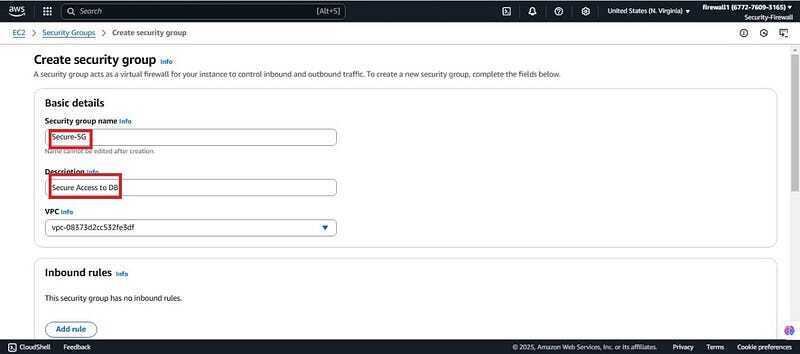
- Need to create another security group which is the secure SG for this demo (Secure-SG). Click on create security SG.
- Give it a name (Secure-SG), description and scroll down to inbound rules.
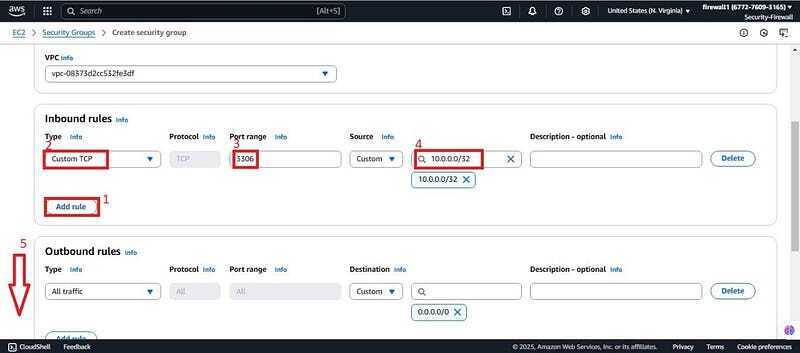
- Click on add rule, type “3306" for port and a private IP address"10.0.0.0/32", Which will be the secure SG. Scroll down and click create SG
CREATING EC2 INSTANCE.
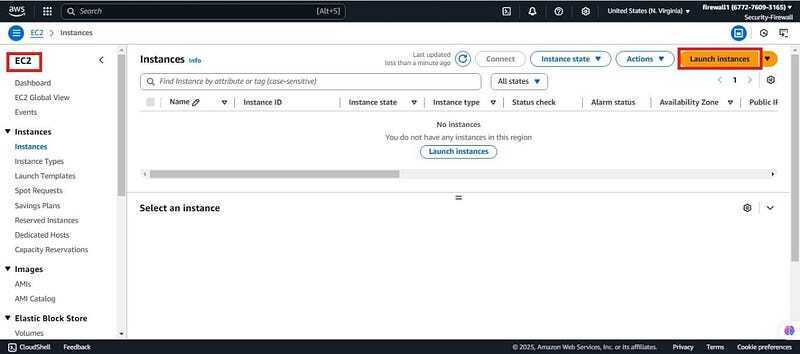
- We need two ec2 instances to attach to the insecure and secure SG to test if the firewall manager is going to detect them. Navigate to the EC2 console and click on launch instances.
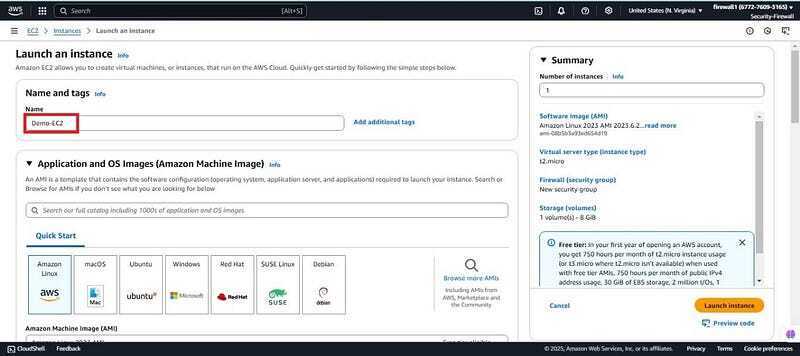
- Give it a name (Demo-EC2) scroll down and keep everything as default.
