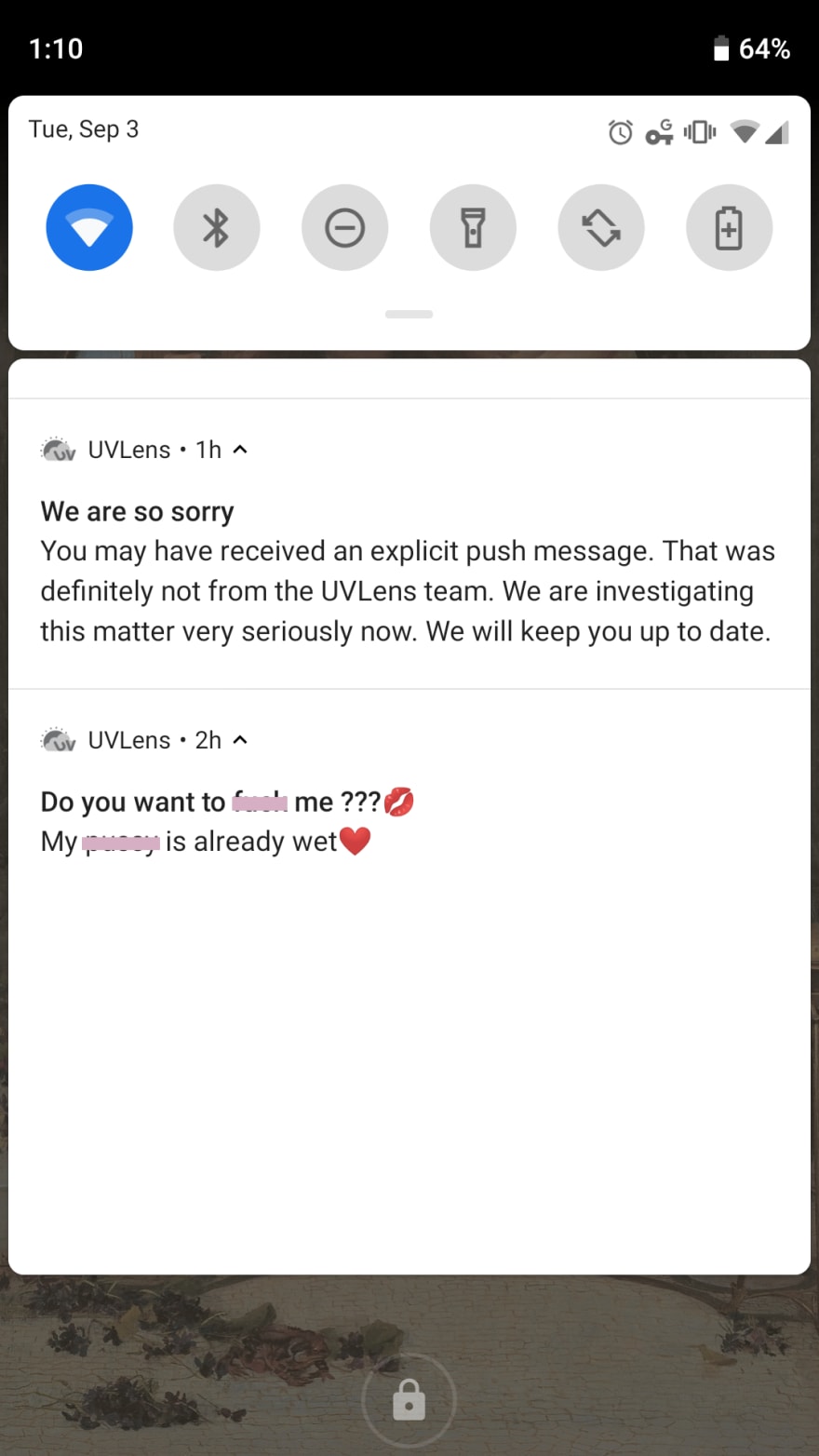
On September 3, 2019, I looked at my phone to find a surprising notification:
The message was sent from UVLens, a niche app with a small user base. Typically, UVLens displays the current UV Index in your region and provides recommendations on sun protection for your skin type. As a Very Pale Person, this has been a really useful way for me to decide if I need to wear sunscreen (yes) and a hat (most likely) when I go out of the house (rarely). It has never sent me a push notification before, and certainly never one so salacious.
UVLens followed up quickly with an apology via push notification and explained on social media that their “3rd party push notification service [had] been compromised.”
This message piqued my curiosity much more than the former. What is a push service and how can it be compromised?
Push Service
A push service is a company that manages an API that applications use to automate messaging their users. They provide easy ways to query for groups of users based on their data, such as time of last login, whether they’ve made a purchase through the app, or device type (iOS, Android, Chrome, etc.).
I reached out to UVLens about their service provider, and they said that they used OneSignal when the offending notification was sent, but they have since switched to the Google-run Firebase Cloud Messaging. According to OneSignal, they are used by companies like Verizon, Virgin Mobile, and HQ.
Push Notifications
Push Notifications are a topic unto themselves, but in short, it is a three-way conversation between an application’s server, the push service, and the user.
- A user downloads your app and agrees to receive push notifications.
- Your app’s server receives that information and...
- passes it to your push service.
- The push service responds with a unique ID for that user.
- When you’re ready to send a message, you query the push service’s API for the user id’s that you need, then pass the information to the push service.
- The push service sends the message to users you indicated.
In order for the push notifications to go through, you typically need two passwords that the push service provides: your application’s ID and an API Rest Key.
How Push Service Can Be Compromised
OneSignal has not made any public statements on the event or how this could happen. However, their API documentation provides clues on simple methods someone could use to access an application’s data.
First, the codes used to query the API are readily available, including instructions to quickly download a CVS file of all your user information. You do need the two authentication keys, though.
However, in researching this topic, I found that many people had actually posted their keys online. Usually, they only gave the REST API Key or the application ID, but a few gave both. (One programmer even posted an image of his user’s IDs.) Using that information, hypothetically, one would be able to download the application’s user information CVS. Hypothetically.
Of course, there are other ways in which passwords become open to the public, but this is a unique instance where user error is leading to compromised data.
The Vulnerability of Small Applications
If this is the method that was used to send the rogue notification, then UVLens was already particularly vulnerable. OneSignal has a simple query that will download all of an app’s user information if they have fewer than 100,000 users.
It’s impossible to know how many downloads an app has, but we can use a general estimate based on ratings. If we assume that a free app, like UVLens, will receive one rating for every 100 downloads, they likely have a total user base of about 88,000.
| Platform | Reviews | Estimated Downloads |
|---|---|---|
| Apple Store | 170 | 17,000 |
| Play Store | 713 | 71,300 |
| Total | 883 | 88,300 |
It’s possible that all of their users’ information was downloaded with one command in the terminal.
UVLens says that their data and servers were not compromised and that users’ information is safe. Luckily for them, the most personal information users input is their skin tone and zip code, so even if that data was released, it’s unlikely to have far-reaching effects.


Top comments (0)