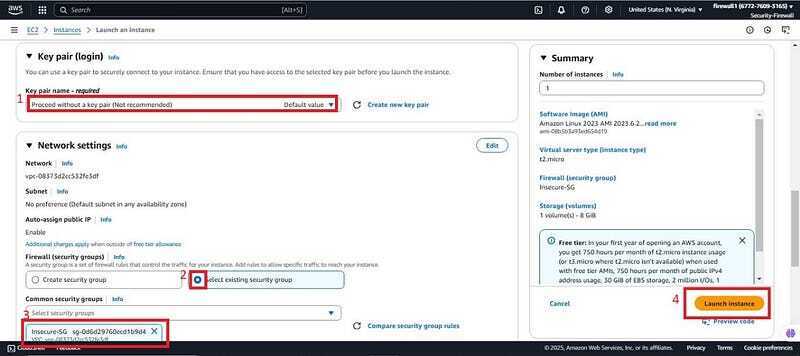
- Proceed without a key pair, Check ✅ on the select existing Security group and attach the insecure SG created above (Insecure-SG). Scroll down and click on the launch instance.
- Create the second instance which will be the secure ec2. Click on the launch instance.
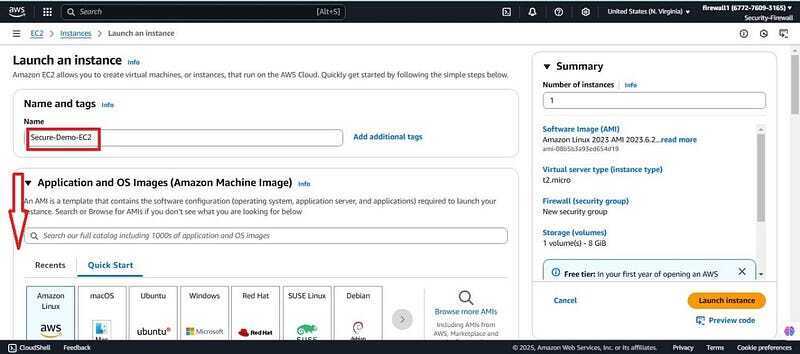
- Give it a name (Secure-Demo-EC2) and scroll down.
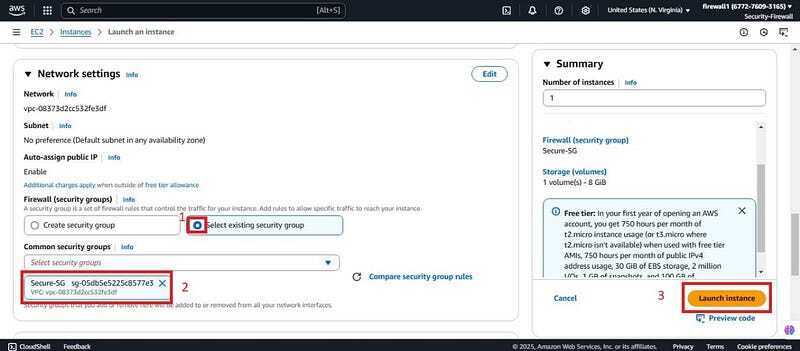
- Proceed without a key pair, click on select existing Security group and attach the secure security group (secure-SG). Scroll down and click the launch instance.
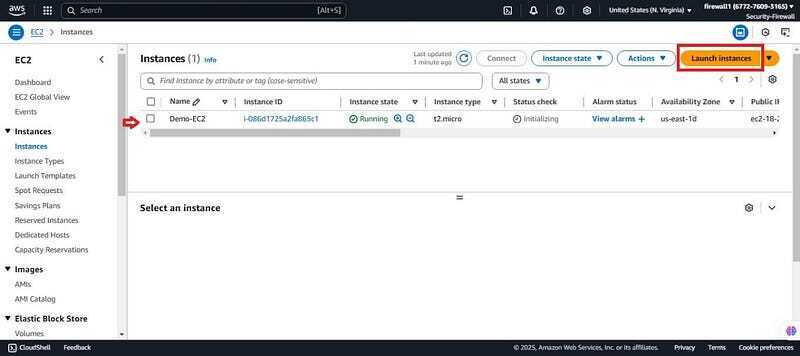
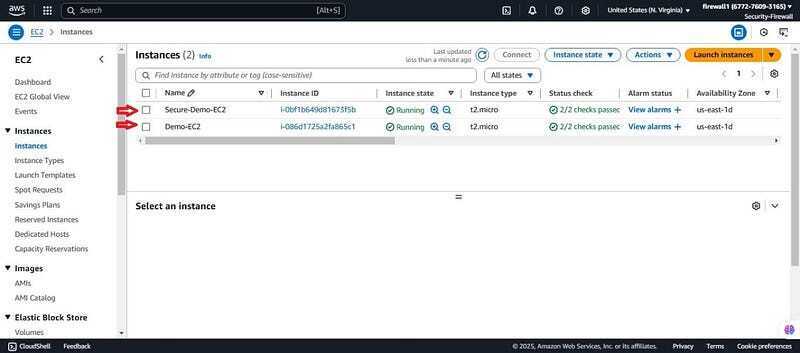
- You should now have two ec2 instances. One which is secure and one insecure instance.
Setting up an Ideal(most secure to follow) security group in the management account(Josephndambombi), the firewall manager will evaluate security groups in member accounts(firewall1) based on the Ideal SG.
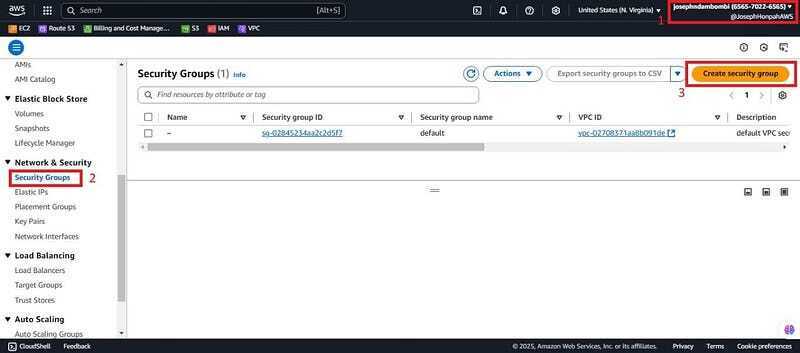
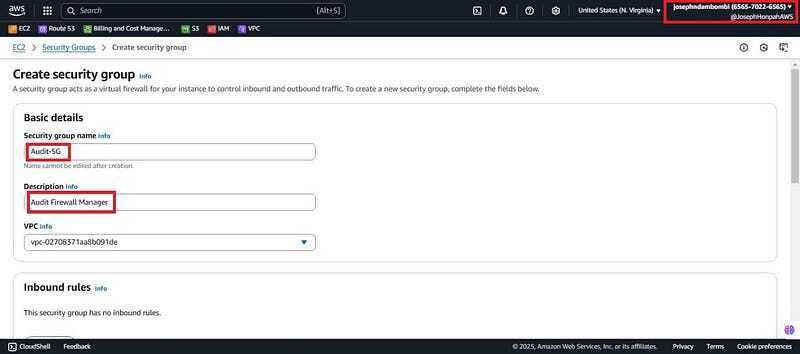
- Back on management account (Josephndambombi “accountID: xxxxxxxx6565") navigate to EC2, scroll down to security group and click create security group.
- Give it a name (Audit-SG), a description and scroll down to inbound rules.
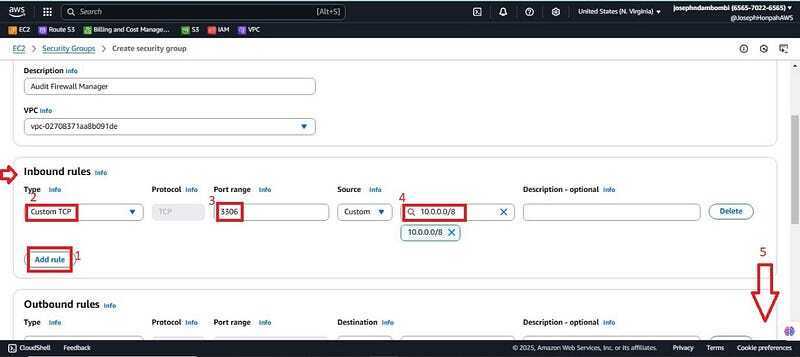
- Click on the add rule, port 3306 and on the source IP attach the entire CIDR range for private IP ranges (10.0.0.0/8), which will not allow any public IP range. Scroll down and click on create security group.
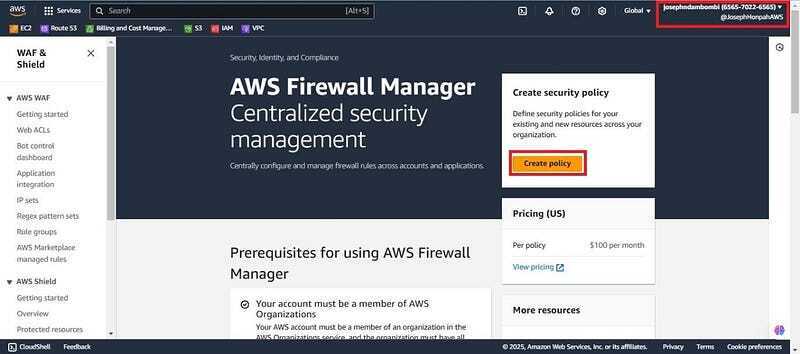
- Navigate to the firewall manager on the management account (Josephndambombi), click on security policies and click on the create policy.
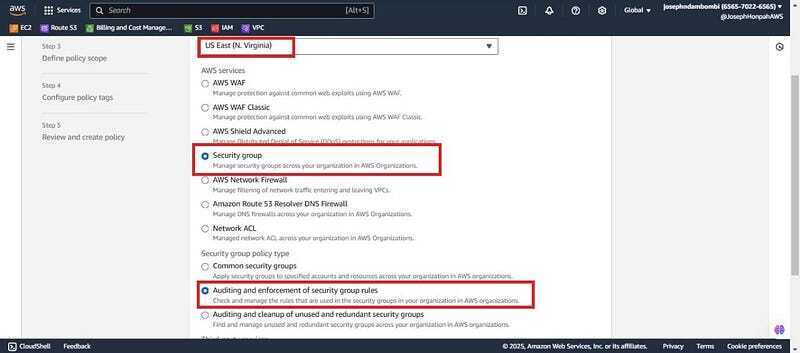
- Keep in mind the region your using to create these resources in management account and in member account (firewall1). Select region “US East(N.Virginia)” , under policy details since we are auditing SG you check on the security group. Check ✅ on Auditing and enforcement of security group rules, Click next.
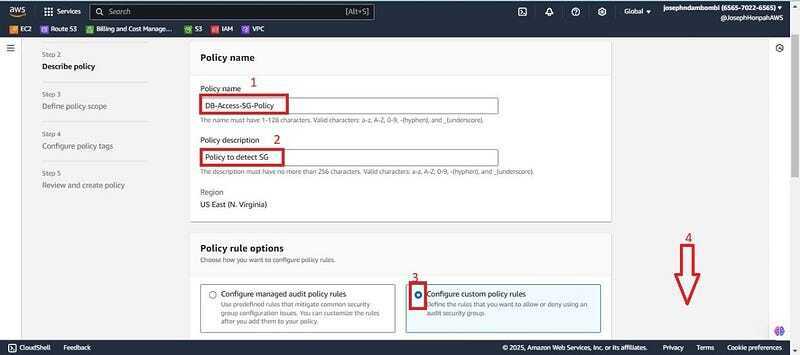
- Give a policy name(DB-Access-SG-Policy), give a description. Check on configure custom policy rules and scroll down.
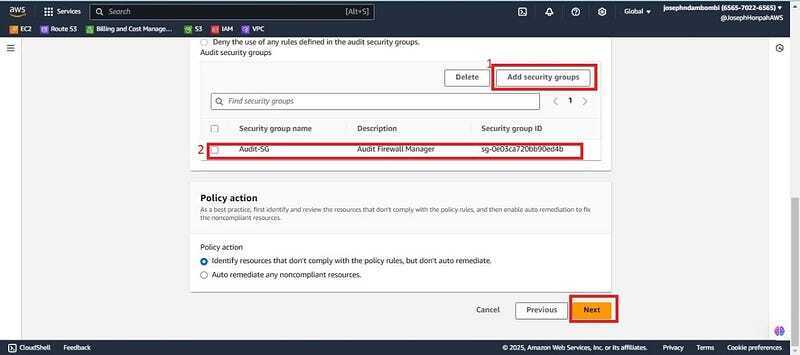
- In the custom rule, click Add security groups and select the Ideal SG (Audit-SG) which you created for the firewall manager to use, Click next.
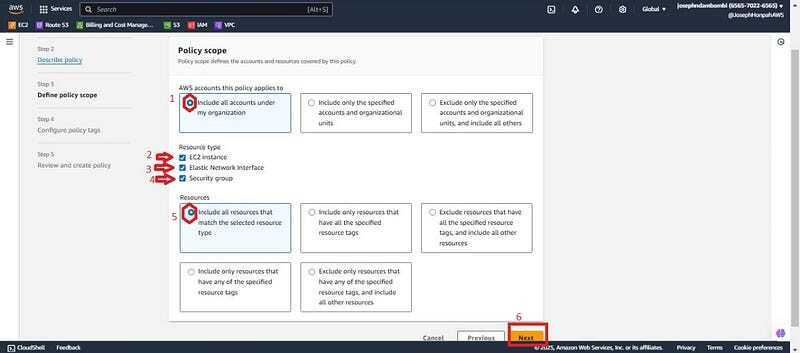
- Check ✅ Include all accounts under my organization, select all resource type and resources check ✅ Include all resources that match the selected resource type. Click next
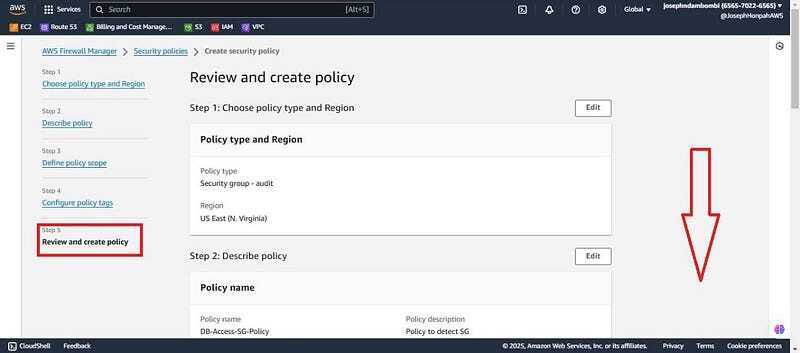
- Keep policy tags as default and click next
- Review details, scroll down and click create policy.
2️⃣STEP 2: Testing if firewall manager can detect these secure and insecure SG, instances and eni which are attached to the instances upon creation.
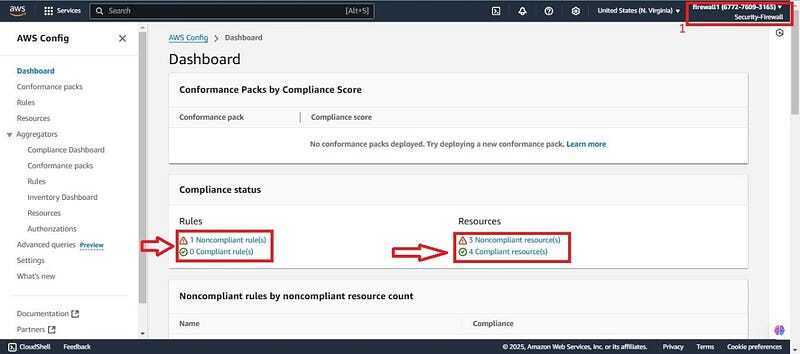
- First switching to the member account (firewall1), navigate to AWS config you should see 3 complaint and 3 non-complaint resources. Which are the secure and insecure resources created at the beginning of this demo.
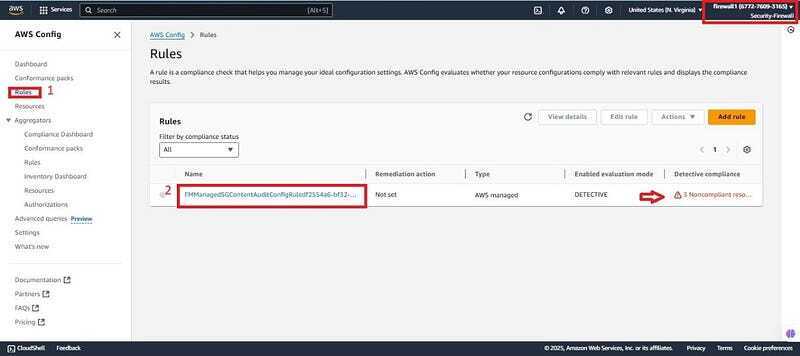
- click on Rules and you should see Firewall manager has created a configuration to detect non compliant resources.
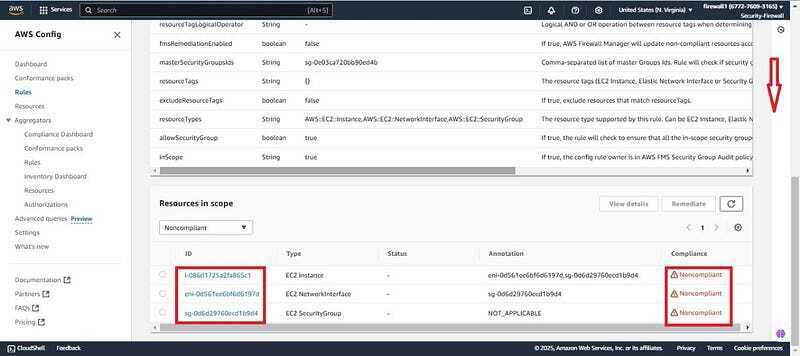
- Click on the created rule and you will see the three resources which were created early in this Demo to detect insecure resources. That is the Insecure-SG, Demo-EC2 and the Eni attached to the EC2 instance as non-compliant. Indicating it works properly.
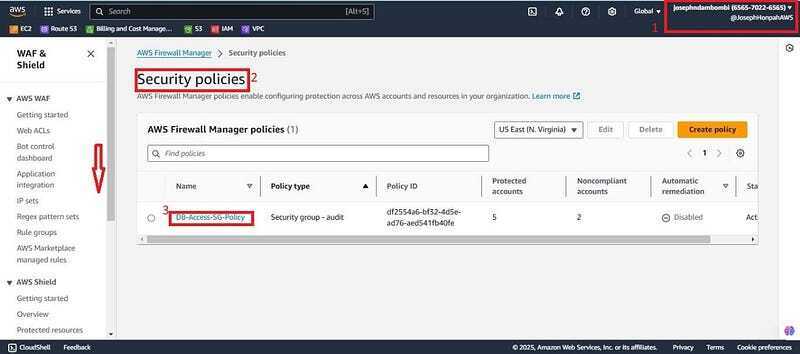
- Login to the management account (Josephndambombi) to check what Firewall Manager has found as complaint and non compliant in the AWS organization. Click on security policies (DB-Access-SG-Policy).
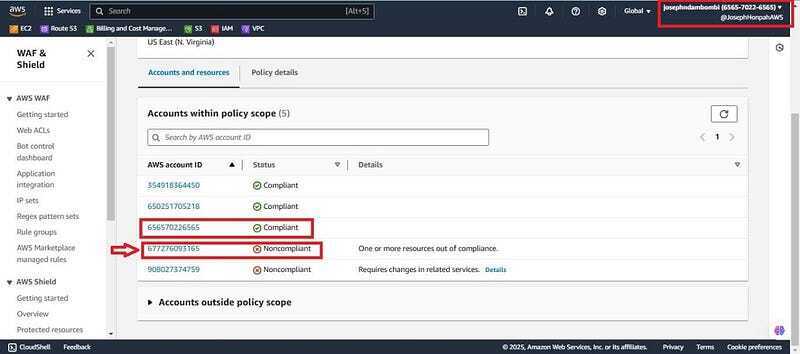
- You will find the management account (Josephndambombi “xxxxxxxx6565") to be complaint and the member account (firewall1 “xxxxxxxx3165") to be non-compliant due to 3 insecure resources in the member account. Click on the member account.
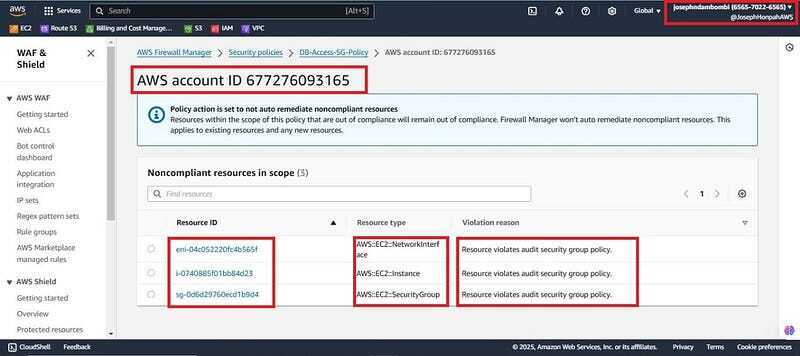
- You will find the same insecure resources which were created above( Demo-EC2, Insecure-SG and the Eni of the instance). And under validation reason you will see it violates the audit security group policy created earlier.
To solve this just enable auto-remediation in the firewall manager or you login to the member account and edit the inbound rules of the insecure-SG to have a private source IP range.
Do not forget to clean up resources first by terminating the EC2 instances, deleting SGs and delete firewall policy
Hurray 🎉 and we just used config and firewall manager to track complaint and non-complaint resources in AWS organizations.
Best Practices
- Start in Audit Mode before enabling remediation to understand the impact.
- Tag your resources to simplify policy scoping.
- Enable AWS Config Aggregators to get a unified view across regions and accounts.
- Use AWS Security Hub to aggregate and prioritize security findings.
Conclusion
AWS Firewall Manager makes it easier to manage and audit security groups across multiple accounts in AWS Organizations. By following this guide, you can ensure your security groups adhere to best practices and reduce the risk of misconfiguration.
If you found this post helpful or have questions about AWS security management, feel free to comment below! 👇🏾 And please like and share for more contents like this 💗
AWS #AWSCommuintyBuilder #Letslearn #Security
By Joseph Ndambombi Honpah on March 20, 2025.
Exported from Medium on March 21, 2025.


Top comments (0)